Picture this: you’ve hardened every laptop in your fleet with real‑time telemetry, rapid isolation, and automated rollback. But the corporate mailbox—the front door for most attackers—is still guarded by what is effectively a 1990s-era filter.
This isn’t a balanced approach. Email remains a primary vector for breaches, yet we often treat it as a static stream of messages instead of a dynamic, post-delivery environment. This environment is rich with OAuth tokens, shared drive links, and years of sensitive data.
The conversation needs to shift. We should stop asking, “Did the gateway block the bad thing?” and start asking, “How quickly can we see, contain, and undo the damage when an attacker inevitably gets in?”
Looking at email security through this lens forces a fundamental shift toward the same assume-breach, detect-and-respond mindset that already revolutionized endpoint protection.
The day the wall crumbled
Most security professionals know the statistics. Phishing and credential theft continue to dominate breach reports, and the financial impact of Business Email Compromise often outweighs ransomware. But the data tells a more interesting story, one that mirrors the decline of legacy antivirus.
A decade ago, AV was good at catching known threats, but zero-day exploits and novel malware slipped past. Endpoint Detection and Response (EDR) emerged because teams needed visibility after an attacker was already on the machine.
Email is following the same script. Secure Email Gateways (SEGs) still filter spam and commodity phishing campaigns reasonably well. What they miss are the attacks that define the modern threat landscape:
- Payload-less Business Email Compromise (BEC)
- Malicious links that are weaponized after delivery
- Account takeovers using stolen credentials that involve no malware at all
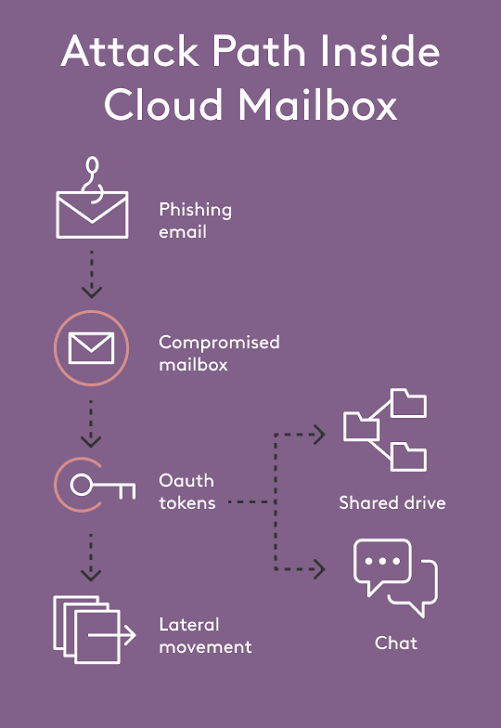
Once a single mailbox is compromised, the attacker gains access to a connected graph of OAuth applications, shared files, chat histories, and calendar invites within Microsoft 365 or Google Workspace. Moving laterally through this graph rarely triggers another SEG alert. The damage happens entirely inside the cloud workspace.
What email security can learn from the endpoint
In the endpoint world, the breakthrough wasn’t a better blacklist. It was the realization that prevention must be paired with continuous visibility and fast, automated response. EDR platforms gave us the ability to record process trees, registry changes, and network calls. When a threat was detected, a host could be isolated and changes could be rolled back, all from a single console.
Now imagine giving email administrators the same super‑powers: a rewind button for messages, OAuth scopes and file shares; the ability to freeze—or at least MFA‑challenge—a mailbox the instant a risky rule is created; and a timeline that shows who read which sensitive thread after credentials were stolen.
This combination of capabilities is what a modern, EDR-like approach to email security provides. It’s a simple idea: assume an attacker will eventually land in a mailbox and build the tooling needed to detect, investigate, and contain the fallout.
The API-first moment that made it possible
For years, adding post-delivery controls to email required fragile journaling configurations or heavyweight endpoint agents. The cloud suites quietly solved this problem for us.
Microsoft Graph and Google’s Workspace APIs now expose the necessary telemetry—mailbox audit logs, message IDs, sharing events, and permission changes—securely over OAuth. The same APIs that provide visibility also provide control. They can revoke a token, pull a delivered message from every inbox, or remove a forwarding rule in seconds.
The sensors and the actuators are already baked into the platform. We just need to connect them to a workflow that feels like EDR. As we’ve argued in our post, The Evolution of Email Security, this richness of telemetry is what allows security teams to move beyond the whack-a-mole of tuning filter rules. Instead of waiting for a user to report a phish, the platform can notice an impossible-travel sign-in, see that the account immediately created five new sharing links, and automatically remediate the risk.
Why this matters for lean security teams
A Director of Security at a small or even mid-size company is often the entire security department, juggling vulnerability management, incident response, and compliance. Tool sprawl is the enemy.
An EDR-like approach to email collapses several fragmented controls—SEG policy, DLP, incident response playbooks, SaaS-to-SaaS monitoring—into a single surface. There are no MX record changes, no agents to deploy, and no dependency on users clicking a “report phish” button.
More importantly, it produces metrics that matter. Instead of citing an arbitrary “catch rate,” you can answer board-level questions with concrete data:
- How quickly do we detect a compromised mailbox?
- How much sensitive data was accessible before containment?
- How many risky OAuth grants were revoked this quarter?
These numbers describe actual risk reduction, not theoretical filter efficacy.
A pragmatic way to move forward
This doesn’t have to be an abstract exercise. The path forward is incremental, and each step provides a tangible security benefit.
- Enable native audit logs. Both Microsoft 365 and Google Workspace include extensive logging. This is the ground truth you’ll need for any future automation.
- Centralize your telemetry. In your SIEM or log platform, start looking for signals of compromise: sudden mail rule creation, mass file downloads, unusual sign-in locations, and new OAuth grants.
- Test automated response. Use the native APIs to test “message clawback” with a phishing simulation. Both Microsoft Graph and the Gmail API offer these endpoints out of the box.
- Evaluate dedicated platforms. Judge them on their breadth of coverage, the sophistication of their post-compromise playbooks, and the speed between detection and automated action.
This journey turns guesswork into evidence, a live breach into a contained incident, and keeps the human effort required proportional to your team’s size.
The bottom line
No one in 2025 would argue that endpoint antivirus is sufficient on its own. We assume prevention will eventually be bypassed, so we build for detection and response. Email deserves the same pragmatic approach.
Of course inbound detection remains critical. But if your security stack can’t also tell you who read a sensitive contract after a mailbox takeover or prevent that exposure automatically then you are still operating in the antivirus era. The attackers have moved on. Your inbox, like your laptop, is ready for an upgrade.
Where Material Security fits in
Material Security was built on the premise we’ve explored here: email is a dynamic, high-value environment that needs post-delivery defenses, not just another pre-delivery filter.
Because Material integrates directly with Microsoft 365 and Google Workspace via their native APIs, deployment takes hours, not months, with no disruption to mail flow.
Once connected, Material records the same fine‑grained telemetry that powers EDR on the endpoint—every mailbox rule, OAuth grant, file share, and sign‑in event—then layers on automated playbooks that shrink a breach window from days to minutes. A suspicious sign‑in can trigger a just‑in‑time MFA challenge, while delivered phish are clawed back across every inbox before they’re even read. Historic mail is wrapped in zero‑knowledge encryption that forces re‑authentication, so stolen credentials alone can’t unlock years of sensitive data.

Perhaps most importantly for security teams of one, Material folds these controls into a single, searchable timeline. You can answer board‑level questions—What was accessed? Who saw it? How quickly did we contain it?—without stitching together half a dozen logs.
In short, Material brings the “assume breach, detect fast, respond faster” ethos of modern endpoint defense to the inbox, turning email from a perennial blind spot into a fully monitored, rapidly recoverable asset.