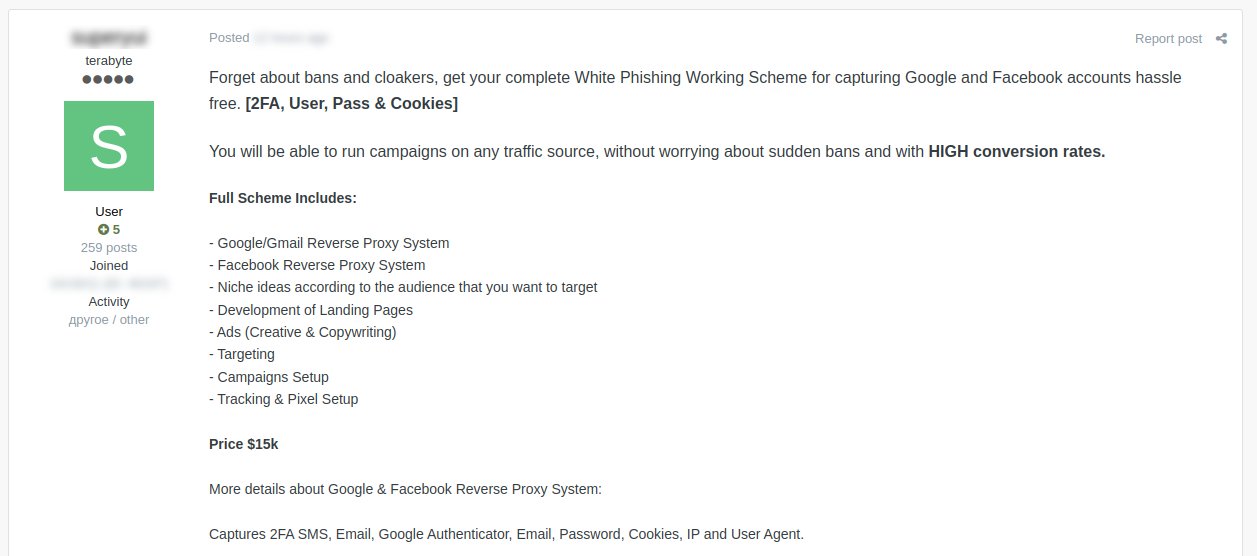
An individual on the dark web was detected advertising a tool capable of extracting information from Facebook and Google accounts.
The tool, known only as the “White Phishing Working Scheme,” is currently available for sale on the dark web marketplace at a price of $15,000.
This scheme has been actively promoted, highlighting numerous advantages and boasting a remarkable conversion rate for malicious intents.
White Phishing Working Scheme
Threat Intelligence platform Falcon Feeds tweeted the above image and the dark web sale of the infostealer.

The dark web user noted that the White Phishing Working Scheme could steal account data from Google and Facebook accounts hassle-free.
Facebook and Google users may have their information compromised including their emails, password, cookies, and IP address. The two-factor authentication codes that are sent over email and/ or SMS are also at risk of being exposed to hackers.
Moreover, the dark web marketplace seller of the White Phishing Working Scheme claimed that it can be used to pilfer Google Authenticator data as well.
All this data when exposed to cybercriminals can release every email conversation to them posing a threat not to one user but to all those connected to the single target.
Hackers can create emails to be sent to their contacts while posing as a known individual or organization having all the information about them from hacking their accounts.
Likewise, as a cybercriminal uses the White Phishing Working Scheme on Facebook, they can use the login details to access their photos, videos, chats, and status updates for malicious gains.
To maintain caution, it is advisable to check active sessions to know on which devices the account is logged in. And to log out of all unknown devices.
Constantly checking emails for any new login attempts may also alert you about unauthorized login attempts which can be curbed in time.
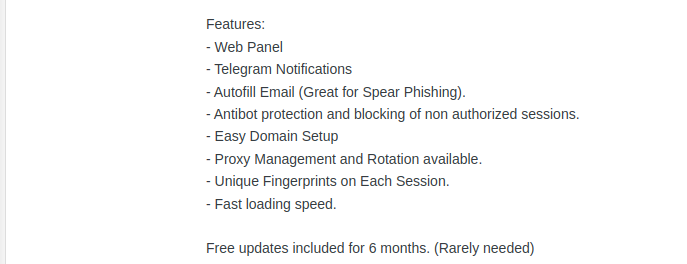
The White Phishing Working Scheme with diverse benefits to hackers could autofill emails for their ease making users vulnerable to being randomly picked by users.
With hackers being offered web panels with an assurance of fast loading speed, the work of cybercrime experts becomes twofold in detecting and stopping the use of such tools.
Moreover, the seller of the infostealer boasted that it cannot be detected in the antibot protection and blocking tool working on a device.
While cybersecurity teams make every effort to ramp up security mechanisms, developers who use their skills for malicious activities are creating tools that bypass detection.
One way to improve the security of devices and data could be to keep an eye out for malicious software sold on the dark web marketplaces and design detection tools accordingly.
Information Stealers on the Rise
A recent research stated that data hacks due to infostealers have increased over the years. It has doubled in Q1 2023 as compared to 2022.
It was found that Telegram was the main source for the Command and Control activities including taking back the stolen data from the target.
Among the most used infostealers was Redline which amounted to 56% of the market share, followed by Raccoon and the RecordBreaker stealer. The research noted that the infostealer used to break the security of the ride-sharing platform Uber was Racoon.
The hackers used Racoon to send two-factor authentication requests on the device of an employee of Uber who eventually felt compelled to approve a request.
Infostealers pose a serious threat to security when organizations use personal devices for work. While office devices may be monitored and have threat detection and authentication mechanisms put in place, mobile phones or personal computers may not.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
