Zyxel has published a security advisory containing guidance on protecting firewall and VPN devices from ongoing attacks and detecting signs of exploitation.
This warning comes in response to multiple reports of widespread exploitation of the CVE-2023-28771 and the exploitability and severity of CVE-2023-33009 and CVE-2023-33010, all impacting Zyxel VPN and firewall devices.
“Zyxel has been urging users to install the patches through multiple channels, including issuing several security advisory newsletters to registered users and advisory subscribers; notifying users to upgrade via the Web GUI’s push notification for on-premises devices; and enforcing scheduled firmware upgrades for cloud-based devices that haven’t yet done so,” warns Zyxel’s security advisory.
Malware botnets are currently exploiting CVE-2023-28771 to perform unauthenticated remote command execution via specially crafted malicious packets and infect devices.
The other two flaws, CVE-2023-33009 and CVE-2023-33010, are buffer overflow bugs that could allow unauthenticated attackers to impose a denial of service state on vulnerable devices or perform remote code execution.
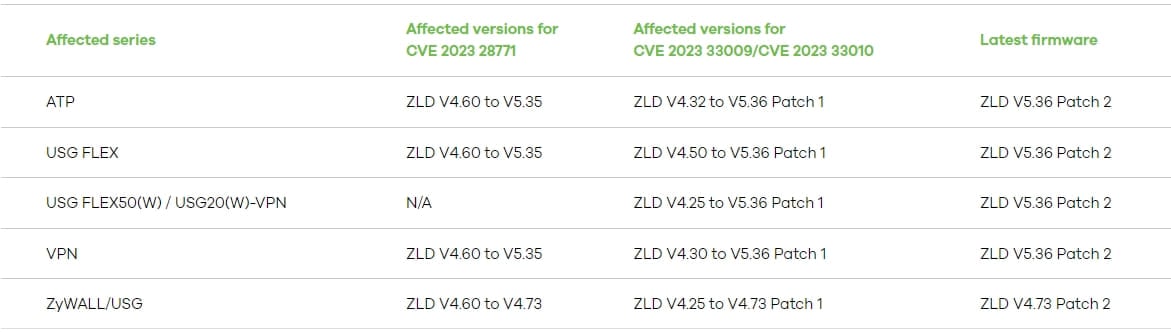
The following table summarizes the impacted Zyxel products, vulnerable firmware versions, and target security updates for each.
Signs of trouble and mitigation
Zyxel says that strong indicators of a hacked device include unresponsiveness and the inability to reach the device’s web user interface or SSH management panel.
Frequent network interruptions and unstable VPN connectivity should also be treated as red flags and investigated.
The recommended action is to apply the available security updates, which are ‘ZLD V5.36 Patch 2’ for ATP – ZLD, USG FLEX and VPN- ZLD, and ‘ZLD V4.73 Patch 2’ for ZyWALL.
However, if updating is impossible now, system admins are advised to implement certain mitigation measures.
The first effective defense measure is to disable HTTP/HTTPS services from WAN (Wide Area Network). This should make vulnerable endpoints unreachable by remote attackers.
If admins need to manage devices over WAN, they should enable ‘Policy Control’ and add rules allowing only trusted IP addresses to access the devices.
Enabling GeoIP filtering is also recommended to limit access to users/systems based on trusted locations.
Finally, Zyxel recommends disabling UDP Port 500 and Port 4500 if IPSec VPN isn’t needed, shutting another avenue for attacks.
It is important to remember that attacks against the listed products are currently underway, and they’re only expected to increase in volume and severity, so taking action to protect your devices as soon as possible is imperative.
