Cryptographic failures occur when the mechanisms and protocols designed to secure data and communications through encryption break down, become compromised, or fail to perform as expected.
These failures compromise the foundational principles of data security—confidentiality, integrity, and authenticity—and leave sensitive information vulnerable to unauthorized access, modification, or exploitation.
However, cryptographic failures can arise from flawed algorithms, poor implementation, weak key management, or insider threats, among other reasons.
When such failures occur, attackers can exploit vulnerabilities to breach systems, decrypt sensitive data, manipulate information, or impersonate users.
This article provides a detailed exploration of cryptographic failures, their causes, types, real-world examples, and strategies to prevent them.
Understanding Cryptographic Failures
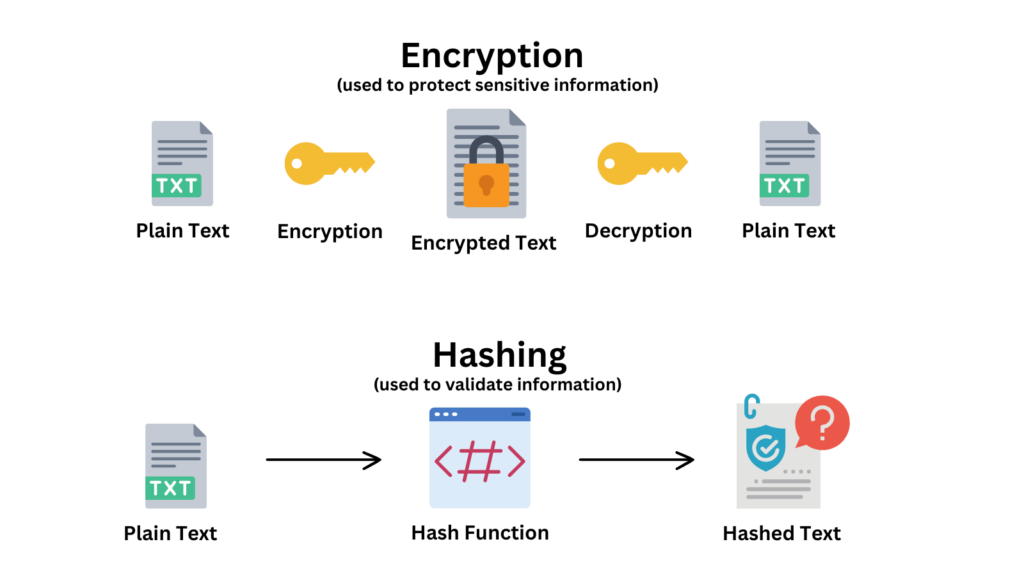
Cryptography involves the use of algorithms and mathematical principles to encode information, ensuring that only authorized parties can access or understand the data.
A cryptographic failure, therefore, is not simply a technical glitch; it represents a severe breakdown in the processes meant to protect information.
Key Principles of Cryptographic Security
- Confidentiality: Ensures that only authorized parties can access sensitive data.
- Integrity: Prevents unauthorized modification of data.
- Authenticity: Verifies the identity of users and ensures data comes from a trusted source.
When cryptographic systems fail, these principles are undermined, leaving data open to breaches, fraud, or exploitation
What Causes Cryptographic Failures?
Numerous factors contribute to cryptographic failures, including:
1. Weak or Outdated Encryption Algorithms
Encryption mechanisms evolve as computational power increases and new attack vectors emerge.
Algorithms deemed secure in the past, like DES or MD5, are now vulnerable to brute-force attacks or cryptographic collisions. Using such algorithms exposes sensitive data to unauthorized decryption.
2. Poor Key Management
Encryption keys are the linchpin of cryptographic systems. Failures in their generation, storage, distribution, or rotation can lead to compromises. Common issues include:
- Using predictable or weak keys.
- Storing keys in plaintext files.
- Failing to revoke or rotate keys after use.
3. Implementation Errors
Flaws in the application of encryption protocols often arise from insufficient testing, bugs, or misuse of cryptographic libraries. These errors weaken the system and open backdoors for attackers.
4. Insider Threats
Disgruntled employees or malicious insiders with access to cryptographic systems might intentionally leak, misuse, or tamper with encryption keys and protocols, compromising the system’s security.
5. Design Flaws
Poorly designed cryptographic systems may use insecure algorithms, inadequate key exchange protocols, or vulnerable implementations that attackers can exploit.
6. Side-Channel Attacks
Advanced attackers analyze physical or operational characteristics, such as power consumption, timing, or electromagnetic emissions, to infer cryptographic keys without directly breaking the algorithm.
7. Cryptographic Backdoors
Intentional vulnerabilities or backdoors inserted into cryptographic systems (e.g., by governments or malicious entities) can be exploited by attackers to decrypt sensitive data.
8. Inadequate Security Awareness
Users or developers with insufficient knowledge of cryptographic best practices may accidentally misconfigure encryption settings or fall victim to phishing or other social engineering tactics.
Types of Cryptographic Failures
1. Design Flaws
These are inherent vulnerabilities in the design of cryptographic systems, such as:
- Using weak algorithms.
- Choosing insecure key exchange protocols.
- Implementing cryptographic primitives incorrectly.
2. Implementation Errors
These occur during the deployment or development of cryptographic systems. Examples include:
- Weak random number generation.
- Unpatched vulnerabilities in cryptographic libraries.
- Coding errors that bypass encryption mechanisms.
3. Key Management Issues
Cryptographic failures are often tied to poor key management practices, including:
- Storing keys insecurely.
- Using common or predictable keys.
- Failing to update or rotate keys regularly.
Real-World Examples of Cryptographic Failures

1. Heartbleed Vulnerability (2014)
The Heartbleed bug in the OpenSSL library exposed sensitive data like private keys and login credentials. It underscored the importance of rigorous code review and timely patching in cryptographic implementations.
2. Dual EC DRBG (2007)
The NSA introduced a backdoored random number generator, Dual EC DRBG, which allowed attackers to predict encryption keys. This case highlighted the risks of using closed or government-influenced cryptographic standards.
3. WhatsApp Encryption Flaw (2017)
A vulnerability in WhatsApp’s end-to-end encryption allowed attackers to intercept and modify encrypted messages. This incident stressed the need for robust encryption protocols and extensive security testing.
How to Prevent Cryptographic Failures
1. Secure Protocol Design
Cryptographic protocols must be designed to address potential vulnerabilities and deliver robust guarantees of confidentiality, integrity, and authenticity. Secure algorithms, proper authentication methods, and strong encryption standards are essential.
2. Implement Robust Practices
Developers must:
- Use well-tested cryptographic libraries.
- Avoid custom or ad-hoc cryptographic solutions.
- Follow secure coding practices to prevent implementation flaws.
3. Conduct Comprehensive Security Testing
Security testing should include:
- Functional tests to ensure cryptographic systems work as intended.
- Vulnerability assessments to identify weak points.
- Side-channel analysis to detect leaks of unintended information.
4. Enable Continuous Monitoring
Regular monitoring of cryptographic systems helps detect breaches, vulnerabilities, or usage anomalies. Applying security updates and patches promptly is vital to maintaining system integrity.
Best Practices for Cryptographic Security
1. Strengthen Key Management
- Use long, complex encryption keys.
- Implement key rotation and revocation policies.
- Securely store encryption keys in hardware security modules (HSMs).
2. Adopt a Defense-in-Depth Approach
Layer multiple security controls, such as access restrictions, intrusion detection systems, and endpoint protection, to reduce reliance on cryptographic measures alone.
3. Monitor Emerging Threats
Stay up-to-date on the latest cryptographic vulnerabilities and attack techniques through threat intelligence feeds, industry publications, and security advisories.
4. Foster Collaboration
Participation in information-sharing platforms and collaboration with industry peers can help organizations gain insights into common challenges and mitigation strategies.
5. Train and Educate Employees
Conduct regular training programs to increase awareness of cryptographic best practices and attack vectors. Employees should also be educated about secure coding and the safe handling of encryption keys.
Cryptographic failures pose significant risks in an increasingly interconnected digital world. From compromised encryption protocols to poor key management practices, these failures can have devastating consequences, including data breaches, financial losses, and reputational damage.
However, by understanding the causes and types of cryptographic failures, organizations can implement robust strategies to prevent them.
By adopting secure design principles, enforcing proper key management, and staying vigilant against emerging threats, organizations can strengthen their cryptographic defenses and safeguard sensitive data against cyberattacks.




