The WordPress plugin WP Fastest Cache is vulnerable to an SQL injection vulnerability that could allow unauthenticated attackers to read the contents of the site’s database.
WP Fastest Cache is a caching plugin used to speed up page loads, improve visitor experience, and boost the site’s ranking on Google search. According to WordPress.org stats, it is used by more than a million sites.
Download statistics from WordPress.org show that more than 600,000 websites still run a vulnerable version of the plugin and are exposed to potential attacks.
Today, the WPScan team from Automattic disclosed the details of an SQL injection vulnerability, tracked as CVE-2023-6063 and with a high-severity score of 8.6, impacting all versions of the plugin before 1.2.2.
SQL injection vulnerabilities occur when software accepts input that directly manipulates SQL queries, leading to running arbitrary SQL code that retrieves private information or command execution.
In this case, the flaw impacts the ‘is_user_admin’ function of the ‘WpFastestCacheCreateCache’ class within the WP Fastest Cache plugin, which is intended to check if a user is an administrator by extracting the ‘$username’ value from cookies.
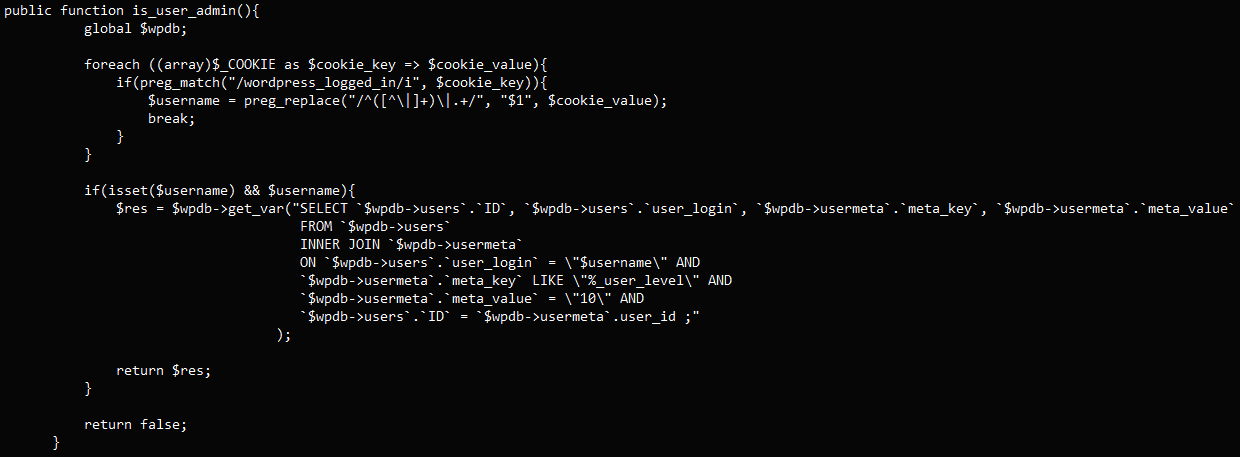
Because the ‘$username’ input isn’t sanitized, an attacker may manipulate this cookie value to alter the SQL query executes by the plugin, leading to unauthorized access to the database.
WordPress databases typically include sensitive information like user data (IP addresses, emails, IDs), account passwords, plugin and theme configuration settings, and other data necessary for the site’s functions.
WPScan will release a proof-of-concept (PoC) exploit for CVE-2023-6063 on November 27, 2023, but it should be noted that the vulnerability isn’t a complex one and hackers can figure out how to exploit it.
A fix has been made available by the WP Fastest Cache developer in version 1.2.2, released yesterday. All users of the plugin are recommended to upgrade to the latest version as soon as possible.





