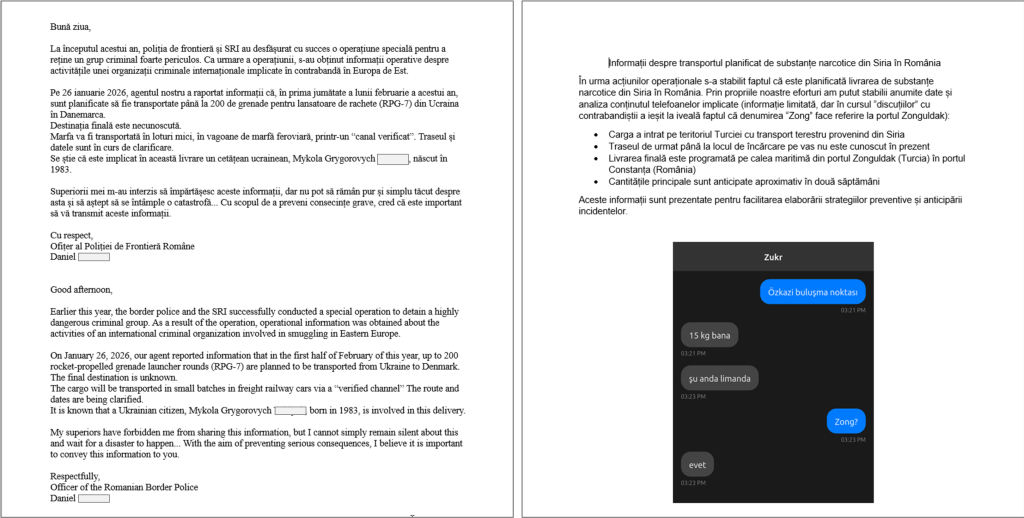
Microsoft disclosed a critical zero-day vulnerability in Office products on January 26, 2026, tracked as CVE-2026-21509, with active exploitation in the wild confirmed.
The vulnerability enables attackers to deploy sophisticated malware through malicious document files, targeting government organizations and critical infrastructure.
| Indicator Type | Value |
|---|---|
| CVE | CVE-2026-21509 |
| Malicious Domains | freefoodaid[.]com, wellnesscaremed[.]com, wellnessmedcare[.]org |
| C2 Infrastructure | *.filen.net, *.filen.io (146.0.41.204-208, 146.0.41.231-234) |
| Malicious Files | BULLETEN_H.doc, Consultation_Topics_Ukraine(Final).doc |
| Persistence Task | OneDriveHealth |
| Threat Actor | UAC-0001 (APT28) |
Attack Campaign Emerges Within 48 Hours
Security researchers discovered the first weaponized document on January 29, 2026, just three days after Microsoft’s advisory.
The malicious file, titled “Consultation_Topics_Ukraine(Final).doc,” masqueraded as European Union COREPER committee materials regarding Ukraine consultations.
Metadata analysis revealed the document was created on January 27 at 07:43 UTC, indicating rapid exploit development following the vulnerability disclosure.
The same day, threat actors launched a coordinated phishing campaign impersonating Ukraine’s Hydrometeorological Center.
The malicious emails, containing a weaponized DOC file named “BULLETEN_H.doc,” were distributed to over 60 email addresses, primarily targeting Ukrainian central executive government agencies.
Technical Exploitation Chain
Opening the malicious document in Microsoft Office initiates a WebDAV connection to external infrastructure, which downloads a shortcut file containing executable code.
The payload deploys several components, including a DLL file, “EhStoreShell.dll,” disguised as an Enhanced Storage Shell Extension, an image file, “SplashScreen.png,” containing shellcode, and registry modifications that implement COM hijacking via CLSID {D9144DCD-E998-4ECA-AB6A-DCD83CCBA16D}.
The malware establishes persistence via a scheduled task named “OneDriveHealth” that terminates and restarts the explorer.exe process.
This triggers the malicious DLL to execute shellcode from the image file, ultimately deploying the COVENANT post-exploitation framework.
The attack infrastructure leverages legitimate cloud storage service Filen (filen.io) for command-and-control communications, complicating detection efforts.
Security analysts identified three additional exploit documents in late January 2026, targeting European Union organizations.
Analysis of embedded URLs, document structure, and infrastructure patterns suggests attribution to UAC-0001, also tracked as APT28, a Russian state-sponsored threat group.
One attack on January 30, 2026, used a domain registered that day, demonstrating the operation’s speed.
The rapid weaponization timeline and targeting of government entities indicate coordinated espionage operations.
Microsoft recommends immediate Windows registry configuration changes and the application of available security updates.
Organizations should monitor or block network connections to FileNet infrastructure and implement enhanced email filtering for Office documents.
Exploiting the vulnerability before widespread patch deployment creates an extended risk window. Security teams should prioritize Microsoft Office updates and implement recommended mitigations to prevent compromise.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




