The Water Saci campaign targeting Brazilian users has escalated significantly, with threat actors demonstrating remarkable technical sophistication by employing artificial intelligence to enhance their malware propagation capabilities.
Security researchers have identified a critical shift in the group’s attack methodology: the transition from PowerShell-based scripts to Python variants.
This transformation has been accelerated through the use of large language models and AI code-conversion tools.
The campaign employs an exceptionally complex attack chain designed to evade conventional detection mechanisms.
Victims receive seemingly innocuous messages through WhatsApp containing multiple file formats including HTML Application (HTA) files, ZIP archives, and PDF documents each serving as an entry point into a sophisticated infection sequence.
The diversity of attack vectors significantly complicates analysis and increases the likelihood of successful compromise.
The initial infection typically begins when users execute malicious HTA files downloaded directly from WhatsApp Web.
These files contain embedded Visual Basic scripts protected by multiple obfuscation layers, designed to evade both security software and manual analysis.
Once deobfuscated, the scripts initiate contact with command-and-control servers to download MSI installers and automation components that establish banking trojans on compromised systems.
AI-Powered Script Conversion
Perhaps most notable is evidence suggesting that attackers leveraged large language models to convert their existing PowerShell propagation routine into a more versatile Python implementation.
The script launches the AutoIt interpreter (DaXGkoD7.exe) to run the compiled AutoIt script.
The Python variant, designated whatsz.py, maintains functional equivalence with its PowerShell predecessor while introducing substantial improvements in capability and reach.
Examination of the Python code reveals explicit comments stating the script was “converted from PowerShell to Python with support for Chrome, Edge and Firefox.”
A helper function translates language codes into readable names like Portuguese (Portugal), English (US), or Spanish (Spain).
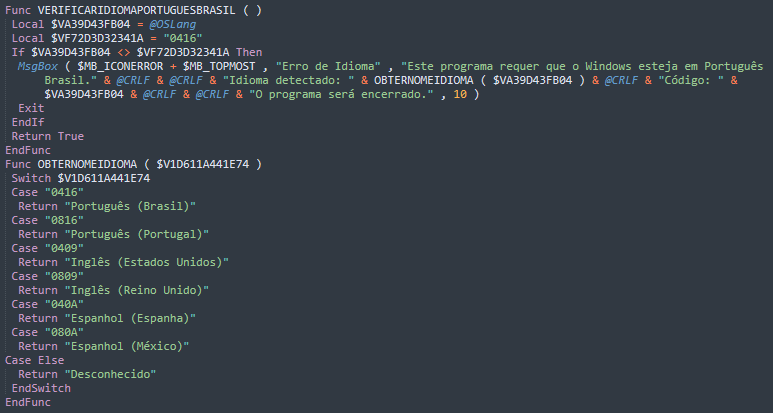
Additionally, the code includes optimization notes suggesting AI involvement, such as “send message to a contact – version optimized with error handling” and “send message to multiple contacts at same time – super fast!”
These annotations are atypical of manually written malware and strongly indicate AI-assisted development.
The Python variant represents not merely a straightforward translation but a significant operational upgrade.
The new implementation adds object-oriented code structure, enhanced error handling, batch messaging capabilities, and multi-browser compatibility features that substantially accelerate malware distribution while improving resilience against detection and failure.
The payload uses the same IMAP-based technique previously documented in our recent analysis of the Water Saci campaign.
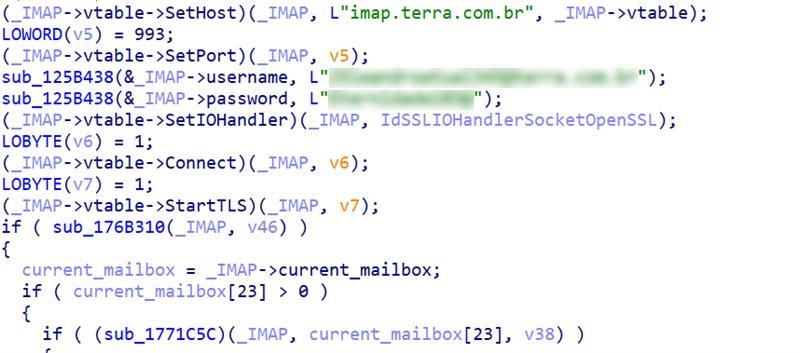
The automation script harnesses Selenium to manipulate WhatsApp Web interfaces, inject malicious JavaScript libraries, extract contact lists, and execute mass file transmission using Base64 encoding.
These capabilities enable threat actors to rapidly propagate malware across victim networks with minimal manual intervention.
Banking Trojan Sophistication
The ultimate payload delivered through this chain is a sophisticated banking trojan that targets explicitly Brazilian financial institutions and cryptocurrency exchanges.
The malware performs comprehensive reconnaissance, detecting installed banking applications, analyzing Chrome browser history for financial websites, and monitoring for antivirus software.
The extensive use of Python in this stage enables the attackers to automate propagation, streamline payload delivery, and enhance the flexibility and resilience of their malicious operations.

Upon identifying banking-related window activity, the trojan injects credentials-stealing overlays and maintains persistent access through process hollowing techniques.
The Water Saci campaign represents a paradigm shift in cybercriminal operations, demonstrating how threat actors are adopting AI technologies to accelerate development cycles and enhance operational effectiveness.
The integration of AI-assisted code conversion, multi-stage delivery mechanisms, and advanced persistence techniques creates a formidable threat landscape for Brazilian users and organizations.
Security experts emphasize the necessity of implementing multi-layered defenses, including disabled auto-downloads in messaging applications, advanced endpoint protection, and comprehensive user awareness training.
As adversaries continue innovating with AI-enhanced capabilities, organizations must maintain vigilant monitoring and rapidly adapt their defensive postures accordingly.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
