Cybersecurity researchers at ANY.RUN have uncovered a sophisticated attack leveraging the Diamorphine rootkit to deploy a cryptocurrency miner on Linux systems, highlighting the growing misuse of open-source tools in malicious campaigns.
The detailed analysis with ANY.RUN Sandbox exposes a multi-stage attack that employs advanced persistence and evasion techniques, posing a significant threat to Linux-based environments.
A Stealthy Multi-Stage Attack
The attack begins with a forked script, masquerading as a Python file, which deploys the Diamorphine rootkit—a Loadable Kernel Module (LKM) designed for Linux kernels across versions 2.6.x to 6.x on x86, x86_64, and ARM64 architectures.
.png
)
The rootkit intercepts system calls to conceal its activities while executing a carefully orchestrated sequence of steps. It starts by installing required dependencies and terminating competing processes, such as rival cryptocurrency miners, to maximize resource availability.
The script then downloads three malicious payloads over the internet: a disguised cryptominer named python-3.7.3.so, the mining payload cloud, and the Diamorphine rootkit package python37.tar.
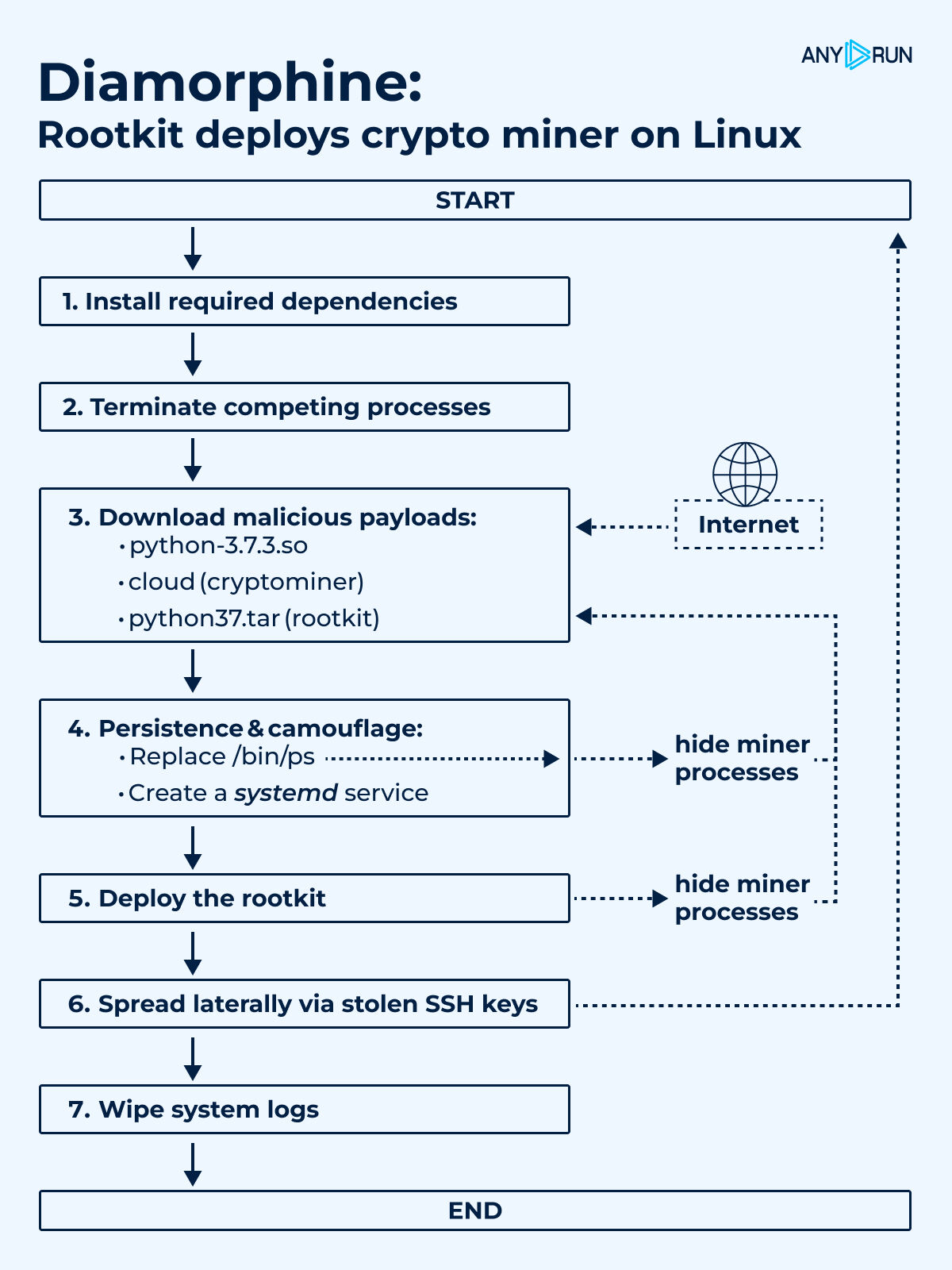
To ensure persistence, the script replaces the /bin/ps utility to hide its processes and establishes a systemd service, allowing the miner to restart after system reboots.
The Diamorphine rootkit is then loaded into the kernel, enabling it to manipulate system calls and further obscure the miner’s presence.
The attack also facilitates lateral movement by stealing SSH keys from the compromised host, using them to propagate to other systems on the network. Finally, the script wipes system logs to hinder forensic analysis, leaving minimal traces of its activity.
A key feature of this attack is its three-layer self-defense mechanism. By replacing the ps utility, installing the Diamorphine rootkit, and loading a library that intercepts system calls, the malware effectively hides its processes and activities from standard monitoring tools.
This layered approach makes detection and removal particularly challenging, as the rootkit becomes nearly invisible to traditional system utilities like lsmod—a problem exacerbated by the rootkit’s use of the list_del function, which removes it from the kernel module list, rendering rmmod ineffective.
Free Webinar: Gain practical insights that will help your team detect threats faster, triage alerts efficiently, and strengthen incident response. Register now and secure your spot! Open-Source Exploitation and Defensive Strategies
The Diamorphine rootkit and the miner are both built from open-source code hosted on GitHub, a platform increasingly exploited by malicious actors.
Originally developed by the user “m0nad,” Diamorphine has been repurposed for this campaign, demonstrating how accessible tools can be weaponized.
The attack’s use of stolen SSH keys for lateral movement amplifies its impact, enabling the malware to spread across networks and compromise additional systems.
The termination of competing miners also points to a competitive underground economy where attackers vie for control of infected hosts.
ANY.RUN’s analysis, conducted using their Linux VM, provides full visibility into the malware’s process activity and persistence mechanisms.
They’ve shared Indicators of Compromise (IOCs) and a TI Lookup query to help organizations identify fresh samples and strengthen their security posture.
This campaign underscores the rising threat to Linux environments, which are increasingly targeted due to their prevalence in servers, cloud infrastructure, and IoT devices. T
he abuse of open-source tools, combined with advanced evasion techniques like LKM rootkits, presents a formidable challenge for defenders.
ANY.RUN recommends leveraging tools like their platform for in-depth analysis, alongside proactive measures such as regular system updates, network monitoring for unusual SSH activity, and robust secrets management using solutions like GitHub Actions’ Secrets or HashiCorp Vault. Code audits with tools like TruffleHog can also help detect exposed credentials in repositories.
As Linux-targeted malware grows in sophistication, this Diamorphine rootkit campaign serves as a stark reminder of the need for vigilance.
Get 14 days of access to ANY.RUN’s advanced features and uncover threats faster -> Try ANY.RUN for 14 Days 


