A critical vulnerability in Windows heap management demonstrates how improper handling of record-size fields enables arbitrary memory read and write operations.
Suraj Malhotra shared a detailed exploitation technique leveraging the Low Fragmentation Heap (LFH) mechanism to achieve code execution on Windows systems.
Windows Heap Exploitation Vulnerability
The Windows NT Heap operates through FrontEnd and BackEnd allocators. The FrontEnd allocator manages small allocations under 16KB using LFH, while BackEnd handles larger requests.
LFH activation requires 18 subsequent allocations of similar sizes, creating predictable memory layouts exploitable by attackers. The vulnerability manifests in applications using private heaps created through HeapCreate() functions.
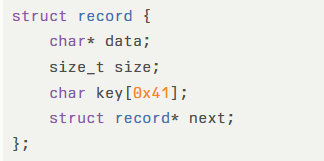
These environments offer reduced security mitigations compared to default process heaps accessed via GetProcessHeap(). The core vulnerability exists in record update functionality, where applications reuse previous record sizes when reading new data:
Exploitation begins by activating LFH through repeated allocations, then creating controlled memory layouts.
Attackers manipulate the target->size field, which remains unchanged during updates, enabling heap overflow conditions when new data exceeds allocated boundaries.
Suraj Malhotra demonstrates arbitrary read capabilities by filling UserBlocks through LFH activation, creating memory holes via record removal, and reusing chunks with crafted data structures.
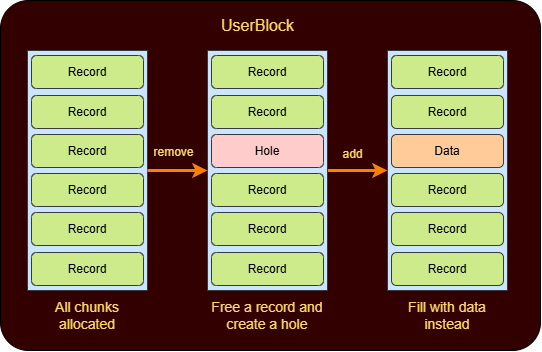
This approach enables reading sensitive memory regions, including heap base addresses, ntdll base locations, and Process Environment Block (PEB) structures.
For arbitrary write primitives, attackers exploit Windows chunk structures containing FLink and BLink pointers in free chunks.
By forging fake chunks and manipulating freelist pointers, researchers achieved FILE structure exploitation involving crafted FILE objects with controlled _base, _file, _flag, and _bufsiz fields.

The FILE structure exploitation requires specific flag combinations including _IOBUFFER_USER (0x0080) and _IOALLOCATED (0x2000) to bypass validation checks.
Setting _base to target memory addresses and _file to stdin enables writing arbitrary data to controlled locations.
Final exploitation involves constructing Return-Oriented Programming (ROP) chains utilizing Windows APIs, including ReadFile, VirtualProtect, and WriteFile, to load and execute shellcode.

The technique leverages Microsoft x64 calling convention, passing arguments through RCX, RDX, R8, and R9 registers using ROP gadgets in ntdll.
This vulnerability analysis, demonstrated through the “dadadb” challenge from Hitcon 2019, highlights the continued importance of proper heap management and size validation.
Organizations should implement robust input validation, utilize modern heap implementations, and employ comprehensive memory protection mechanisms to mitigate sophisticated exploitation techniques targeting Windows heap internals.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.



