Two malicious VSCode Marketplace extensions were found deploying in-development ransomware, exposing critical gaps in Microsoft’s review process.
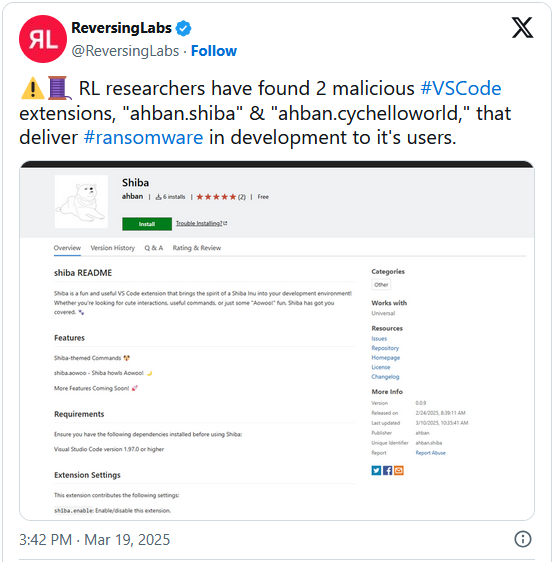
The extensions, named “ahban.shiba” and “ahban.cychelloworld,” were downloaded seven and eight times, respectively, before they were eventually removed from the store.
It is notable that the extensions were uploaded onto the VSCode Marketplace on October 27, 2024 (ahban.cychelloworld) and February 17, 2025 (ahban.shiba), bypassing safety review processes and remaining on Microsoft’s store for an extensive period of time.
The VSCode Marketplace is an online platform where developers can find, install, and share extensions for Visual Studio Code (VSCode). It is widely used by software and web developers, data scientists, and programmers.
ReversingLabs discovered that the two extensions contain a PowerShell command that downloads and executes another PS script that acts as ransomware from a remote server hosted on Amazon AWS.
The ransomware is clearly in development or a test as it only encrypts files in the C:users%username%DesktoptestShiba folder and does not touch any other files.
When done encrypting the files, the script will display a Windows alert stating, “Your files have been encrypted. Pay 1 ShibaCoin to ShibaWallet to recover them.” No ransom notes or further instructions are given like normal ransomware attacks.
.jpg)
Source: ReversingLabs
ReversingLabs states that Microsoft quickly removed the two extensions from the VSCode Marketplace after the researchers reported them.
However, ExtensionTotal security researcher Italy Kruk told BleepingComputer that their automated scanner caught the extensions earlier and informed Microsoft a while back, receiving no response.
Kruk explains that ahban.cychelloworld wasn’t malicious in its initial upload. It added the ransomware code in its second submission, version 0.0.2, which was accepted on the VSCode Marketplace on November 24, 2024.
“We reported ahban.cychelloworld to Microsoft on November 25, 2024, via an automatic report generated by our scanner,” Kruk told BleepingComputer.
“It is possible that due to the low number of installs for the offending extension, Microsoft didn’t prioritize its review.”
Since then, the ahban.cychelloworld extension had another five releases, all containing the malicious code and all being accepted in Microsoft’s store.
The fact that the extensions downloaded and executed remote PowerShell scripts, and could stay undetected for almost four months demonstrates a concerning gap in Microsoft’s review process.
Although in this case, Microsoft failed to react for months, the company has done the opposite recently, removing VSCode themes used by 9 million users too quickly after it got reported for suspicious obfuscated code.
While VSCode themes should not be using obfuscated JavaScript, the Material Theme – Free’ and ‘Material Theme Icons – Free’ extensions were later proven not to be malicious.
Microsoft apologized for the unjustified removal and banning of their publisher and said they would update their “scanners and investigation process to reduce the likelihood of another event like this.”

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
