In a recent development on an underground forum, a user is actively promoting the sale of Zeppelin2 ransomware, offering both its source code and a cracked version of its builder tool. This malicious software, known for its destructive capabilities, has caught the attention of cybersecurity experts and law enforcement agencies worldwide.
The forum post claims that the user successfully cracked the Zeppelin2 builder tool, originally designed to encrypt data, by bypassing its security measures. The post showcases screenshots of the source code and highlights the intricate details of the build process, revealing that the ransomware employs Delphi as its programming language.
The Cracked Version of Zeppelin2 Ransomware Builder Tool
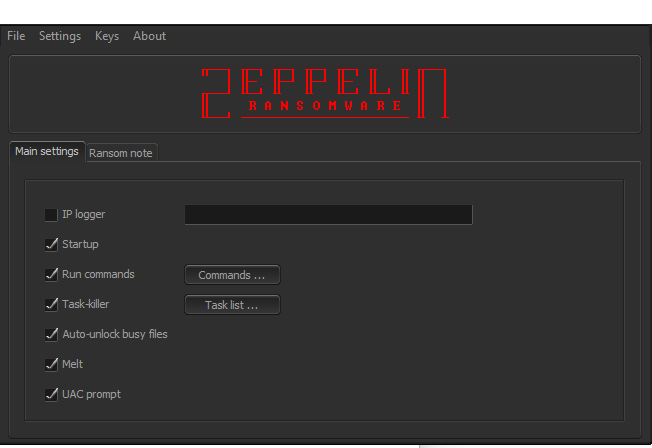
The Zeppelin2 ransomware builder tool, promoted by this threat actor, boasts various features including file settings, ransom notes, IP logging, startup commands, task killers, and auto-unlocking busy files. The threat actor emphasizes the ransomware’s ability to encrypt files comprehensively, making data recovery impossible without a unique private key held by the attackers.
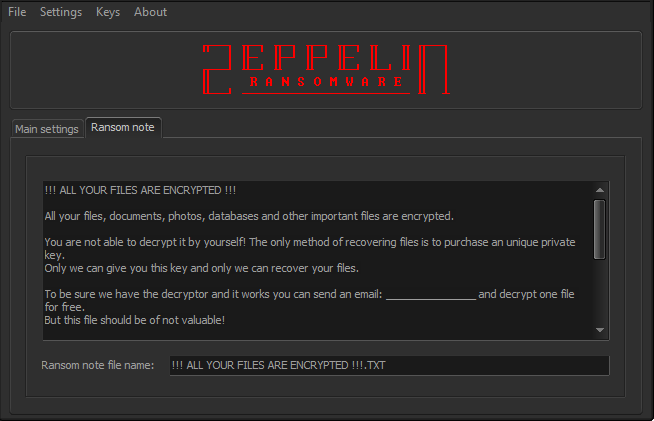
Once the ransomware completes its encryption process, victims are confronted with a ransom note declaring the encryption of all their files. The note instructs victims to contact the attackers via email and provides a method for testing the legitimacy of the decryptor by sending a non-valuable file.

According to reports, Zeppelin2 ransomware demands ransom payments in Bitcoin, with extortion amounts ranging from several thousand dollars to over a million dollars. The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have jointly issued a cybersecurity advisory to address the Zeppelin2 threat.
Who is the Zeppelin2 Ransomware Group?
Zeppelin2 has been employed by threat actors since 2019, continuing at least until June 2022. The targets of this ransomware-as-a-service (RaaS) model span diverse sectors, including defense contractors, educational institutions, manufacturers, technology companies, and notably, organizations in the healthcare and medical industries.
The ransomware’s modus operandi involves exploiting vulnerabilities such as remote desktop protocol (RDP) exploitation, SonicWall firewall vulnerabilities, and phishing campaigns to gain access to victim networks. Before unleashing the Zeppelin2 ransomware, threat actors meticulously map and enumerate the victim’s network, identifying critical data enclaves, including cloud storage and network backups.
As is customary with ransomware groups, Zeppelin2 operators exfiltrate sensitive corporate data, intending to make it accessible to buyers or the public should the victim resist complying with their demands.
Notably, the FBI has observed instances where Zeppelin2 actors execute their malware multiple times within a victim’s network, generating different IDs or file extensions for each attack instance, requiring multiple unique decryption keys.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.