A coordinated reconnaissance campaign targeting Citrix NetScaler infrastructure over the past week used tens of thousands of residential proxies to discover login panels.
The activity was observed between January 28 and February 2, and it also focused on enumerating versions of the product, indicating an organized discovery effort.
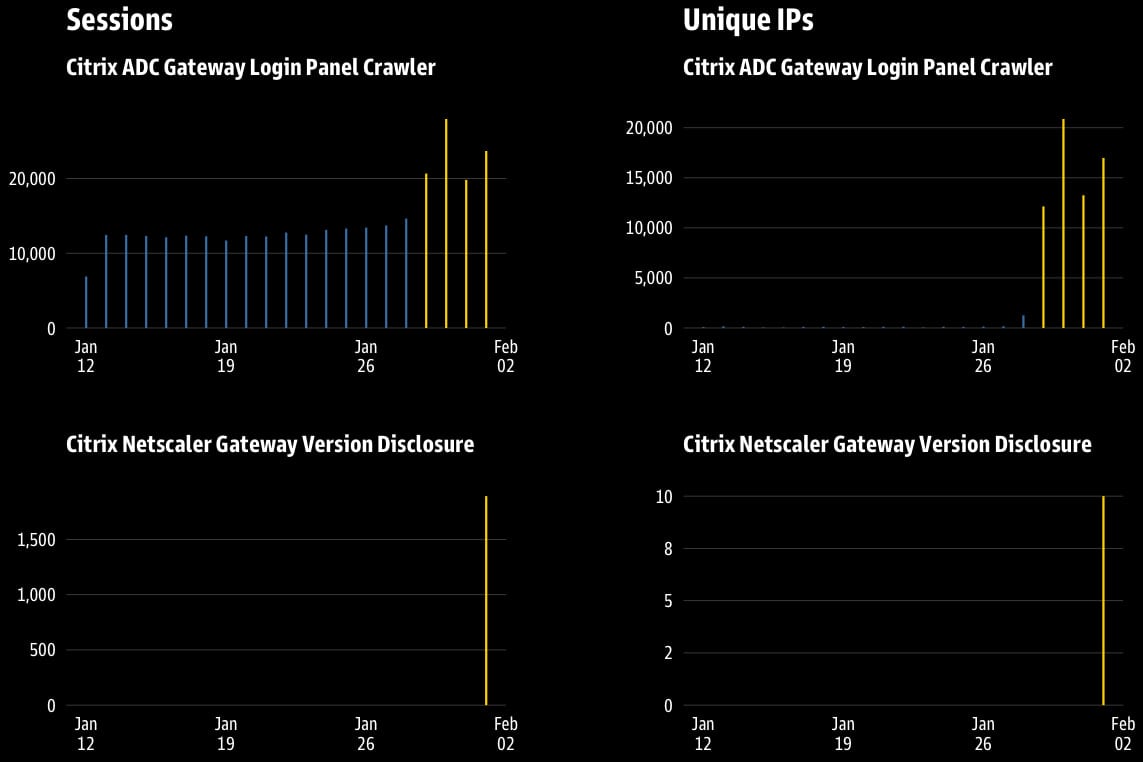
Threat monitoring platform GreyNoise traced the source of the scanning traffic to more than 63,000 distinct IPs that launched 111,834 sessions. According to the researchers, 79% of the traffic was aimed at Citrix Gateway honeypots.

Roughly 64% of the traffic came from residential proxies, with IPs spread across the globe, appearing as legitimate consumer ISP addresses and bypassing reputation-based filtering. The remaining 36% came from a single Azure IP address.
The activity strongly indicates pre-exploitation infrastructure mapping, rather than random internet scanning, GreyNoise says.
“The specific targeting of the EPA [Endpoint Analysis] setup file path suggests interest in version-specific exploit development or vulnerability validation against known Citrix ADC weaknesses.”
Source: GreyNoise
The two indicators of malicious intent are obvious, with the most active one generating 109,942 sessions from 63,189 unique IPs and targeting the authentication interface at ‘/logon/LogonPoint/index.html’ to identify exposed Citrix login panels at scale.
The second indicator, observed on February 1st, was a six-hour sprint with 10 IPs launching 1,892 sessions focused on the URL path ‘/epa/scripts/win/nsepa_setup.exe’ to enumerate Citrix versions via EPA artifacts.
GreyNoise notes that the attacker employed a user agent for Chrome 50, released in early 2016. Targeting the EPA setup file may indicate an “interest in version-specific exploit development or vulnerability validation against known Citrix ADC weaknesses.”
“The rapid onset and completion suggest a targeted scanning sprint that may have been triggered by discovery of vulnerable EPA configurations or intelligence about deployment windows,” GreyNoise says.
The most recent critical-severity flaws impacting Citrix products are CVE-2025-5777, aka ‘CitrixBleed 2,’ and CVE-2025-5775, a remote code execution vulnerability that was exploited as a zero-day.
GreyNoise lists several detection opportunities for this latest activity, including:
- Monitoring for the blackbox-exporter user agent originating from non-authorized sources
- Alerting on external access to /epa/scripts/win/nsepa_setup.exe
- Flagging rapid enumeration of /logon/LogonPoint/ paths
- Watching for HEAD requests against Citrix Gateway endpoints
- Tracking outdated browser fingerprints, specifically Chrome 50 (circa 2016)
Additionally, the researchers recommend that system administrators review the necessity of internet-facing Citrix Gateways, restrict access to the /epa/scripts/ directory, disable version disclosure in HTTP responses, and monitor for anomalous access from residential ISPs in unexpected regions.
GreyNoise has also shared the IP addresses used to launch the scanning activity.

Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
