A critical path traversal flaw in ZendTo has been assigned CVE-2025-34508 researchers discovered that versions 6.15–7 and prior enable authenticated users to manipulate file paths and retrieve sensitive data from the host system.
This issue underscores the persistent risk in web-based file transfer applications.
Path Traversal Vulnerability (CVE-2025-34508)
ZendTo is a PHP-driven dropoff or pickup service that allows any registered user to upload files for sharing. During the “dropoff” process, two variables chunkName and tmp_name determine how file uploads are staged and moved.
Horizon3.ai reports that the server-side sanitization routine strips non-alphanumeric characters from chunkName, but if an attacker supplies a chunkName comprised entirely of non-alphanumeric characters, the sanitization leaves an empty or dot-only string.
This results in a chunkPath pointing to the root uploads directory rather than a unique temporary file:
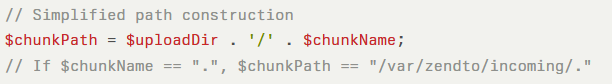
Once chunkPath is established, the code concatenates a user-controlled tmp_name to relocate the file into the target dropoff directory:
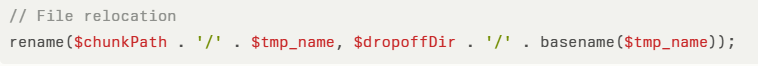
Because tmp_name is not sanitized, attackers can embed directory traversal sequences.
Downloading this file exposes the application’s log data, including dropoff claim IDs, creating the way to enumerate and exfiltrate any user-uploaded content or critical system files.
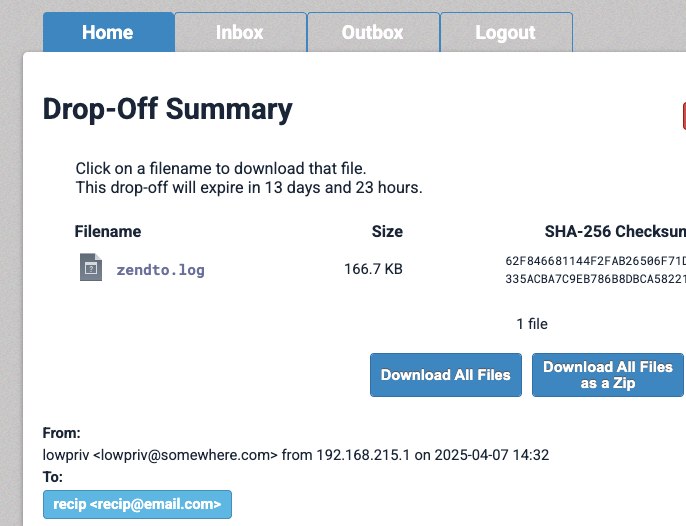
Drop-off Summary
| Risk Factors | Details |
| Affected Products | ZendTo versions 6.15–7 and prior |
| Impact | Arbitrary file read and information disclosure |
| Exploit Prerequisites | Low-privilege authenticated user |
| CVSS 3.1 Score | 7.8 (High) |
Mitigation
In default installations, file access is limited to the www-root user’s permissions, yet this typically encompasses all uploaded content. Beyond user files, adversaries could target the ZendTo database or source code, potentially causing a denial-of-service.
Although CVE-2025-34508 requires authentication, the minimal barrier allows low-privilege users to perform arbitrary file reads.
Administrators are strongly urged to upgrade immediately. The fix implements stricter validation on both chunkName and tmp_name, ensuring only safe, expected filenames are processed.
This disclosure follows high-profile incidents involving MOVEit Transfer (CVE-2023-34362), Accellion FTA (CVE-2021-27104), and GoAnywhere MFT (CVE-2023-0669), highlighting that file-sharing platforms remain prime targets.
Organizations must maintain vigilant patch management and conduct regular security reviews of their file transfer applications.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
