Winter Vivern APT exploited zero-day in Roundcube webmail software in recent attacks

Russia-linked threat actor Winter Vivern has been observed exploiting a zero-day flaw in Roundcube webmail software.
Russian APT group Winter Vivern (aka TA473) has been observed exploiting a zero-day flaw in Roundcube webmail software on October 11, 2023.
ESET researchers pointed out that is a different vulnerability than CVE-2020-35730, that the group exploited in other attacks.
The Winter Vivern group was first analyzed in 2021, it has been active since at least 2020 and it targets governments in Europe and Central Asia.
In March 2023, security firm Proofpoint observed the group actively exploiting vulnerabilities (CVE-2022-27926) in unpatched Zimbra instances to gain access to the emails of NATO officials, governments, military personnel, and diplomats.
In recent attacks, the group was observed exploiting a XSS vulnerability, tracked as CVE-2023-5631, by sending a specially crafted email message. The messages were sent from team.managment@outlook[.]com and had the subject Get started in your Outlook.
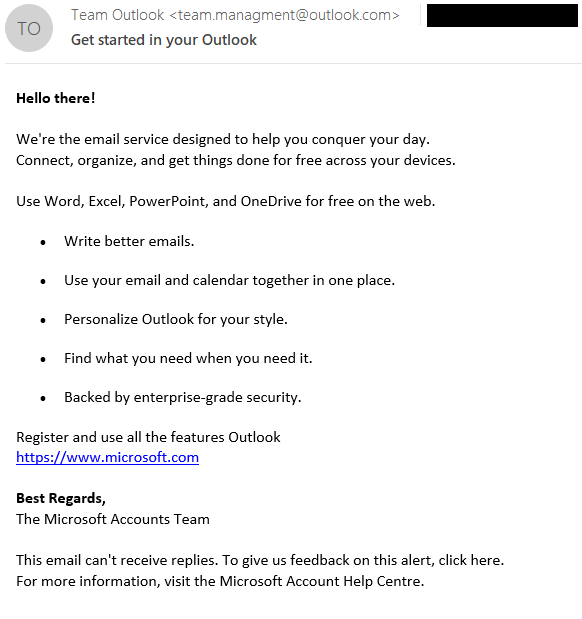
The analysis of the email HTML source code revealed the presence of a SVG tag at the end, which contains a base64-encoded payload.
“Once we decode the base64-encoded value in the href attribute of the use tag, we have:
As the x value argument of the href attribute is not a valid URL, this object’s onerror attribute will be activated.” reads the analysis published by ESET. “Decoding the payload in the onerror attribute gives us the following JavaScript code (with the malicious URL manually defanged), which will be executed in the browser of the victim in the context of their Roundcube session.”
The experts noticed that the JavaScript injection successfully operated also on fully patched Roundcube instances. This incident revealed a zero-day XSS vulnerability impacting the server-side script rcube_washtml.php. The vulnerability is caused by the poor sanitization of malicious SVG documents before they are incorporated into the HTML page interpreted by a Roundcube user.
ESET reported the zero-day to Roundcube, the company patched the issue on October 14th, 2023. The vulnerability affects Roundcube versions 1.6.x before 1.6.4, 1.5.x before 1.5.5, and 1.4.x before 1.4.15.
“Winter Vivern has stepped up its operations by using a zero-day vulnerability in Roundcube. Previously, it was using known vulnerabilities in Roundcube and Zimbra, for which proofs of concept are available online,” ESET concludes. “Despite the low sophistication of the group’s toolset, it is a threat to governments in Europe because of its persistence, very regular running of phishing campaigns, and because a significant number of internet-facing applications are not regularly updated although they are known to contain vulnerabilities.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
Pierluigi Paganini
(SecurityAffairs – hacking, Winter Vivern)
