Modern organizations face mounting challenges in securing their public-facing assets. From the rise of shadow IT to third-party supplier exposures, the array of risks and pitfalls in today’s digital environments make it nearly impossible to maintain meaningful cyber resilience using traditional defense methods.
To stay ahead of emerging threats and maintain a strong security posture, security teams are turning to external attack surface management (EASM) as a key component of their digital risk protection strategy.
This article examines the critical role EASM plays in digital risk protection (DRP), and how security teams can effectively use tools like these to enhance ongoing digital resilience efforts and mitigate potential vulnerabilities.
Bridging the gap
Security teams these days are regularly tasked with managing complex, sprawling public-facing digital attack surfaces that are not only difficult to manage, but often hard to fully understand and map. This challenge is amplified in hybrid environments, where blurred lines of ownership and responsibility make effective security oversight even more difficult.
Recent data highlights just how fragmented the modern digital footprint has become. Organizations now rely on a wide range of technologies to support their operations, but this diversity often leads to visibility gaps and an increased risk of exposure. Without clear and continuous visibility into these expanding attack surfaces, vulnerabilities become easier to overlook – and for attackers to exploit.
Unsurprisingly, 83% of cyberattacks originate from external actors, many of whom exploit weaknesses at the network perimeter. With Gartner naming EASM as the top cybersecurity trend for the next five to ten years, it’s clear that managing these external entry points has become a critical priority for security teams.
Understanding EASM
EASM is the ongoing practice of identifying and addressing vulnerabilities and security gaps across an organization’s internet-facing digital footprint. Crucially, this involves the continuous discovery, evaluation, and mitigation of externally accessible attack vectors—many of which are overlooked in traditional security approaches.
Key components of an effective EASM approach include:
- Asset Discovery – Mapping all public-facing digital assets, including websites, applications, cloud services, and exposed infrastructure components.
- Vulnerability Assessment – Evaluating IT assets to uncover misconfigurations, outdated software, or other weaknesses that could be exploited. Regular penetration testing combined with EASM is also crucial for further identifying security gaps that automated tools or high level scans may miss.
- Threat Intelligence – Collecting and analyzing data on emerging threats and TTPs of threat actors to better understand potential risks.
- Continuous Monitoring – Maintaining real-time visibility to detect changes, new exposures, or signs of malicious activity as they occur.
Together, these components enable security teams to maintain a proactive security posture by continuously reducing exposure and staying ahead of potential threats.
Gain a consistent and clear view of your ENTIRE organizations digital presence and any cyber threats hiding within.
Outpost24s innovative combination of Cyber Threat Intelligence and Attack Surface Management offers a full overview of external threats & risks facing your organization. This makes it easier to prioritize threats and fight them proactively.
Get a Free Assessment
The importance of DRP
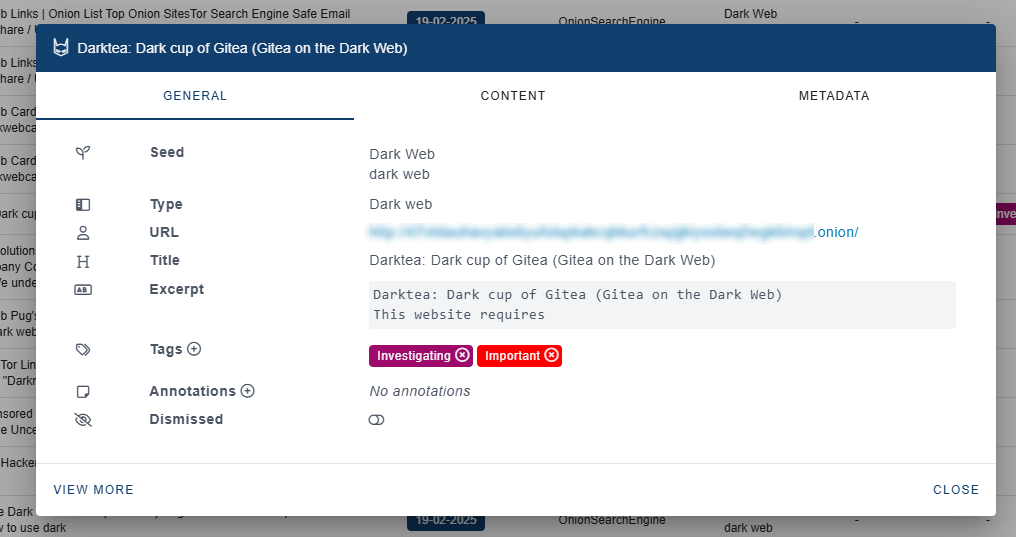
While EASM is centered on uncovering vulnerabilities in public-facing IT assets to strengthen an organization’s security posture, DRP takes a broader approach by proactively identifying and mitigating external threats that emerge from an organization’s digital footprint—spanning public sources as well as Social Media presence and deep and dark web channels.
DRP improves cyber resilience through four key objectives:
- Risk Identification – Detecting potential threats to digital assets across various external environments.
Detect and monitor Cyber Risk outside of your owned assets. - Risk Mitigation – Taking proactive steps to minimize the likelihood and impact of identified risks.
- Compliance – Ensuring ongoing alignment with regulatory and industry-specific requirements.
- Reputation Management – Safeguarding the organization’s brand and public perception from reputational threats.
Collectively, these four objectives enable organizations to proactively safeguard their digital assets, minimize external threats, and maintain a resilient security posture that protects both operational integrity and brand reputation.
How EASM can help enhance DRP
By aligning DRP with EASM, security teams can gain a comprehensive view of their external risk landscape —empowering them to respond swiftly, protect critical assets, and uphold organizational trust in an increasingly complex threat environment.
EASM enhances DRP by providing the following crucial functions:
Comprehensive visibility
EASM provides organizations with a comprehensive view of their external attack surface, a critical element for effective DRP. With clear visibility into all potential exposures, security teams can better safeguard against cyber risks, laying the foundation for robust cyber resilience.
Proactive threat detection
Undetected security gaps that elude security teams are likely to be exploited by cyber attackers. By proactively identifying and mitigating threats before they can be leveraged by malicious actors, EASM helps minimize risks that could lead to cyberattacks and data breaches.
Risk prioritization
In an ideal world, organizations would have unlimited resources for cybersecurity. However, the reality is that security teams must focus on protecting what matters most. EASM empowers them to prioritize risks based on their potential impact and likelihood, ensuring resources are allocated where they are needed most.
Incident response
Time is critical when responding to security incidents, as swift action is key to limiting the impact of breaches and minimizing data exfiltration. EASM enhances incident response by providing real-time insights and actionable intelligence, enabling teams to act quickly and decisively.
Best practices for integrating EASM into DRP
To successfully integrate EASM into your DRP strategy, consider adopting the following best practices:
Regular assessments
Conduct regular EASM assessments to stay ahead of emerging threats. Continuous evaluation of your external attack surface helps identify new vulnerabilities and allows for timely mitigation before these risks are exploited.
Collaboration
Collaboration is key to effective EASM integration. Encourage regular communication and cooperation between departments like IT, security, and compliance. By working together, different teams within the organization can align their efforts and create a more cohesive approach to managing digital risks.
Continuous improvement
Cyber threats are constantly evolving, so it’s crucial to emphasize continuous improvement. Ensure your EASM and DRP strategies are adaptable to new threats, incorporating lessons learned from past incidents to strengthen your security posture over time.
Vendor selection
In selecting an EASM vendor, you should consider your organization’s specific needs and ensure that candidate solutions provide the scalability, flexibility, and capabilities necessary for comprehensive attack surface management.
You should also evaluate its threat intelligence integrations—a broader range of integrations offers a more unified approach to DRP. For instance, Outpost24’s EASM solution combines data gathering, enrichment, and AI-driven analysis into a seamless, event-driven platform that provides the most comprehensive and actionable view of your attack surface.
To learn more, claim a free attack surface analysis today.
Sponsored and written by Outpost24.
