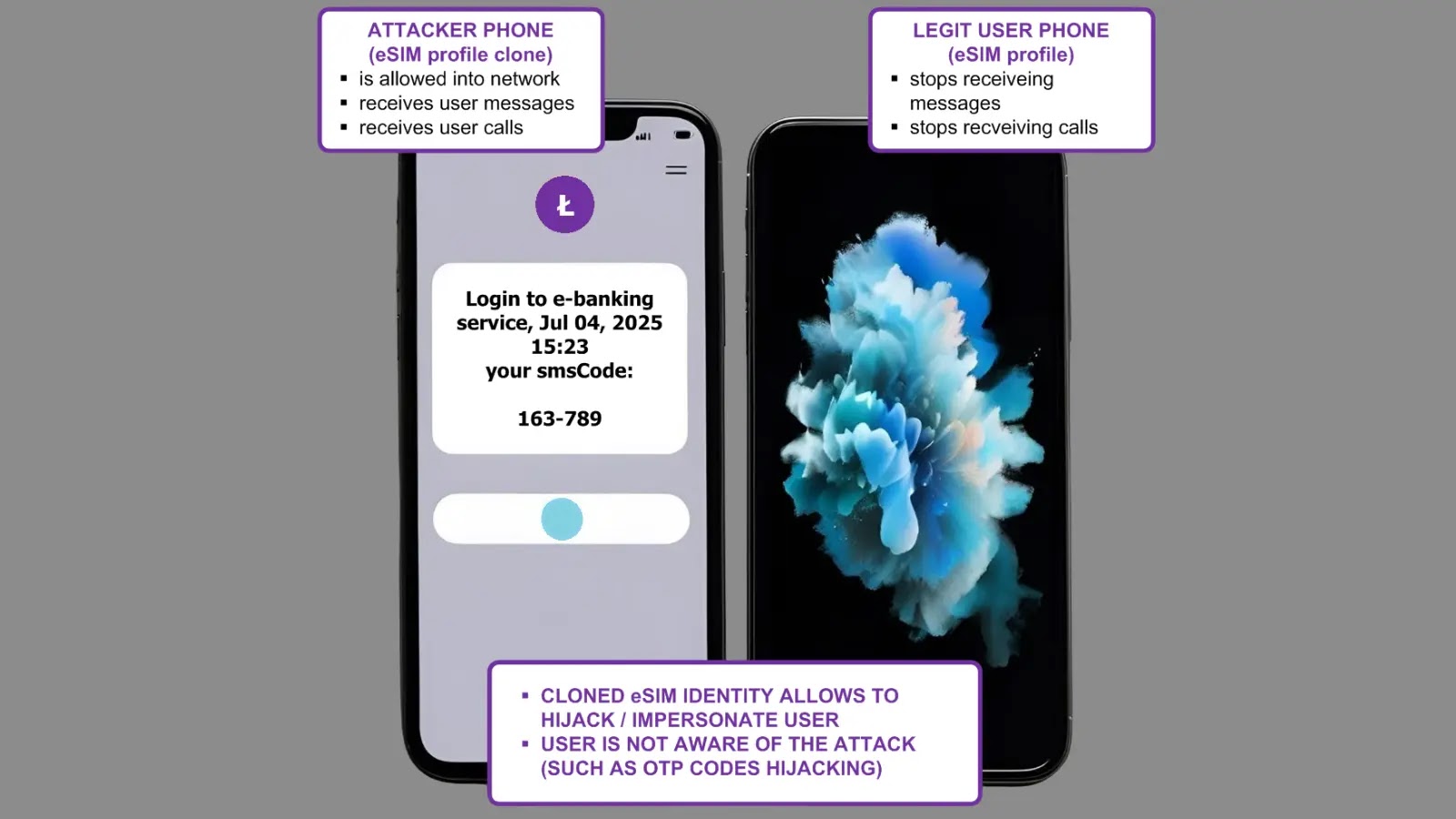
Xenomorph has been discovered with a new malware campaign targeting several United States and Spain institutions. This new campaign shows thousands of downloads of Xenomorph malware by victims.
Xenomorph is an Android malware that was discovered in February 2022 by Threat Fabric. According to previous malware campaigns, this Android malware was distributed using phishing webpages, tricking victims into installing malicious APKs.
However, a new list of victims belonging to several institutions in the US, Portugal, and multiple crypto wallets have been identified, showing consistency in the banking malware family.
Xenomorph Android Malware
Xenomorph malware is capable of performing a simple SMS manipulation and can go up to full device control, which is due to the use of a very powerful Automated Transfer System (ATS) framework that Remote access capabilities had obtained. The malware has been constantly being added with new features by its developers for additional functionalities.
Implementing AI-Powered Email security solutions “Trustifi” can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account Take Over, Business Email Compromise, Malware & Ransomware
Xenomorph uses “overlay” as its primary method for obtaining Personally Identifiable Information (PII), including usernames, passwords, credit card numbers, and much more. The modules that are available in Xenomorph, including the new functionalities, are listed below
| MODULE NAME | DESCRIPTION |
| notificationAccess | Grant notification access |
| grantPermissions | Automatically grants itself all permissions required |
| dozeModeDisableTypeA | Disable Doze mode (Xiaomi MIUI) – version 1 |
| dozeModeDisableTypeB | Disable Doze mode (Xiaomi MIUI) – version 2 |
| dozeModeDisableTypeC | Disable Doze mode (Xiaomi MIUI) – version 3 |
| dozeModeDisableTypeD | Disable Doze mode (Xiaomi MIUI) – version 4 |
| disablePlayProtect | Disable Play Protect |
| xiaomiAdminAccess | Get Admin Access Xiaomi |
| restrictUninstall_SamsungApi29 | Stop uninstall procedure in Samsung using API 29 (Android 10) |
| dismissSettingsAlerts_Generic | Dismiss Settings Alerts |
| restrictReset_Generic | Stop device reset |
| restrictReset_ByContentVid_SamsungApi30 | Stop device reset in Samsung using API 30 (Android 11) |
| restrictUninstall_ByClassName | Stop uninstall procedure based on Class name |
| restrictUninstall_Generic | Stop uninstall procedure |
| restrictAccessibilityDisable_Generic | Stop disabling of Accessibility Services privileges |
| restrictAdminRetrieve_XiaomiApi30 | Restrict retrieving Admin in Xiaomi using API 30 (Android 11) |
| restrictSettingsClicks_Generic | Restrict clicks in settings |
| defaultSmsApp-Alert | Interface with Default SMS settings Alert |
| defaultSmsApp-Role-ChangePrevention | Prevent removal of Default SMS Role |
| defaultSmsApp-Role | Obtain Default SMS role |
| defaultSmsApp-Settings | Set as Default SMS Handler |
| grantSystemWritePermissions | Grants system write permissions |
| getGoogle2FA | Gets Google Authenticator 2FA codes |
| grantWriteStoragePermissions | Grants write storage permissions (new functionality) |
Further investigations on this new malware revealed that threat actors have inserted several modules that are supported by Samsung and Xiaomi devices, as these two contribute to 50% of the whole Android market share.
New Capabilities
A few additional commands have been added from the previous versions of Xenomorph. The new commands were start_mimic (Start Mimic Function), stop_mimic (Stop Mimic Function), show_push (Enable antisleep push notification), and click on point (simulate touch on specific coordinates). This mimic function enables the malware to act as any other application and remove a malware-specific behavior that was not available in the previous version.
Furthermore, this malware was also found to be merged with RisePro stealer with Private Loader traces, which are some common Desktop-stealer malware. Additionally, the new version of Xenomorph also uses LummaC2, which was another well-known stealer.
Moreover, the communication with the C2 has been updated, replacing HTTP with raw TCP sockets over port 50500 for receiving commands and data exfiltration.
A complete report has been published by Threat Fabric, which provided detailed information about the malware, distribution, code analysis, C2 communication, their old targets, new functionalities, and other information.
Indicators of Compromise
Xenomorph Samples
| HASH (SHA256) | APP NAME | PACKAGE NAME |
| e2646afca109162f66b117ca8a7feed0272ab6d8822132dafd2d54d7553cbfde | Chrome | com.peace.frequent |
| 259e88f593a3df5cf14924eec084d904877953c4a78ed4a2bc9660a2eaabb20b | Chrome | com.mtnyrvojt.qtbxtwjnq |
| 257f041d1b6ed82808cd8ef07ec84cf141c38e5374b654de46879a3bc180c79c | Chrome | com.uhtvqsutg.igogiciut |
Xenomorph C2 servers
| SERVER URL/IP | ROLE |
| airlinesimulator[.]io | Overlay Server |
| fobocontentplus[.]online | C2 Server |
| fobocontentplus[.]top | C2 Server |
| fobocontentplus[.]site | C2 Server |
| 92l[.]info | Phishing Server |
Protect yourself from vulnerabilities using Patch Manager Plus to quickly patch over 850 third-party applications. Take advantage of the free trial to ensure 100% security.