A fresh wave of spam is hitting inboxes worldwide, with users reporting that they are once again being bombarded by automated emails generated through companies’ unsecured Zendesk support systems.
Some recipients say they are receiving hundreds of messages with strange or alarming subject lines.
Users flooded with bogus ‘Activate account’ emails
Since yesterday, numerous social media users say they have begun receiving large bursts of emails with subject lines such as “Activate your account” and similar support-style notifications appearing to originate from different companies.

Recipients say the messages arrive in rapid succession and look like legitimate automated replies from customer support portals, despite never signing up or submitting a ticket.
“Anyone else getting a slew of failed account & support sign-up emails?” posted security researcher Jonathan Leitschuh on LinkedIn.
“Someone is DDoSing Zendesk support ticketing systems and other account creation processes across the internet with my email right now. Anyone know what the attacker is hoping to achieve here?”
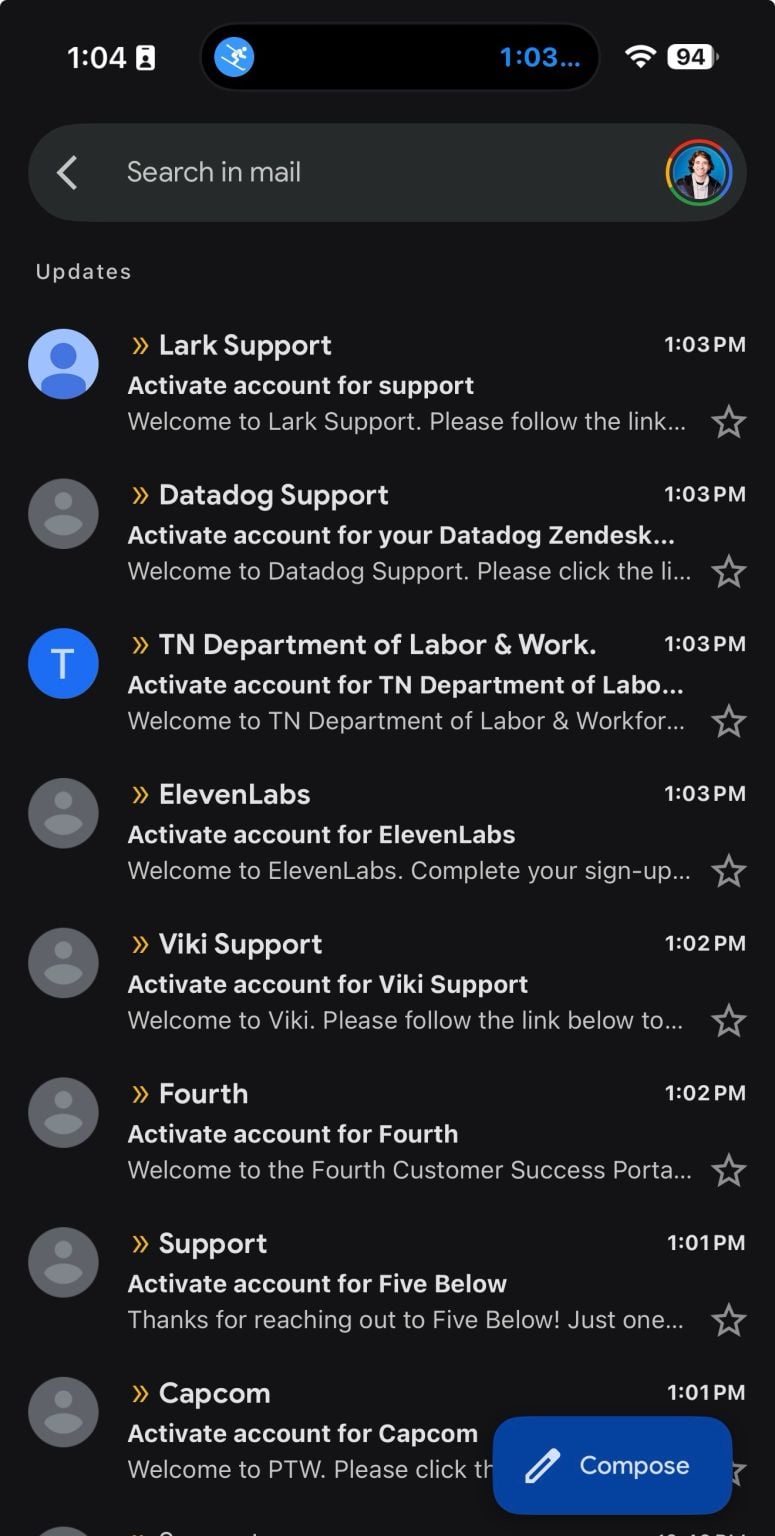
Several users took to social media [1, 2, 3] to report their inboxes overflowing with similar messages:
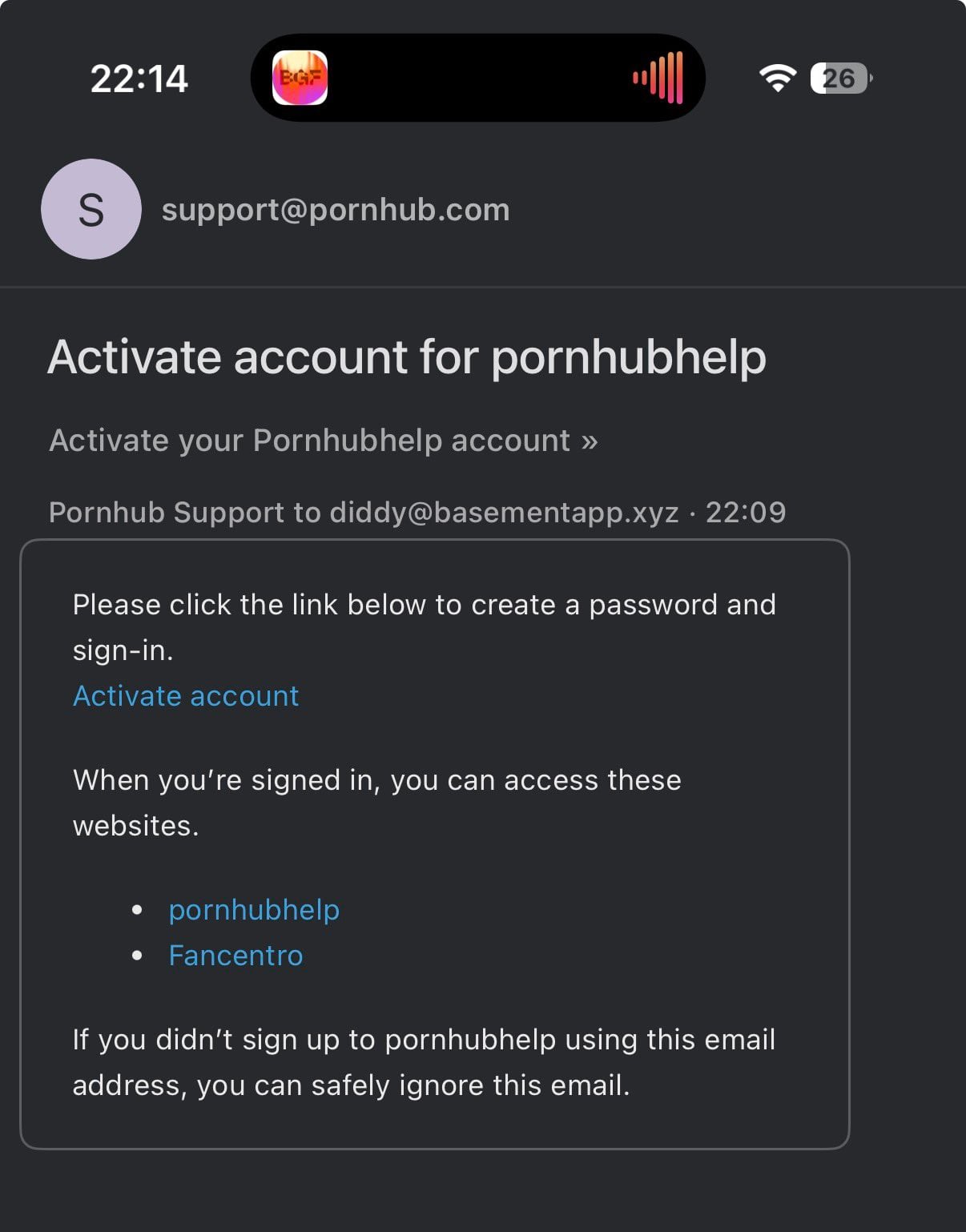
(@nickvernij on X)
Similar to the previous incident, the emails appear to be sent from real companies’ Zendesk instances, allowing them to bypass spam filters and land directly in inboxes.
The activity strongly suggests attackers are once again abusing Zendesk ticket submission forms to trigger confirmation emails to large lists of addresses.
What happened in January
In January, a massive global spam wave was traced to attackers abusing Zendesk’s ability to let unverified users submit support tickets.
Each ticket automatically generates a confirmation email to the email address entered, enabling threat actors to turn exposed support portals into large-scale spam relays.
The earlier campaign began around January 18 and affected several companies, with some recipients receiving hundreds of messages with bizarre or alarming subject lines.
Multiple companies had confirmed they were affected by the spam wave, including Dropbox and 2K, who responded to tickets to tell recipients not be concerned and to ignore the emails.
Zendesk had earlier told BleepingComputer that it had introduced new safety features on their end to detect and stop this type of spam in the future.
“We’ve introduced new safety features to address relay spam, including enhanced monitoring and limits designed to detect unusual activity and stop it more quickly,” Zendesk said at the time.
“We want to assure everyone that we are actively taking steps – and continuously improving – to protect our platform and users.”
In a December 2025 advisory, Zendesk had also warned customers about this type of abuse, explaining that attackers were sending what it called “relay spam” by abusing Zendesk instances.
The company said earlier that organizations could prevent this type of abuse by restricting ticket creation to only verified users and removing placeholders that allow any email addresses or ticket subject to be used.
The renewed activity suggests attackers may still be able to abuse exposed Zendesk ticket portals despite the safeguards introduced earlier this year.
BleepingComputer has contacted Zendesk for comment and will update this story if we receive a response.

Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.



