Netskope Threat Labs has uncovered a malicious campaign exploiting fake software installers, including those mimicking popular tools like DeepSeek, Sogou, and WPS Office, to deliver dangerous malware payloads such as the Sainbox RAT (a variant of Gh0stRAT) and the Hidden rootkit.
This operation, primarily targeting Chinese-speaking users through phishing websites and counterfeit MSI installers, showcases advanced tactics, techniques, and procedures (TTPs) reminiscent of the China-based Silver Fox adversary group.
A Sophisticated Campaign Targeting Chinese Speakers
Netskope attributes this activity to Silver Fox with medium confidence, based on the use of phishing pages, fake installers for Chinese software, Gh0stRAT variants, and the specific targeting of this demographic.
The attack begins when victims visit phishing websites designed to mirror legitimate software portals, such as the WPS Office site, tricking users into downloading malicious installers.

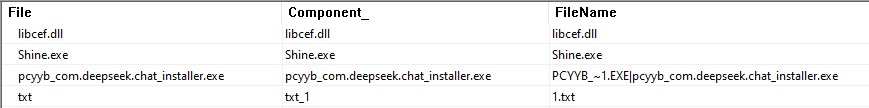
These installers, predominantly MSI files, execute a legitimate binary named “Shine.exe” to sideload a malicious DLL, “libcef.dll,” a counterfeit version of the Chromium Embedded Framework library.
Simultaneously, the genuine software installer runs to maintain the illusion of legitimacy.
Technical Breakdown of the Infection Chain
During execution, a file named “1.txt” is dropped, containing shellcode and a malware payload.
The shellcode, inspired by the open-source sRDI tool, facilitates reflective DLL injection by loading “Install.dll” into memory and invoking its exported “Shellex” function, initiating the malicious payload.
The payload, identified as Sainbox RAT, grants attackers full control over the victim’s system, enabling data theft and further payload deployment.
Embedded within its .data section is a rootkit driver based on the open-source Hidden project, which the RAT installs as a service named “Sainbox” using NtLoadDriver.
This rootkit employs mini-filters and kernel callbacks to hide processes, files, and registry entries, while also protecting itself and specific processes from termination.
Persistence is achieved by setting the path of “Shine.exe” to the Windows registry Run key under the name “Management,” ensuring the malware reactivates on system reboot.
The combination of Sainbox RAT and Hidden rootkit provides both control and stealth, evading detection by security tools.
This campaign highlights the exploitation of AI software popularity, with phishing sites acting as bait and legitimate installers masking malicious activity.
The reliance on commodity malware like Gh0stRAT variants and open-source rootkits like Hidden demonstrates the attackers’ strategy of leveraging existing tools for efficiency.
According to the Report, Netskope Threat Labs continues to monitor the evolution of Sainbox RAT and Silver Fox’s TTPs, noting the challenges in attribution due to shared tooling and potential false-flag operations.
With medium confidence, this activity aligns with Silver Fox’s known patterns, though ongoing research may refine these insights as new evidence emerges.
Indicators of Compromise (IOCs)
| Type | Value | Description |
|---|---|---|
| File Name | Shine.exe | Legitimate file used for DLL sideloading |
| File Name | libcef.dll | Malicious DLL payload |
| File Name | 1.txt | File containing shellcode and malware |
| Registry Key | Management | Run key for persistence |
| Service Name | Sainbox | Rootkit service name |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
