For years, defensive security strategies have focused on three core areas: network, endpoint, and email. Meanwhile, the browser, where most modern work happens, sits across all of them. Cybercriminals have adapted to this, shifting attacks away from perimeter defenses and into the browser itself.
Browser-based threats manipulate web applications in real time, evading detection by firewalls, Secure Web Gateways (SWGs), and Endpoint Detection & Response (EDR) solutions. From multi-step phishing to malware reassembly, new attack methods make it critical for security teams to rethink detection and response at the browser layer.
This article examines three key areas where attackers focus their efforts and how browser-based attacks are evolving.
A New Class of Threats
Malware Reassembly: The New Breed of Fileless Attacks
Traditional security models are designed to detect and block file-based malware. However, attackers have moved away from conventional payloads in favor of malware that dynamically reassembles itself within the browser. These attacks are virtually invisible to endpoint and network security tools.
Campaigns like ClearFake and SocGolish use JavaScript loaders and HTML injections to modify web pages and reassemble malicious code and file downloads directly in a browser tab.
By operating within the browser’s execution environment, these threats evade traditional detection mechanisms, allowing cybercriminals to hijack user sessions, pass drive-by downloads, steal credentials, and compromise sensitive data.
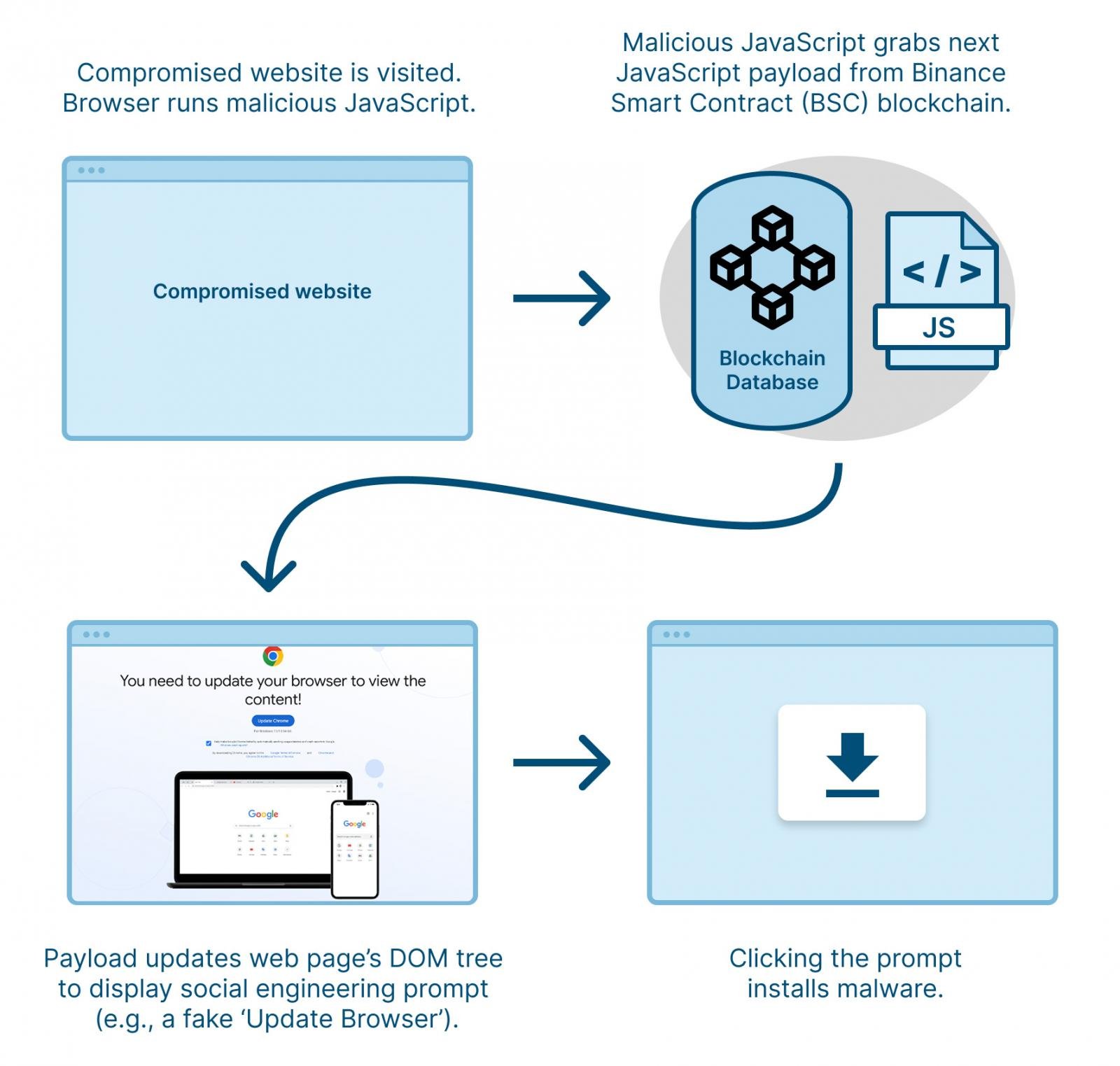
Without real-time visibility into how web pages and scripts behave inside the browser, organizations remain blind to these emerging attack techniques.
Keep Aware provides security teams with instant visibility into browser activity. With click-by-click telemetry, DOM-tree analysis, and threat blocking capabilities, you can detect and stop malicious activity where it starts.
Gain full investigative power and ensure browser threats are stopped before they harm your users, data, or apps.
Request a Demo
Phishing & Trusted Site Exploitation: The Evolution of Social Engineering
Attackers have refined phishing techniques to bypass automated detection by employing sophisticated, multi-step tactics. These include:
- Multiple redirects to avoid URL-based detection and isolation mechanisms.
- JavaScript-rendered phishing pages that dynamically generate malicious content on demand.
- CAPTCHAs, fingerprinting, and session-based access control to block security tools from scanning fraudulent sites.
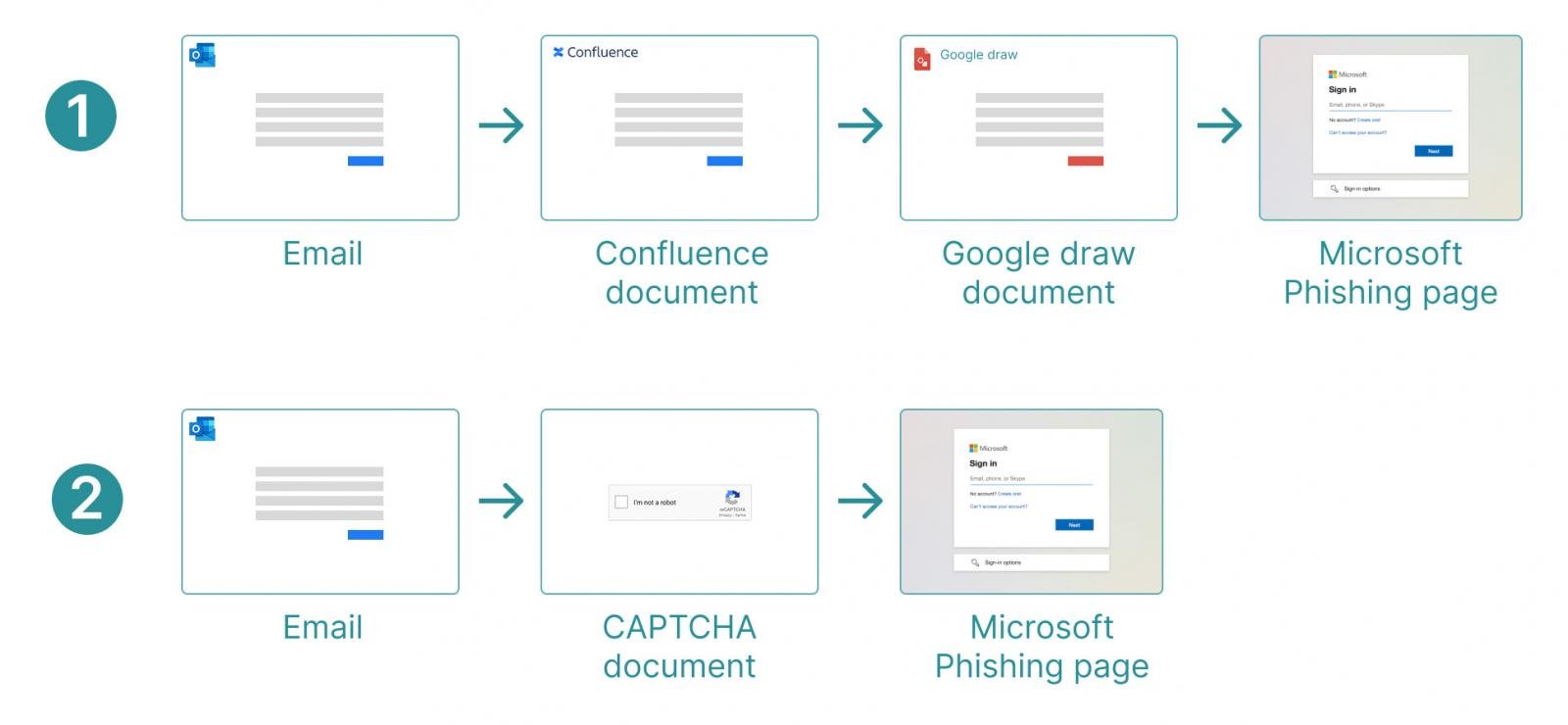
Keep Aware’s recent browser security report highlighted that a staggering 70% of multi-step phishing campaigns impersonate Microsoft, OneDrive, or Office 365 applications.
While these have long been prime targets, attackers now leverage inherently trusted platforms like Google Docs, Dropbox, and AWS to host malicious content, making detection significantly more difficult.
Since traditional reputation analysis and isolation is ineffective against these tactics, security teams need detection models that operate within the browser itself to monitor page structure and detect changes over time—regardless of URL.
The Browser Extension Blind Spot: A Growing Attack Surface
Browser extensions have evolved from simple productivity tools into deeply integrated applications with access to just about everything happening in the browser. Despite their increasing complexity, extension security remains largely unmonitored, creating an enormous attack surface for cybercriminals.
- Info-Stealers and other malicious extensions can masquerade as legitimate tools while silently exfiltrating data.
- Compromised Chrome Web Store accounts have led to the mass distribution of rogue extensions, bypassing standard security reviews.
- Extension re-enablement or version updates can pose immediate security risks as new permissions, ownership changes, and new source code are presented into the organization.
A cybersecurity company recently suffered an attack where a compromised Chrome Web Store account resulted in a malicious browser extension being distributed to its customers.
This highlights the urgent need for real-time extension monitoring, enforceable policies, and automated alerting on extension risks.
The Security Gap: Why Traditional Tools Fall Short
The fundamental challenge in browser security lies in its unique data model—the Document Object Model (DOM)—which governs how web pages are rendered and manipulated but remains largely ignored as a vulnerability.
Unlike network and endpoint security, which monitor traffic and process execution, the browser is an active execution environment where content and scripts dynamically change.
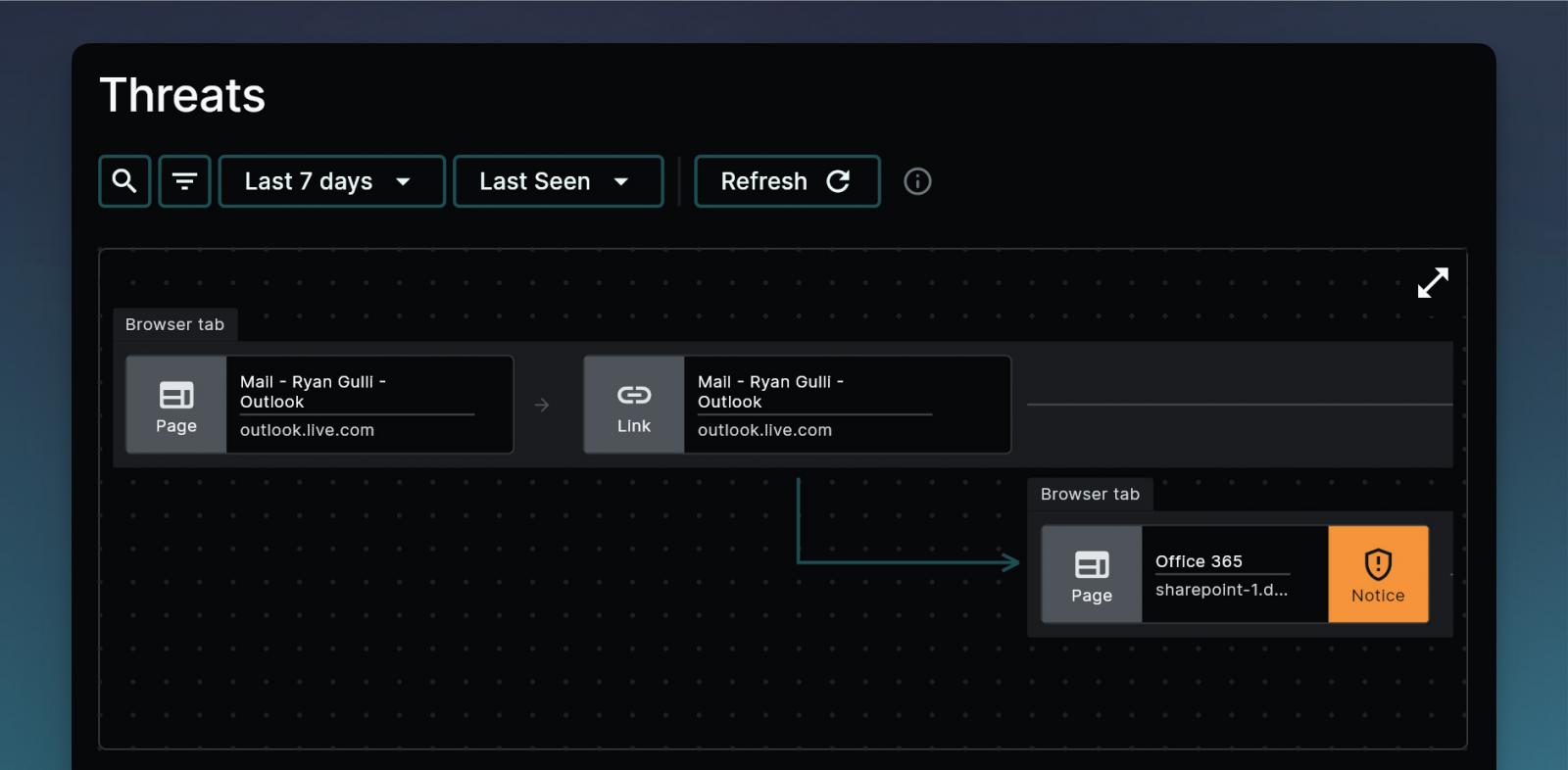
Organizations must adopt a browser-native threat detection model, monitoring session behaviors, credential input patterns, and high-risk interactions in real time. Security controls must evolve beyond blocklists and URL filtering to incorporate context-aware detection.
Just as EDR transformed endpoint security, Browser Detection & Response (BDR) must become a core component of enterprise security, enabling real-time telemetry, JavaScript execution analysis, and browser-layer threat intelligence integration into security operations.
The Browser is a Risk Across the Enterprise
While detection and response are critical to browser security, organizations must also consider broader enterprise risks, including:
- Data exposure risks: Sensitive information can be copied, pasted, uploaded, or shared within unmonitored SaaS applications.
- Shadow IT proliferation: Employees routinely use unsanctioned tools and AI-powered applications in the browser, bypassing IT controls.
- Generative AI risks: Employees paste confidential data into AI-powered chatbots and assistants without understanding security implications.
- Insider threats: Compromised accounts and malicious insiders can exfiltrate corporate data directly within the browser.
These challenges underscore the need for continuous visibility and threat prevention that extends beyond network, endpoint, and email. Security teams must rethink browser governance, data security, and insider risk management as part of a holistic enterprise security strategy.
For a deeper dive into browser-based threats and emerging security trends, explore Keep Aware’s recent State of Browser Security report.
A New Reality
The browser is no longer just a productivity tool—it is a primary attack surface attackers have weaponized to bypass traditional security defenses.
As phishing campaigns evolve, malware reassembly becomes more sophisticated, and browser extensions remain unchecked, organizations that fail to adapt will remain vulnerable.
Security teams must integrate browser detection & response capabilities into their enterprise security stack to gain real-time visibility, detect browser-native threats, and protect people where they work.
Request a free demo with a Keep Aware team member to uncover the browser-based threats your security tools are missing and take the next step in securing your workforce.
AUTHOR: Ryan Boerner
Boerner, a computer engineer turned cyber security practitioner, began as a SOC analyst tackling network threats across Texas agencies. Specializing in network and email security, he later honed his expertise at IBM and Darktrace, working with organizations of all sizes. Seeing a critical gap between security teams and employees—where strong defenses still let threats through—he founded Keep Aware to make the browser a cornerstone of enterprise security.
Sponsored and written by Keep Aware.
