Hidden vulnerabilities in legacy code often create unseen risks for modern development environments.
One such issue recently surfaced within the Python ecosystem, where outdated bootstrap scripts associated with the zc.buildout tool expose users to domain takeover attacks.
These scripts, designed to automate the installation of package dependencies, contain hardcoded references to external domains that are no longer under the control of the original maintainers.
The core of the problem is a specific behavior in these scripts where they attempt to fetch the deprecated distribute package from python-distribute[.]org.
This domain has been abandoned since 2014 and is currently parked and available for purchase. If a threat actor were to acquire this domain, they could serve malicious payloads that would be automatically downloaded and executed by any developer running the compromised bootstrap script.
.webp)
This creates a direct path for supply chain attacks, bypassing standard security checks.
Reversinglabs security analysts identified this vulnerability, noting that it affects several well-known packages, including slapos.core, pypiserver, and tornado.
Although many developers have transitioned to newer packaging standards, these legacy files often persist in repositories.
The vulnerability is not triggered during a standard pip install but typically requires manual execution or invocation through a build process like a Makefile.
Once activated, the script blindly trusts the external source, creating a significant supply chain risk similar to the fsevents incident in the npm registry.
Analyzing the Execution Mechanism
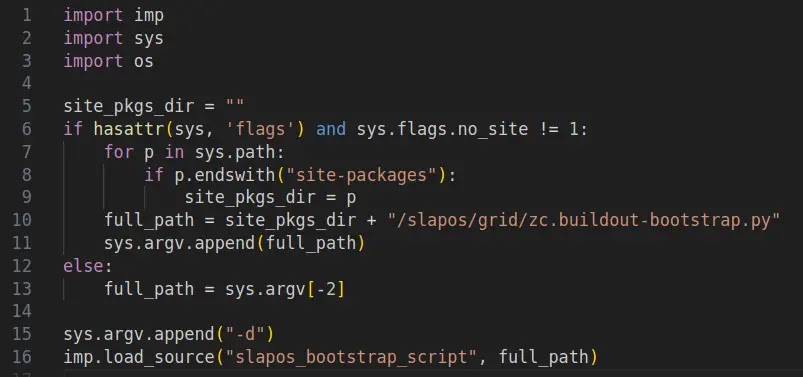
The technical core of this vulnerability lies in the insecure way the bootstrap script handles dependency resolution. The code logic specifically checks for the presence of the distribution package.
.webp)
If it is not found, the script initiates a download routine using Python’s built-in urllib libraries. As illustrated in the figure above, the distributed setup is fetched and executed in bootstrap.py; the script explicitly requests content from the now-defunct python-distribute[.]org.
Crucially, the response from this URL is passed directly to an exec() function, which runs the code immediately without any integrity checks or signature verification.
.webp)
To validate this vector, researchers crafted a proof-of-concept exploit targeting slapos.core. The Proof-of-concept script exploits the vulnerability in slapos.core, the PoC works by manipulating command-line arguments to force the script into its vulnerable download path.
The result of the terminal output after running the PoC script confirms that the script successfully connects to the external domain, proving that any code hosted there would run with the user’s full privileges.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.
