A newly surfaced mobile spyware platform called ZeroDayRAT is rapidly gaining traction across underground Telegram channels.
ZeroDayRAT is designed to give attackers complete remote control over both Android and iOS devices, supporting versions from Android 5 through 16 and iOS up to version 26, including the latest iPhone 17 Pro.
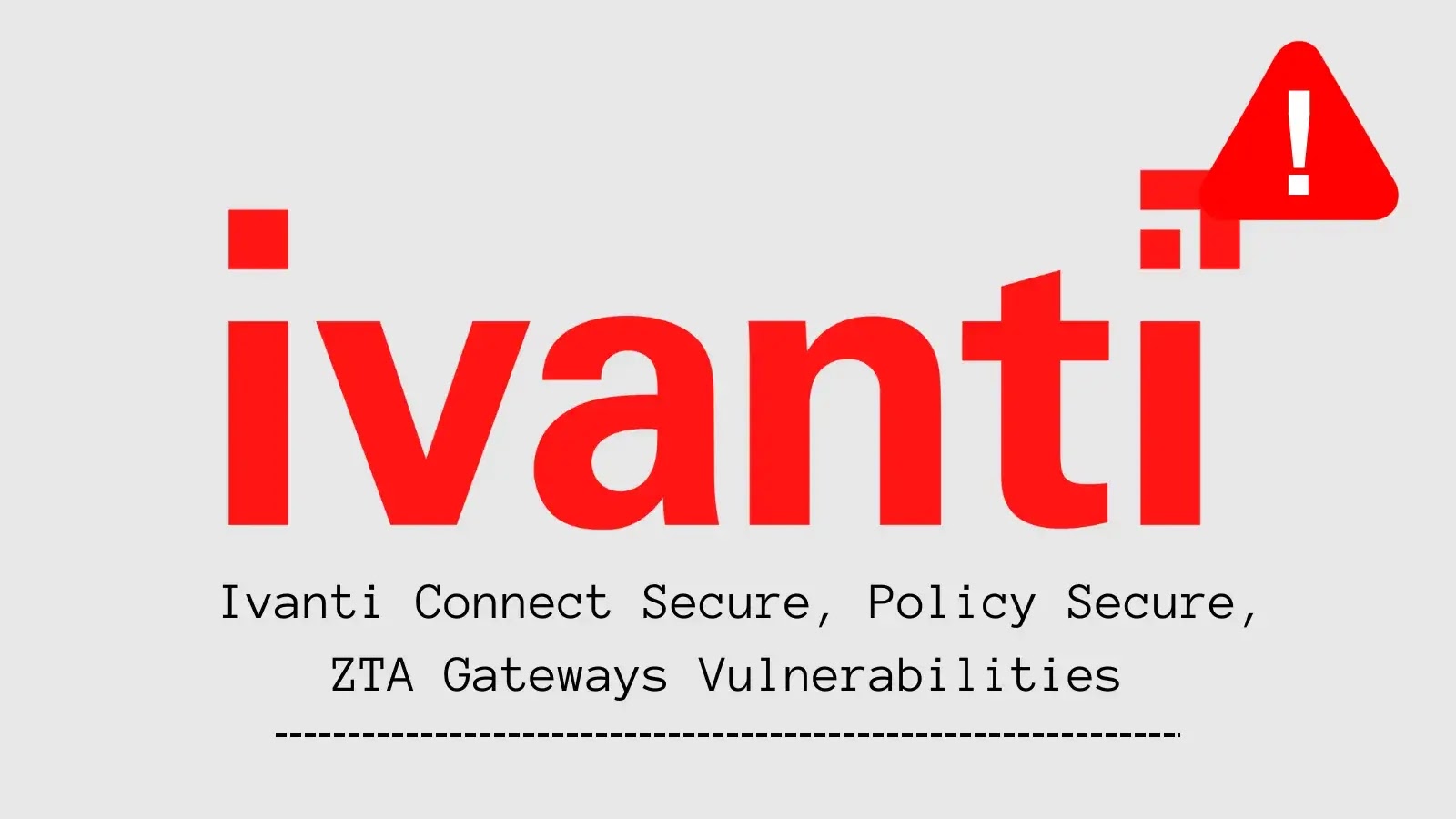
The panel interface allows the operator to manage multiple infected devices worldwide as seen in sample dashboards showing victims in India and the U.S.enabling real-time tracking and data theft through a browser interface.
Infection usually begins with smishing text messages carrying links to fake apps that mimic trusted brands or services.
Other infection paths include phishing emails, malicious APKs, fake app stores, or even shared files over messaging platforms like WhatsApp and Telegram.
First observed on February 2nd, this toolkit is openly sold with dedicated channels for sales, support, and live updates, giving cybercriminals a one-stop shop to run full-scale surveillance campaigns without any technical expertise.
Once a device is infected, the attacker gains a full device overview: model, OS, carrier details, dual SIM numbers, battery levels, recent messages, and app usage patterns.
From this alone, an operator can map when a user is active, which apps they use, and whom they communicate with, revealing a complete behavioral profile.
ZeroDayRAT Exploit
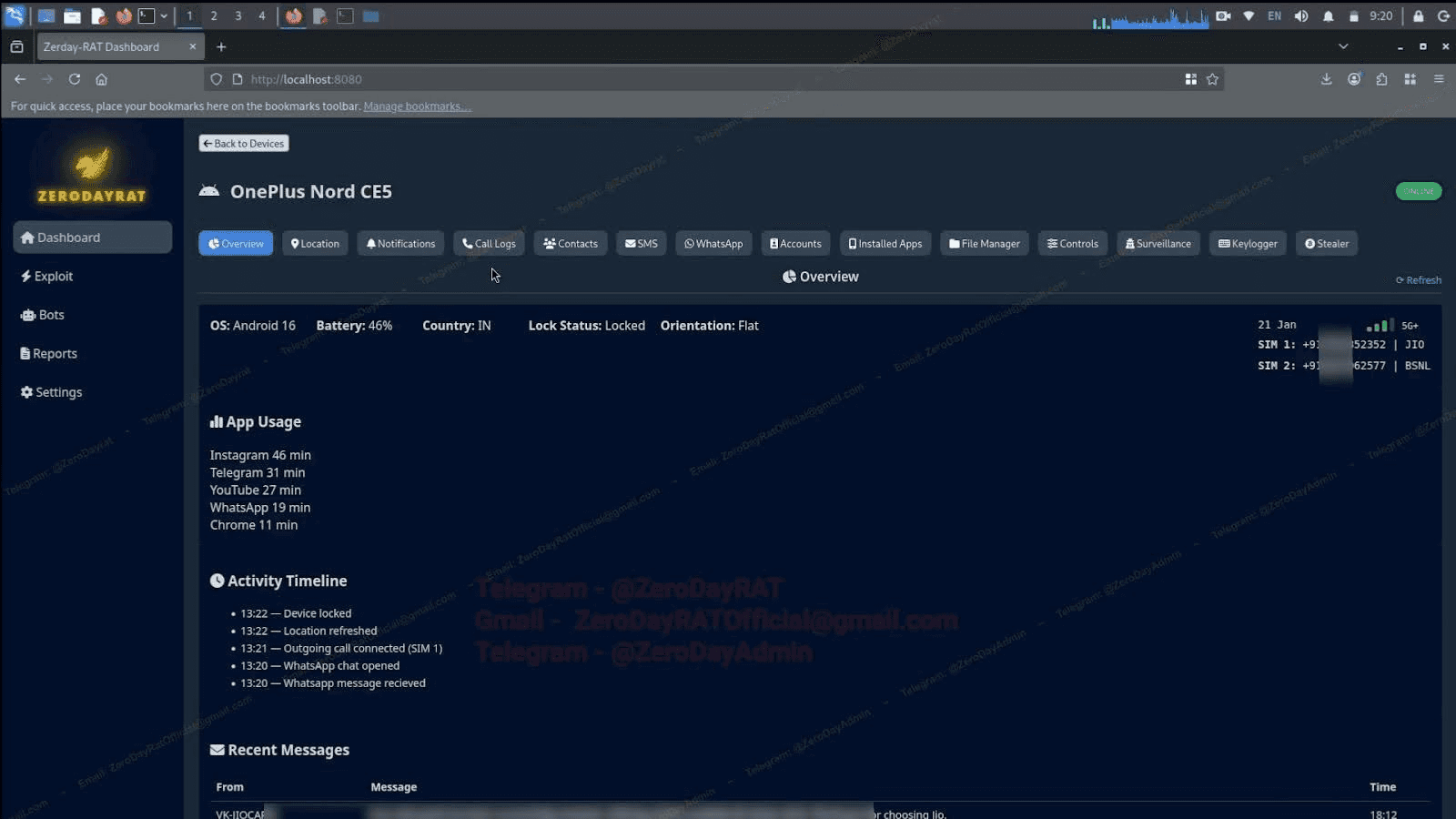
Each data stream has a dedicated tab for granular monitoring. The Location tab shows GPS coordinates on an embedded Google Map, logging both real-time movements and travel history.
The Notifications tab displays every app alert from WhatsApp and Instagram to banking apps giving the attacker passive visibility into nearly all phone activity.
The Accounts tab lists every service linked to the device, including Google, Facebook, Telegram, Amazon, and Paytm. With this data, attackers can perform account takeovers or launch targeted phishing.
Meanwhile, SMS controls allow interception of messages and OTP codes, effectively bypassing SMS-based two-factor authentication.
ZeroDayRAT also provides live surveillance through the camera and microphone, as well as keystroke logging with live screen previews. These tools enable attackers to monitor what victims see, type, and say in real time turning an ordinary smartphone into a surveillance device.
Financial Theft Modules
Beyond spying, ZeroDayRAT includes powerful theft tools. The crypto stealer targets digital wallets like MetaMask and Binance, while clipboard injection silently redirects cryptocurrency transactions.
A bank stealer module captures credentials from financial apps and UPI services such as PhonePe and Google Pay, using overlay attacks to steal data directly.
ZeroDayRAT represents a dangerous shift advanced mobile spying kits, once reserved for state-sponsored use, are now traded openly to anyone with money.
For individuals, this means total privacy loss and possible financial compromise. For enterprises, an infected employee’s phone could expose credentials, communications, and corporate data.
Security experts urge users to avoid sideloading apps, verify download sources, and enforce mobile threat defense tools at both personal and organizational levels. As ZeroDayRAT spreads, defending mobile endpoints is no longer optional it’s essential.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.