The cybersecurity world is on the brink of a revolution, driven by quantum computing. Quantum computers can also break the encryption systems we depend on daily while powering breakthroughs in medicine, artificial intelligence, and beyond. Organizations must adapt fast as traditional perimeter-based security becomes obsolete. Enter Zero Trust Architecture (ZTA), a proactive, resilient strategy, which is ready to defend digital ecosystems against the looming quantum threat.
The Quantum Threat: Breaking Cryptography as We Know It
Quantum computers are not only faster; they are a different kind of technology. Using quantum mechanics, they can solve some problems in seconds, which would take millions of years for classical computers. One alarming example is Shor’s algorithm, which can break most modern cryptographic protocols, including RSA and Elliptic Curve Cryptography (ECC). These algorithms protect everything from online banking to military communications and networks.
Experts predict that large-scale, fault-tolerant quantum computers that can run Shor’s algorithm may appear within 10-15 years (according to the estimates of IBM and Google quantum teams). When that happens, the attackers will be able to decrypt the sensitive data, forge digital identities, and compromise critical infrastructure. The clock is ticking.
Fig. 1: Quantum Computing’s Threat to Encryption
Why Zero-Trust Architecture Is the Answer
Conventional security postures are based on the assumption that everything within the network is secure, which is incorrect in the current environment. Zero-Trust Architecture changes this perspective with the help of a single principle: Never Trust, Always Verify. It means that every user, device, and application is considered a potential threat and requires confirmation of its good intentions.
Here’s why ZTA stand s out:
- Least Privilege Access: Only necessary rights are granted to users and devices. If a breach does occur, it is limited in scope.
- Continuous Verification: It is not a static process of trusting. It happens in real time using behavior analysis, device status, and others.
- Micro-Segmentation: The networks are segmented into separate compartments that prevent the attacker from moving freely throughout the network.
- Encryption Everywhere: The data is encrypted in the rest, in transit and in use – quantum or not, it is very difficult to crack.
- Comprehensive Monitoring: Real-time logging and analytics to identify anomalies before they become a crisis.
For instance, Google’s BeyondCorp initiative, a real ZTA implementation, migrated security from network perimeter to device and user verification and successfully adapted to a cloud-first environment. It is not just a reduction of the attack surface; it is the creation of a quantum-ready fortress.

Fig. 2: Traditional Security vs. Zero-Trust Architecture
Quantum-Resistant Cryptography: The Perfect Partner
ZTA is powerful, but it is not the only solution. To respond fully to quantum threats, we need quantum-resistant cryptography – the algorithms intended for use against quantum attacks. The National Institute of Standards and Technology (NIST) is the leading body in standardizing options like these:
- Lattice-Based Cryptography: The cryptography based on complex lattice mathematics. CRYSTALS – Kyber (NIST selected) is one of them.
- Hash-Based Cryptography: Cryptography based on quantum-proof hash functions. SPHINCS+ is excellent.
- Code Based Cryptography: The security of this system is based on error correcting codes. As an example, McEliece has proved its effectiveness.
- Multivariate Cryptography: It solves complex equations. Rainbow is a notable scheme.
- Isogeny-Based Cryptography: It uses secure key exchange using elliptic curve isogenies.
These combined with ZTA provide a layered defense. Picture a cybersecurity onion: peel one layer, and another stands strong.
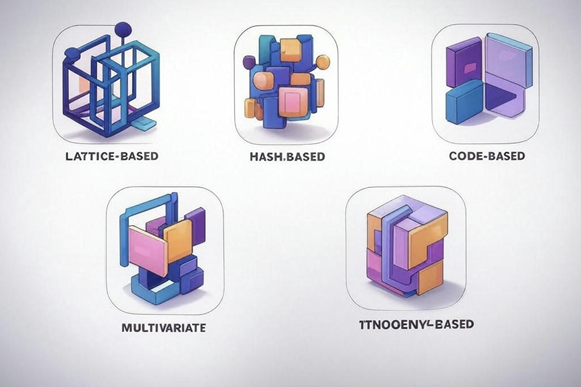
Fig. 3: Five Pillars of Quantum-Resistant Cryptography
Challenges on the Horizon
ZTA and quantum-resistant cryptography are not something that can be implemented easily. The challenges organizations encounter in the process are listed below:
- Legacy Systems: Many organizations are using outdated technologies that are incompatible with ZTA or new cryptography. For instance, a bank using 20-year-old mainframes would need a costly overhaul to integrate lattice-based encryption.
- Performance Tradeoffs: Some quantum-resistant algorithms like CRYSTALS-Kyber can increase the computational complexity that can slow down the systems or increase the operational costs.
- Interoperability: New systems must be compatible with the old ones and with the partners’ setups without disrupting the business processes.
- Cultural Resistance: This is so because ZTA is a cultural shift. For instance, people who are used to the open network will not like the constant verification.
- Evolving Threats: Quantum tech is developing unexpectedly, which necessitates the need for organizations to be flexible.
However, the cost of doing nothing is greater than the cost of doing something. A single quantum breach could cripple a company or a country.

Fig. 4: Hurdles in Adopting Quantum-Ready Security
Collaboration: The Path Forward
No one faces this alone. This is where governments, industries and academia must come together. NIST’s Post Quantum Cryptography Standardization Project is a perfect example of how it has brought together people from all over the world to build future proof defenses. They should begin now to identify vulnerabilities, implement ZTA pilots, and engage with peers.
The Future of Cybersecurity
Quantum computing is a two-edged sword: a great invention and a cyber threat. With the help of Zero-Trust Architecture and quantum-immune cryptography, organizations can defend themselves. The way is long, but the action should be taken now for the future. Ready to fortify your defenses? The quantum era waits for no one.
About the Author
 Dinesh Besiahgari is a Frontend Engineer II at Amazon Web Services, specializing in developing scalable, user-centric web applications. He has a strong background in AI, IoT, and machine learning, with multiple research papers published in IEEE, Springer and patents in advanced technologies. Dinesh’s work has been featured in leading industry publications such as Forbes, Cybernews, PYMNTS and more. A global speaker and judge at prestigious tech events, he is widely recognized for his contributions through numerous awards. He is passionate about building secure, intelligent systems and AI-driven platforms that push the boundaries of innovation.
Dinesh Besiahgari is a Frontend Engineer II at Amazon Web Services, specializing in developing scalable, user-centric web applications. He has a strong background in AI, IoT, and machine learning, with multiple research papers published in IEEE, Springer and patents in advanced technologies. Dinesh’s work has been featured in leading industry publications such as Forbes, Cybernews, PYMNTS and more. A global speaker and judge at prestigious tech events, he is widely recognized for his contributions through numerous awards. He is passionate about building secure, intelligent systems and AI-driven platforms that push the boundaries of innovation.
Dinesh can be reached at Dinesh Besiahgari




