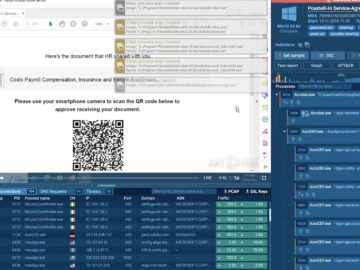
QR code Phishing, or “Quishing,” is a cyber threat that exploits the widespread use of QR (Quick Response) codes in phishing attacks.
Quishing takes advantage of the recent high-use volume and increasing popularity of QR codes. These codes, which can be easily scanned using smartphones, are commonly seen as innocent and have become a widely used tool for businesses and organizations to exchange information, facilitate payments, or guide users to websites. Exploiting this trust and familiarity is a common tactic in certain activities.
Scammers can utilize QR codes through various channels, such as emails, text messages, social media, public places, or even by directly approaching individuals to scan them.
The FBI has reported an increase in scammers instructing victims to utilize physical crypto ATMs and QR codes for payment transactions.
Fraudsters often manipulate victims into making payments and instruct them to withdraw funds from their financial accounts, including investment or retirement accounts.
The FBI cautions that a QR code linked to the scammer’s cryptocurrency wallet will be given to the victim for use in the transaction.
The fraudster will then guide the target to a physical cryptocurrency ATM where they can deposit their funds, buy cryptocurrency, and utilize the given QR code to fill in the recipient’s address automatically.
QR Code phishing can be prevented using an advanced AI email security leader, Trustifi, which monitors all attacks on its clients with its security operations (SecOps) teams. From July to September, the SecOps team saw a 250% rise in hacks that erase QR codes in 2023.
An In-Depth Analysis of 1.3 Million Emails exposes the staggering volume of threats that evaded conventional gateway solutions. Download The Report Now.
How Quishing Works
Generating a Malicious QR Code
Cybercriminals create QR codes that, when scanned, direct users to deceptive websites or initiate the download of harmful software.
The QR codes can be distributed through different channels, including emails, social media, printed materials, or by placing stickers over legitimate QR codes in public areas.
The Scam Process
Once someone scans the QR code, they are directed to a deceptive website that may appear legitimate. On this site, they are prompted to provide sensitive information such as login credentials, personal data, or financial details.
Malware may be downloaded in response to certain quishing attempts that lead to compromising devices and networks.
The attackers leveraged compromised email accounts to exploit the victim organization’s legitimate Outlook infrastructure for sending the QR codes. The phishing pages found after QR code scans were hosted through an enterprise survey service and linked to IP addresses associated with Google or Amazon.
What sets these messages apart is that they include QR codes that allow users to access missed voicemails. This cleverly avoids the need to scan URLs for email attachments, which secure email gateways and native security controls typically block.
Mostly, the QR code images were generated on the same day they were sent, which reduces the chances of them being flagged by a security blocklist due to prior reports. A total of six distinct profiles were utilized to transmit messages for the campaign, with the majority crafted to appear connected to the industry of interest.
Recent Quishing Aattck
In the latest phishing campaigns, cybercriminals have started utilizing QR codes as an alternative to buttons to redirect victims to fraudulent websites.
These emails lack clear-text URLs and instead use QR codes to obfuscate them, which poses a challenge for security software to detect.
QR codes have become more effective by targeting mobile users, who may have less protection from internet security tools.
Upon reaching the phishing site, individuals are prompted to provide their bank location, code, user name, and PIN.
After inputting these details on the phishing page, the user patiently awaits validation, only to be prompted to re-enter their credentials because they were deemed incorrect.
This repetition is frequently used in phishing campaigns to prevent typos when users enter their credentials for the first time.
It is important to exercise caution when dealing with emails, even if they appear genuine. Refrain from clicking on any buttons, URLs, or QR codes that redirect you to external websites.
Before entering your account credentials, it’s important to verify the domain you’re on to ensure its authenticity.
You may have encountered them in various settings, such as restaurants, parking lots, and marketing campaigns. In 2022, the Federal Bureau of Investigation highlighted the issue of cybercriminals manipulating QR codes to unlawfully obtain victims’ financial funds.
In the past, QR Code phishing attacks were not very common. However, around mid-September 2023, Microsoft Security Research & Threat Intelligence noticed a notable rise in phishing attempts involving QR codes.
Recent incidents of quishing (QR code phishing) highlight the ever-changing strategies employed by cybercriminals and the growing importance of maintaining a high level of caution in digital security.
Trustifi, an AI Email Security Leader, Defends QR Code Phishing
Trustifi has expanded its OCR scanning capabilities to include QR codes embedded with its highly acclaimed Inbound Shield module. Our OCR scanning capability thoroughly examines the QR code object, searching for any embedded URLs and other potentially harmful content that our Trustifi AI filtering engines have already analyzed.
Traditional email security solutions that do not incorporate machine learning and AI protection layers provide limited benefits to organizations regarding phishing.
Trustifi and other AI-enabled email security solutions include several AI-protection filters that analyze embedded URLs and prevent impersonation attacks from launching after the initial email phishing attempt.
Trustifi’s AI-enabled email security utilizes its extensive data sets within its Large Language Model (LLM) to generate sophisticated behavior analytics for detecting malicious content in QR code attacks and AI-generated text messaging.
Preventing advanced AI-powered attacks is a key focus of Trustifi’s email security expertise. The company’s cutting-edge use of AI and machine learning sets it apart, resulting in improved email protection efficiency and streamlined incident response.
Trustifi’s Email Detection and Response (EMDR)
Trustifi’s advanced AI-enabled inbound shield scans every attachment, looking for key indicators of a QR code attack:
- Does the QR Code URL code contain HTTP or HTTPS prompting the user for a username and password?
- Is the QR code URL domain legitimate or misspelled?
- Is the QR Code redirecting the user to a known phishing site?
- Is the QR code attempting to download malicious malware after the user presses the image?
Trustifi’s powerful AI-filtering engine detects these malicious attack methods, preventing these QR codes from performing attacks against their client’s devices. Trustifi’s AI engines learn over time as more of these types of QR codes morph into new attack vectors. This learning process is the key to Trustifi’s continuous success in stopping AI-enabled hacker attacks.
Trustifi OCR Scanning:
Trustifi’s latest feature includes a machine-learning OCR scan that automatically encrypts crucial email files. Trustifi, a SaaS email security firm, today added an AI-enabled functionality to its industry-leading email encryption and DLP product that uses OCR.
Even when attack vectors change, Trustifi’s capacity to monitor all incoming emails for domain impersonation, rogue URL links, and plain text messaging that coerces users into clicking on QR codes is unmatched.
Trustifi’s award-winning Inbound Shield module now scans QR codes using QCR scanning.
OCR scanning checks QR codes for embedded URLs and other rogue material previously filtered by Trustifi AI. OCR scanning is rarely included in legacy email security systems, including secure email gateways.
Implementing AI-Powered Email security solutions “Trustifi” can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account Take Over, Business Email Compromise, Malware & Ransomware
Quishing Attack Targets
Many of these phishing emails were specifically aimed at energy companies, while other sectors, such as manufacturing, insurance, technology, and financial services, were also subject to targeting.
The QR codes in these emails directed users to deceptive Microsoft 365 pages, often masquerading as security setting updates or multifactor authentication requests. This advanced method utilized trusted domains and obfuscation techniques to avoid detection and effectively land in email inboxes.
One notable instance of a quishing attack involved deceptive emails that seemed to originate from credible sources, like the Chinese Ministry of Finance or a parcel delivery service.
These emails included documents with QR codes that, upon scanning, led users to deceptive websites to extract personal and financial data. This strategy successfully transferred the phishing attack from a desktop setting to mobile devices, potentially exploiting weaker anti-phishing defenses.
The adoption of QR codes in phishing campaigns reflects a calculated decision by attackers to take advantage of emerging platforms and changing user habits.
Implementing AI-powered email security solutions can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account Take Over, Business Email Compromise, Malware, & Ransomware – Request Free Demo.
The Risks of Quishing
Personal and sensitive information is at risk of being stolen.
Financial Fraud: There is a risk of direct financial theft or fraud, particularly when providing payment information.
Malware Infection: Certain deceptive attempts can result in the downloading of malware, posing a threat to the security of devices and networks.
Trust Issues: The growing problem of quishing has resulted in a lack of trust in QR codes, which can significantly diminish their effectiveness for legitimate purposes.
Be cautious of sharing your login credentials, which can lead to unauthorized access to your personal or workplace accounts.
Organizational Risks Potential Security Breaches: If an employee becomes a target of a phishing attack, unauthorized individuals risk gaining access to the company’s networks and sensitive data.
Reputation Damage: If an organization becomes involved in a phishing attack, whether as a target or due to compromised systems, it could seriously damage its reputation.
Financial Losses: Apart from direct theft, businesses can incur financial losses due to the need for remediation, heightened cybersecurity measures, and potential legal repercussions.
Addressing Cybersecurity Concerns Distribution of Malware: Quishing is a method that can be utilized to distribute malware, resulting in the compromise of devices and networks.
The widespread use of QR codes has significantly increased the potential for cybercriminals to exploit vulnerabilities, posing a greater challenge in maintaining comprehensive security measures.
Focusing on Vulnerable Populations: Individuals who are not as familiar with technology may be more vulnerable to phishing attempts, which puts them at a higher risk of being targeted.
Impact on Society Decline in Trust of QR Codes: Frequent quishing attacks can erode people’s trust in QR codes, making them less useful and less likely to be embraced.
Regular exposure to such tactics may cause users to become desensitized to suspicious activity, making them more vulnerable to other types of cyberattacks.
Potential Legal Ramifications for Organizations: Companies that do not adequately safeguard their data may face legal consequences, particularly under data protection regulations such as GDPR.
Compliance Challenges: Organizations must ensure their cybersecurity policies and practices are up-to-date to effectively combat evolving threats, which can require significant resources.
Effective Strategies and Recommended Approaches to Prevent QR Phishing
Increasing User Awareness: It is essential to inform users about the possible risks of QR codes. Users need to exercise caution when scanning QR codes from unfamiliar or untrustworthy sources.
Secure QR Code Generation: Generating QR codes securely and making them tamper-proof is crucial for organizations.
Verification of URLs: Checking the URL after scanning a QR code is recommended to confirm that it aligns with the intended destination.
Certain scanner apps that use secure QR code scanners have advanced security features that can effectively identify and flag any suspicious URLs that may pose a potential threat.
Implementing Multi-Factor Authentication (MFA): Adding a layer of security can be beneficial, particularly for platforms that phishers frequently target.
Consistent Monitoring: It is important for companies to consistently monitor their QR code campaigns to detect any signs of tampering or misuse.
Please exercise caution when sharing information after scanning a QR code: Before entering any personal information or data, it’s important to double-check the logo and the full URL of the page you are on when prompted to click on a link.
For enhanced security, it is advisable to manually enter the original URL into your browser rather than providing sensitive information through a link or QR code.
Organizations should adopt efficient incident response plans, regularly monitor email traffic for anomalies, and stay updated on emerging threats to stay ahead of the evolving email threat landscape with Trustifi AI-powered Email security solutions.