A China-linked hacking group is exploiting a Windows zero-day in attacks targeting European diplomats in Hungary, Belgium, and other European nations.
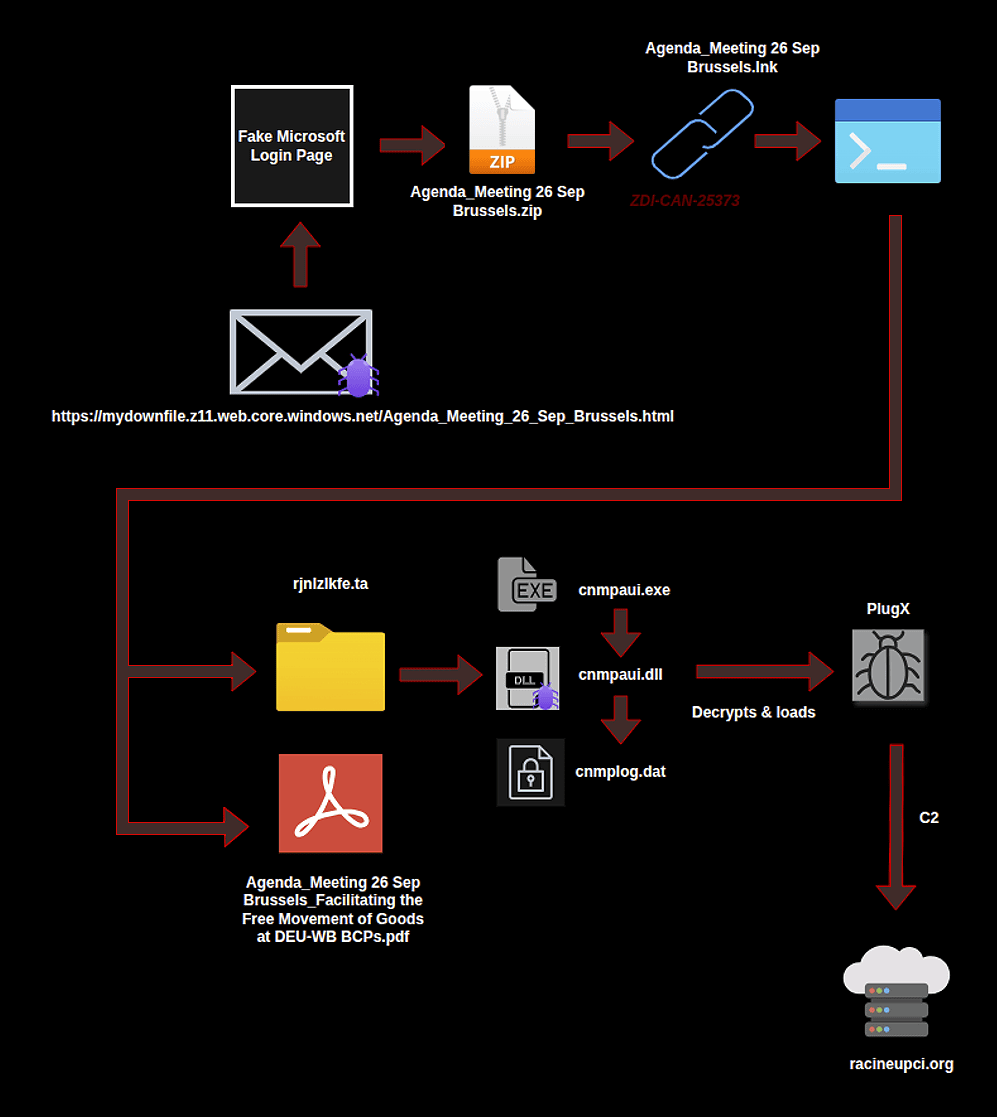
According to Arctic Wolf Labs, the attack chain begins with spearphishing emails that lead to the delivery of malicious LNK files themed around NATO defense procurement workshops, European Commission border facilitation meetings, and various other diplomatic events.
These malicious files are designed to exploit a high-severity Windows LNK vulnerability (tracked as CVE-2025-9491) to deploy the PlugX remote access trojan (RAT) malware and gain persistence on compromised systems, allowing them to monitor diplomatic communications and steal sensitive data.
The cyber-espionage campaign has been attributed to a Chinese state-backed threat group tracked as UNC6384 (Mustang Panda), known for conducting espionage operations aligned with Chinese strategic interests and targeting diplomatic entities across Southeast Asia.
Analysis of malware and infrastructure used in this campaign by researchers from Arctic Wolf Labs and StrikeReady has also revealed that these attacks have broadened their scope in recent weeks. While initially focused on Hungarian and Belgian diplomatic entities, they now also target other European organizations, including Serbian government agencies and diplomatic entities from Italy and the Netherlands.
“Arctic Wolf Labs assesses with high confidence that this campaign is attributable to UNC6384, a Chinese-affiliated cyber espionage threat actor,” the researchers said. “This attribution is based on multiple converging lines of evidence including malware tooling, tactical procedures, targeting alignment, and infrastructure overlaps with previously documented UNC6384 operations.”
Heavily exploited in attacks
The zero-day vulnerability used in this campaign enables attackers to execute arbitrary code remotely on targeted Windows systems. However, user interaction is required for successful exploitation, as it involves tricking potential victims into visiting a malicious page or opening a malicious file.
CVE-2025-9491 exists within the handling of .LNK files, which allows attackers to exploit how Windows displays the shortcut files to evade detection and execute code on vulnerable devices without the user’s knowledge. Threat actors exploit this flaw by hiding malicious command-line arguments within .LNK shortcut files to the COMMAND_LINE_ARGUMENTS structure using padded whitespaces.
In March 2025, Trend Micro threat analysts discovered that CVE-2025-9491 was already being widely exploited by 11 state-sponsored groups and cybercrime gangs, including Evil Corp, APT43 (also known as Kimsuky), Bitter, APT37, Mustang Panda, SideWinder, RedHotel, Konni, and others.
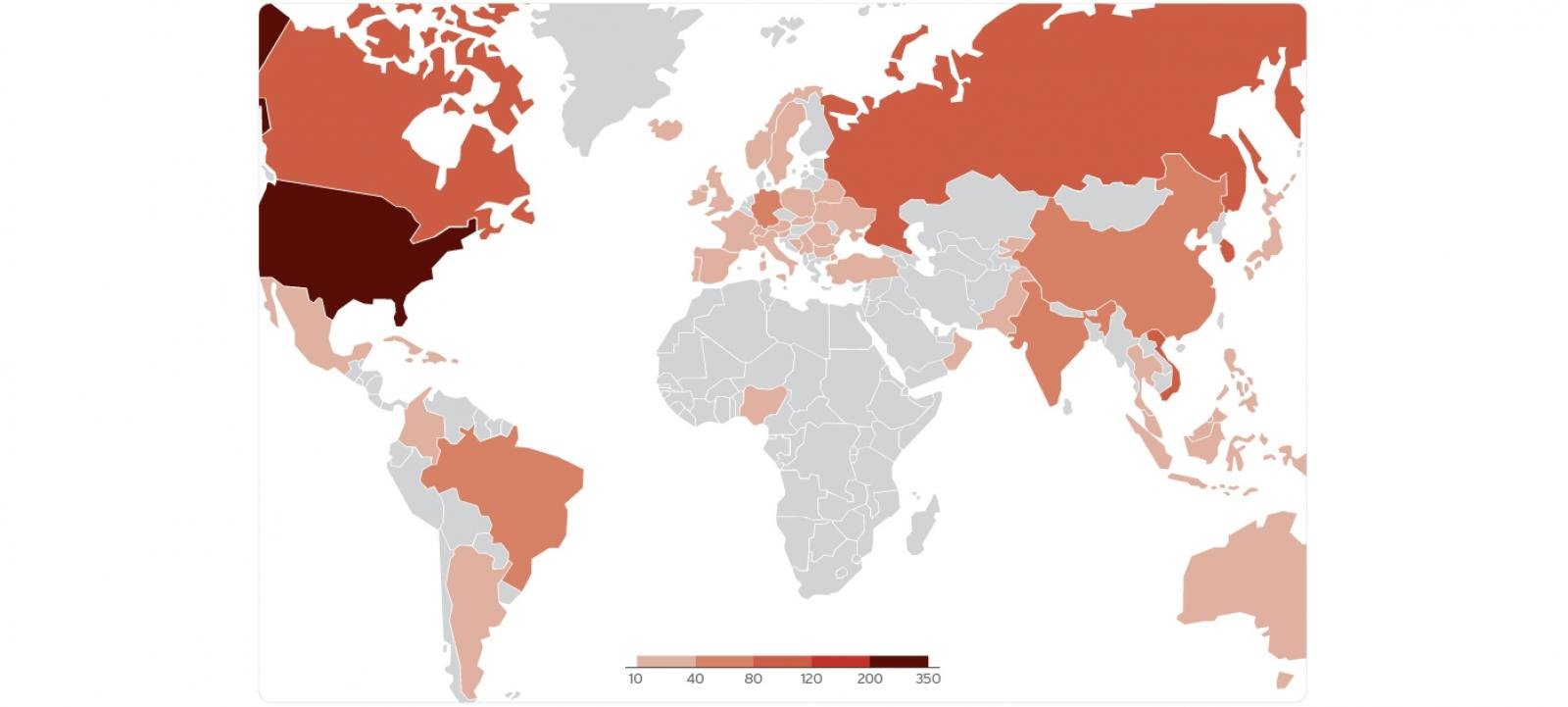
”Diverse malware payloads and loaders like Ursnif, Gh0st RAT, and Trickbot have been tracked in these campaigns, with malware-as-a-service (MaaS) platforms complicating the threat landscape,” Trend Micro said at the time.
While Microsoft told BleepingComputer in March that it would “consider addressing” this zero-day flaw, even though it “does not meet the bar for immediate servicing,” it has yet to release security updates to patch this heavily exploited Windows vulnerability.
Since there is no official CVE-2025-9491 patch to block ongoing attacks, network defenders are advised to restrict or block the use of Windows .LNK files and block connections from C2 infrastructure identified by Arctic Wolf Labs.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
