A Dictionary attack is one of the ways through which the attackers try to gain access to the keys of the reign. Bad actors take advantage of people using common dictionary words as their passwords.
A study has proved that the majority of people like to reuse their passwords or use common phrases that are relatively easy to remember.
Databases used in dictionary attack does not only include the common dictionary words, but also the passwords leaked in previous attacks.
BurpSuite is indeed a great tool for testing vulnerabilities in web applications. We are here using its free version which has limited capabilities but works well for learning! Let’s begin the process to brute force/dictionary attack.

So, we’ll be using VM setup, with Kali and Bee-Box as a Web Server which is the victim. The process for setting up the Burp Suite and proxy in the browser is explained here. Make sure you have set up your proxy to your local host.
STEP1: Intercepting the Login Request
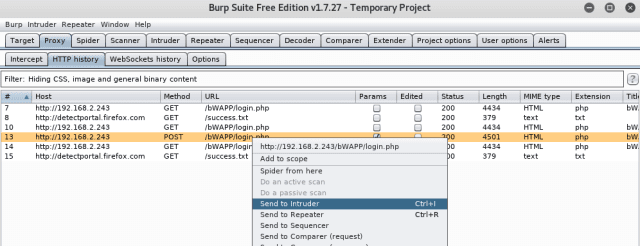
To capture the HTTP request, try entering the username and password on the login form of Bee-Box. [With the Intercept ON] Once you hit the login button, Burp Suite will intercept the request and then forward the request or turn it off.
Now, right-click on the request and send it to the intruder.
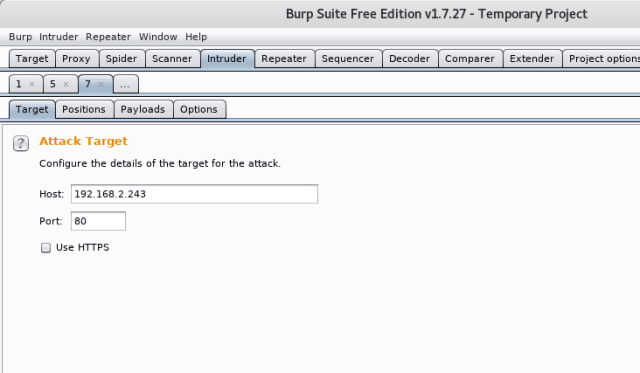
STEP2: Intruder
Once on your Intruder Tab, you will see the IP, and the port you want to attack gets to fill in automatically. In case, if you did not make the request (as in step 1), you can manually put the information here under the “target” tab.
Now turn to the “position” tab. This is the same request (or information of raw packet) that you made before. The highlights here are the “potential injection” points marked by the BurpSuite.
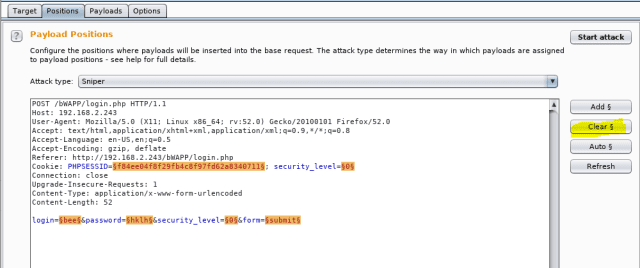
Here we know the username and just wanted to get through the password. For now, other things like sessionsIDs or security level or login are not required. Hit the “clear” as shown.
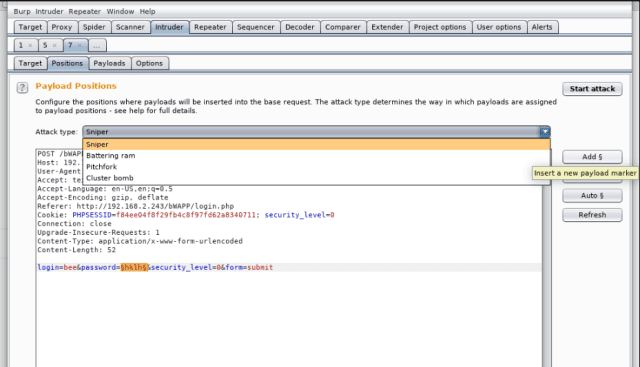
And then highlight the parameter “password” and click Add. You would be able to see those little markers around the “password”. This means, that we will be passing a list of letters, which will go through each of those and send a request to the server.
As only one parameter needs to be replaced, select the “Sniper” attack. Sniper attack uses only one payload set and replaces all the marked positions one by one.
If you are trying both for the username and password, then select “Cluster Bomb”. It puts the first payload at the first position, and the second at other, and uses all the possible combinations.
Now, we are going to go forward and set the payload. Since, we just working on finding the password, select 1. You can load the word list from Kali from the path- /usr/share/wordlists.
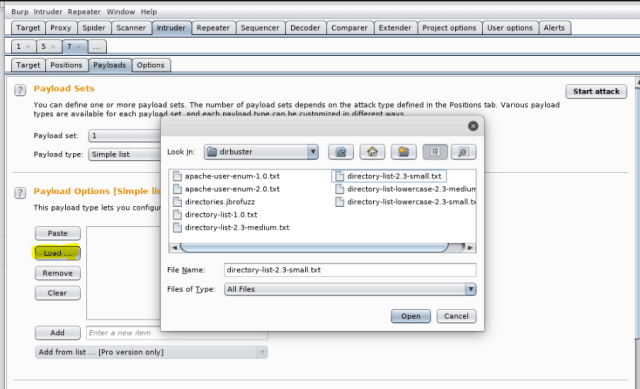
In here, I am manually adding the words, I want to test against the parameter password. And then hit “Start Attack”.
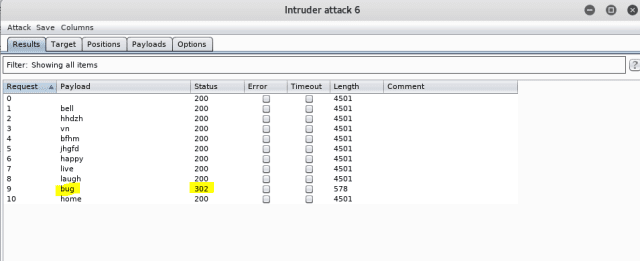
In the “result” window, you will notice that one word has different values for “length” and “status”. All others will have the same as the base request.
How To Protect Yourself Against Dictionary Attack:
Dictionary or brute force attacks are not only limited to online attacks, but also offline attacks. Some of the steps below are helpful for falling for these attacks:
- Locking account after a maximum number of authentication attempts is reached.
- Using multi-factor authentication to log in to your account.
- Insert special characters in your passwords and an extra syllable to guard it against the Dictionary attack. (eg. P@$$$word).
- Use a longer password with special characters and avoid reusing them. Use haveibeenpwned to look if your credentials have ever been leaked.
These are some of the steps, but not limited to these, which can strengthen the protection against these attacks.
Also Read
What is Phishing Attack? How it Works & How to Prevent Yourself?
What is Spoofing? How It Works and How to Prevent it
You can follow us on Linkedin, Twitter, and Facebook for daily Cyber Security and hacking news updates.