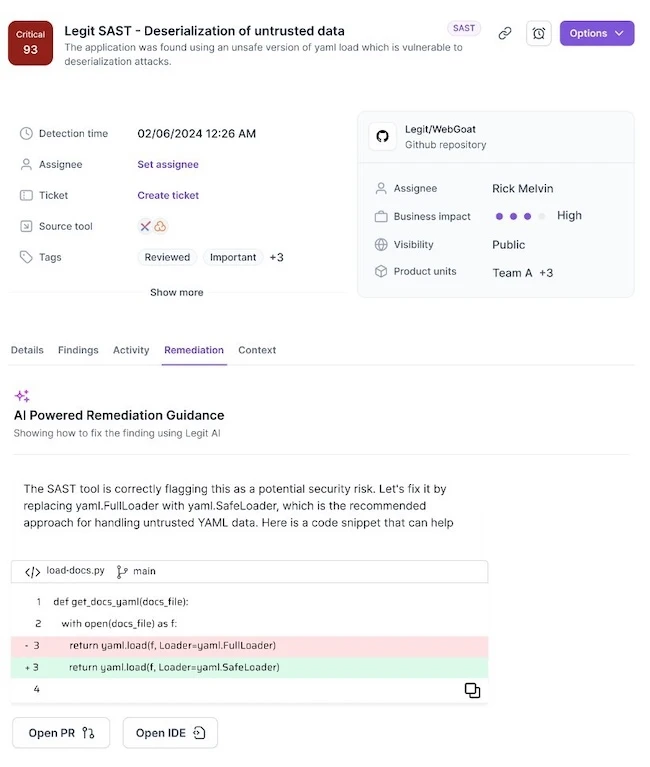
The NSA has published Phase One and Phase Two of its Zero Trust Implementation Guidelines, providing structured guidance for organizations working to implement zero trust cybersecurity practices. The documents are part of a larger series designed to support adoption of zero trust frameworks aligned with the Department of Defense target-level maturity model.
Guidelines aim to guide practical implementation
Phase One outlines 36 activities focused on establishing conditions that support 30 specific zero trust capabilities at this stage of implementation. Phase Two defines 41 activities that begin integrating core zero trust solutions into organizational environments, enabling 34 distinct capabilities associated with this later phase.
NSA officials said the phased design allows organizations to tailor efforts based on their goals and constraints. The modular structure is intended to make it possible to adopt foundational and advanced tasks based on organizational maturity and operational context.
Context within the broader zero trust series
The Phase One and Phase Two releases follow earlier guidance issued this year, including a Primer and a Discovery Phase guideline. The Primer outlines the strategy, principles, and structure behind the implementation series. The Discovery Phase focuses on establishing baseline visibility into assets, users, applications, data, and access activity, providing groundwork for later implementation work.
System owners, cybersecurity professionals, and other stakeholders should review the Primer and Discovery Phase guidance before moving into the new phases to support a consistent understanding of zero trust activities and operational environments.
The Zero Trust Implementation Guidelines align with existing federal frameworks, including the Department of Defense CIO’s Zero Trust Framework, and aim to translate high-level principles into discrete tasks for security teams.
What practitioners see in the guidance
Security practitioners reviewing the guidance said its emphasis on continuous evaluation and coordinated enforcement reflects where zero trust efforts need to mature.
Brian Soby, CTO of AppOmni, told Help Net Security that the guidance reinforces the need to move beyond access checks at login. “Continuous evaluation has to happen after login, not just at login,” Soby said. “The guidance pushes maturity beyond authenticate, then trust, toward ongoing decisions driven by what the user is doing, what privileges are being requested, and what resources are being touched.”
Soby said this focus reflects current attack patterns. “The attacks that are winning right now are post-auth,” he said, adding that device posture and login checks offer limited protection when abuse occurs inside an active session.
He also pointed to the emphasis on policy coordination across environments. “A major theme in the guidance is that zero trust is an operating model,” Soby said. “Policies have to be centrally defined, consistently applied, continuously assessed, and enforced through coordinated policy decision points and policy enforcement points, with real-time monitoring and automation.”
The guidance also highlights behavioral analytics as a core capability. Soby said the documents place appropriate weight on understanding activity inside applications. “Meaningful UEBA requires understanding real activity, not generic signals,” he said. “The higher-signal story is what happened in the application, including privilege use, data access, configuration changes, and unusual exports.”
Where organizations continue to struggle
Soby said the guidance covers the necessary components, but many implementations fall short in practice. One common issue is an overreliance on zero trust network access tools. “Organizations over-center on ZTNA, and ZTNA-only architectures are easy to bypass,” he said. He added that treating zero trust as a completed project after deploying ZTNA ignores application-layer risk.
Another gap is failure to treat applications themselves as enforcement points. “Each application is its own policy decision point and policy enforcement point,” Soby said. He noted that many identities never pass through enterprise gateways, including customers, partners, integrations, and non-human identities.
“Any zero trust architecture that leaves visibility and management of the application PDPs and PEPs out of the architecture is expensive and grossly insufficient,” Soby said.