Thesaurus is one of the most well-known platforms, with 5 million monthly visitors, and is regularly used by students, writers, and everyone else who want to enhance their vocabulary and linguistic talents.
Researchers in cybersecurity at Group-IB have recently discovered a cryptojacking technique on a well-known thesaurus website. This plan infects site users with malware to mine bitcoin and may also install other malicious software.
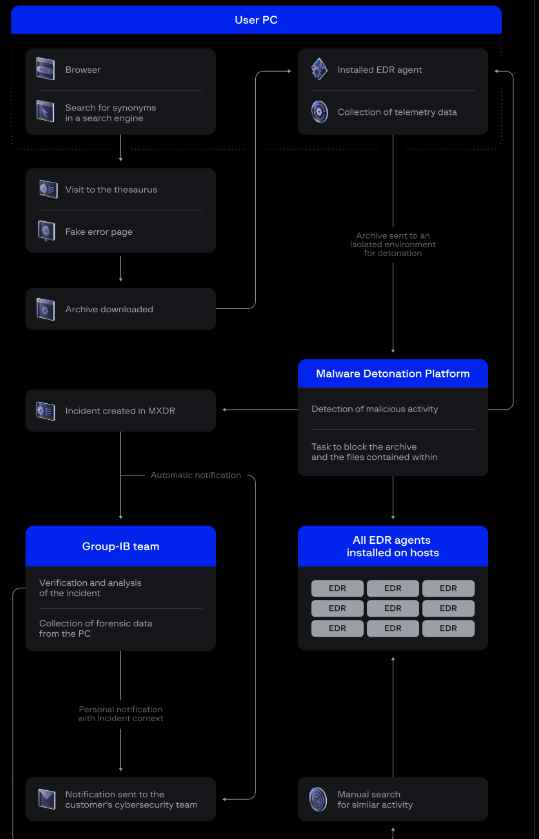
24/7 monitoring by Group-IB found harmful archives that were identified by Group-IB MXDR, which revealed an increase in malware across various client firms with strange archive names such as “chromium-patch-nightly.00.[0-9]3.[0-9]3.zip.”
The similarities, on the other hand, pointed to a common origin and an unusual method of attack.
The Campaign of Cryptojacking
The harmful archives were sent to the Malware Detonation Platform managed by Group-IB, where they were subjected to in-depth examination under a protected virtual setting. The files included a dropper that installed XMRig Coinminer, which is used in the mining of the Monero cryptocurrency, which is well-known for the privacy capabilities it provides.
The analysts utilized the EDR module of MXDR to narrow down the source of the package, and they found that it was downloaded to the Downloads folder on the workstations that were impacted. Specialists evaluated the browser history and extracted artifacts in order to track out the origin of the malicious sample. This was done since the Downloads folder is often used for downloading files. Analysts discovered a cunning infection chain in which going to a website for a thesaurus resulted in the automated downloading of malicious archive files. It’s interesting to see that the mischief skipped over the antonyms part.
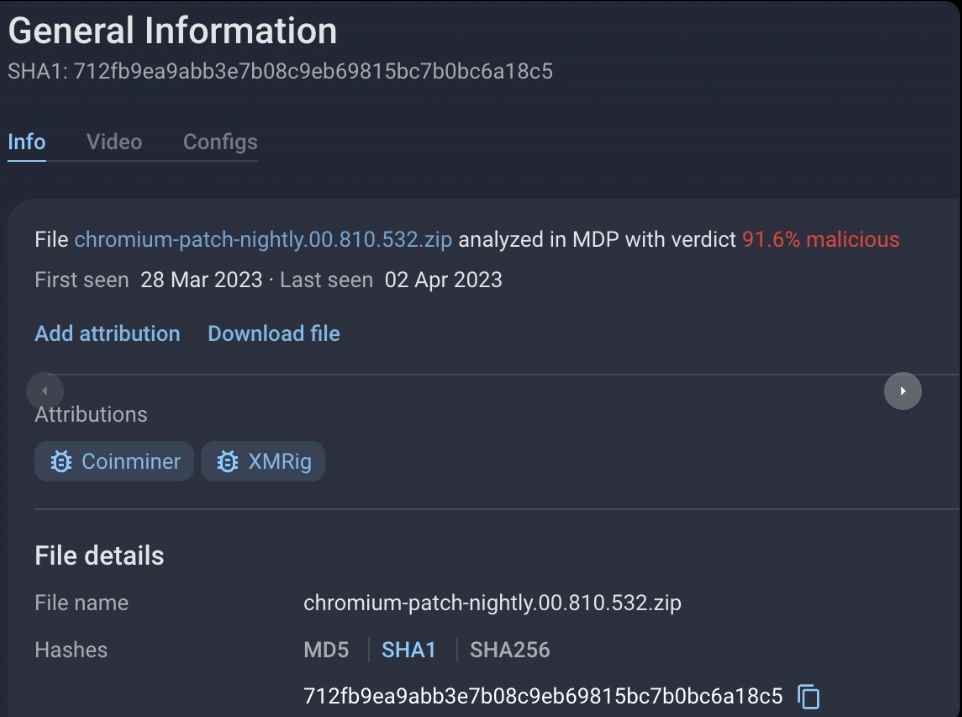
After doing the analysis, they used Header to look for evidence of dropper activity.ImageFileName filter, which discovered traces but did not uncover the actual launch.
This group discovered that there were no host launches for the downloaded dropper and immediately notified customers. In the incident comments part of the MXDR system, the company provided consumers with context and preventative advice.
After receiving confirmation from the Malware Detonation Platform, the danger posed by the archived file is immediately rendered harmless, and the EDR agent immediately blocks and quarantines hazardous files. It also distributes the hashes of dangerous files, which may have an effect on other customers’ blocklists even if those customers have never received the item in question.
The widespread belief that well-known websites are risk-free was debunked when it was discovered that a miner had been operating on one of them. Threat actors used a number of tried-and-true methods, including as drive-by downloads and social engineering via the deployment of a phony error page.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
