Phishing attackers abuse TLDs like .li, .es, and .dev to hide redirects, steal credentials, and bypass detection. See top domains flagged by ANY.RUN in 2025.
Some phishing sites don’t need fancy tricks, just the right domain name. And you won’t always spot it until it’s too late.
Hackers have become masters at abusing certain Top-Level Domains (TLDs), like .com, .ru, or .dev, to host phishing pages, fake login portals, or malware redirects. While many TLDs are used for legitimate purposes, others are repeatedly exploited to trick users into handing over sensitive information.
Recent sandbox data from ANY.RUN highlights the 20 TLDs most frequently used in phishing campaigns in 2025. These domains are central to fake delivery scams, credential harvesting pages, and multi-stage redirect chains.
Which TLD is the Most Abused by Attackers?
According to ANY.RUN’s 2025 data, the .li domain ranks #1 in phishing abuse by ratio. An alarming 57% of observed .li domains were flagged as malicious. But here’s the twist: many of them don’t host phishing content directly. Instead, .li is widely used as a redirector; a middleman that sends unsuspecting users to fake login pages, malware downloads, or credential harvesting sites.
These indirect roles in phishing chains often go unnoticed by detection tools, making .li a quiet but dangerous enabler in many attacks.
For instance, in this ANY.RUN analysis session, we see a .li domain in action. At first glance, it seems harmless.
View analysis session
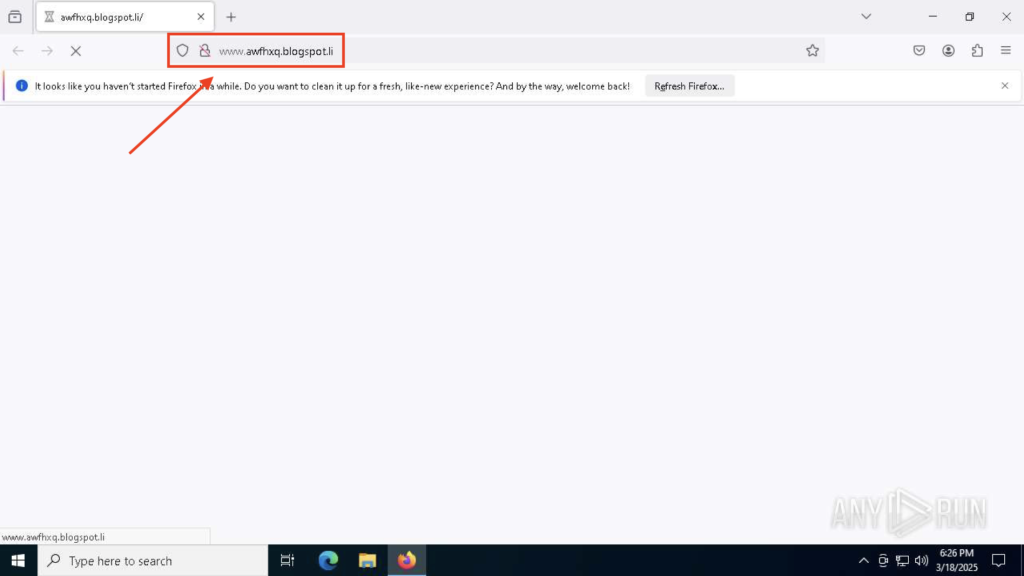
As soon as it loads, the browser is quietly redirected from the .li domain to a .com version of the same name, maintaining a sense of legitimacy before finally landing on a phishing page tied to a crypto-mining scam.
There’s no flashy malware or obvious warning sign, just a quick, invisible switch that hands the user over to an attacker-controlled site.

This kind of redirection tactic makes .li especially slippery. But it can be easily spotted inside the ANY.RUN sandbox, where analysts can trace every redirection in real-time, uncover hidden phishing paths, and extract critical IOCs before users ever click the link. Because the malicious content often lives one hop away, tools that rely only on domain blacklists or static scans frequently miss it.
| Gain control over phishing investigations with full redirection paths, behaviour traces, and real-time analysis. Start analyzing with ANY.RUN. |
Other Commonly Abused TLDs in Phishing Campaigns
While .li tops the list by ratio, it’s far from the only domain zone being misused by attackers. Several others stand out due to the high frequency and recurring use in phishing campaigns.
.es: Fake Logins and Delivery Scams
.es, Spain’s country code TLD, has become a popular choice for attackers running credential phishing and fake delivery scams. Phishing pages using .es often mimic familiar services like Microsoft 365 or postal couriers, tricking users into entering their login credentials or payment information. The domains feel local and trustworthy, making them especially dangerous for Spanish-speaking users.

.sbs: Cheap Domains for Credential Harvesting
Because .sbs domains are incredibly cheap to register, attackers use them for quick-hit phishing campaigns. These domains often host fake tracking pages, urgent payment requests, or impersonate corporate portals, each crafted to steal login details or credit card numbers. The low barrier to entry makes .sbs a go-to for disposable phishing infrastructure.
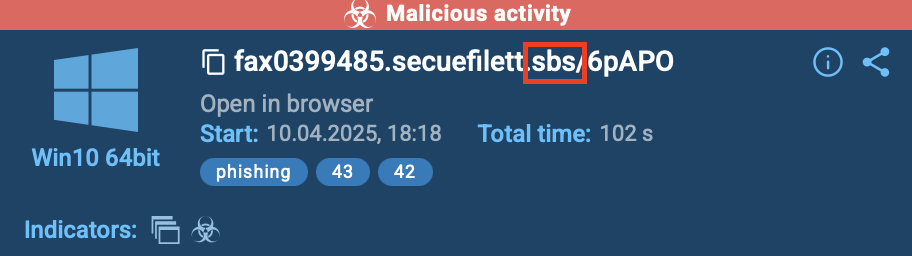
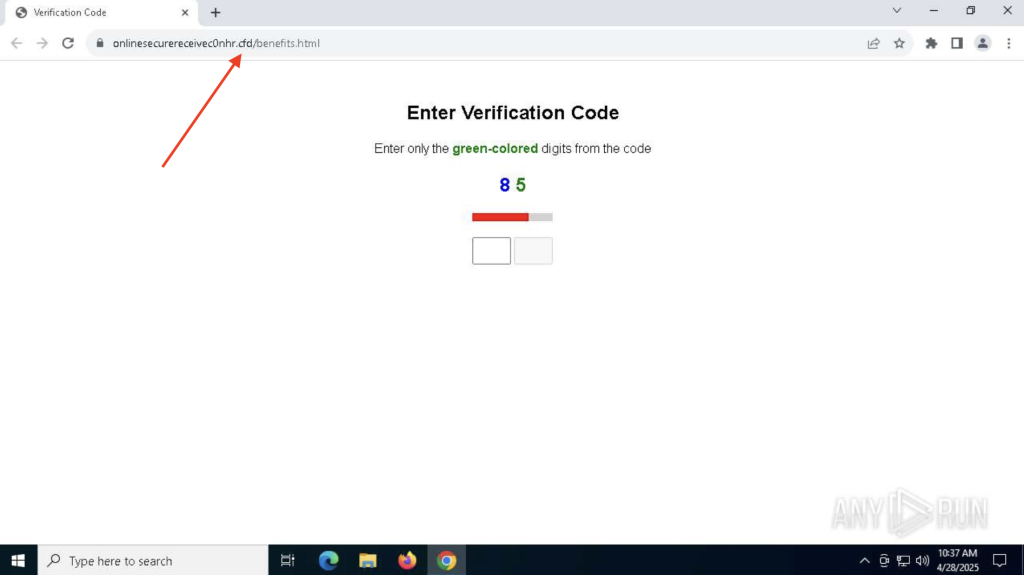
.cfd: Frequently Used in Phishing Kits
Another budget TLD, .cfd shows up often in phishing kits posing as document sharing or government portals. These sites may appear to be PDF viewers or tax forms but are designed to harvest sensitive information, usually corporate credentials or ID data.
Since the branding is generic and the sites are throwaway, attackers can spin them up in bulk.
.ru: Familiar-Looking but Malicious
Despite being a legitimate country-code domain, .ru remains a common sight in malicious campaigns. Many phishing actors use it to lend a sense of credibility, especially when targeting users in or near Russia. It’s frequently used to host fake login forms or distribute malware disguised as software downloads.
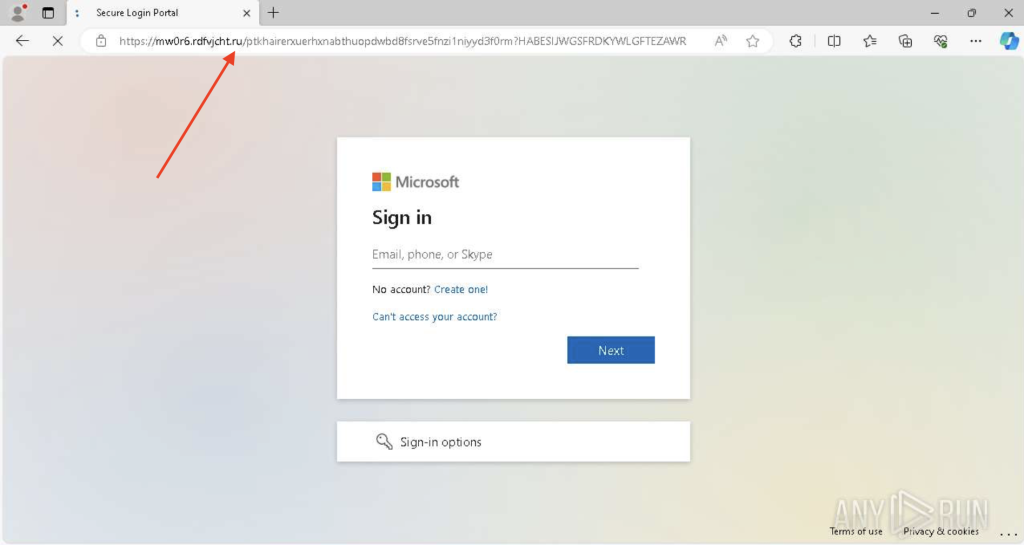
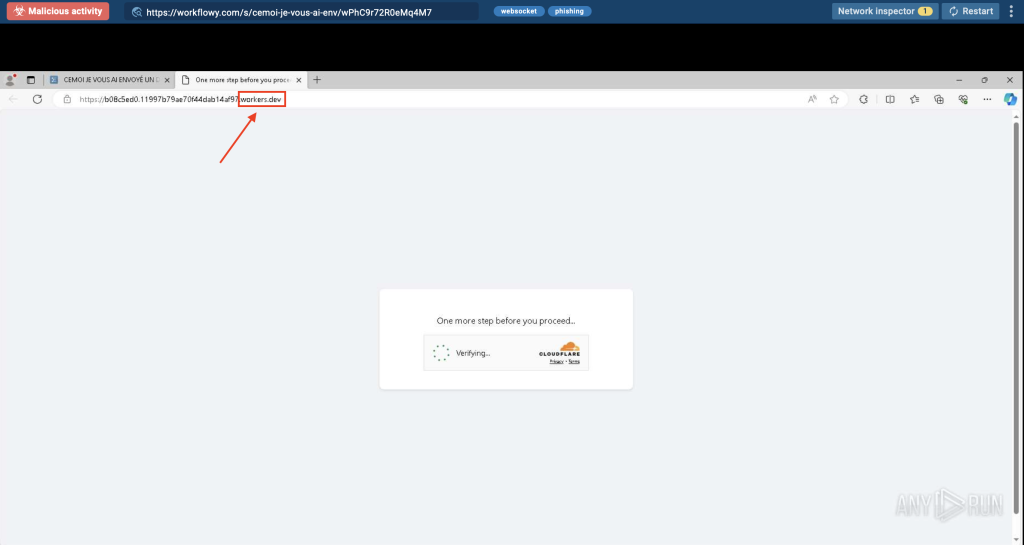
.dev: Abused via Trusted Platforms
.dev domains are often tied to Google’s hosting services, such as pages.dev and workers.dev, giving them an automatic layer of legitimacy through HTTPS and clean interfaces. Phishing pages hosted here can look polished and professional, making them harder to distinguish from real services, even for tech-savvy users. This makes .dev a powerful tool for impersonating SaaS platforms or cloud services.
The Fastest Way to Uncover Phishing Threats
Interactive sandboxes like ANY.RUN allows security teams to safely detonate suspicious URLs, monitor real-time redirections, and expose phishing behaviour as it unfolds. With verdicts in under 40 seconds, analysts can quickly understand whether a domain is benign, malicious, or part of a broader campaign.
Key benefits for SOC teams:
- Trace full redirect chains – Follow every jump, even when the initial domain appears harmless or masked behind a short link.
- Uncover phishing kits, credential stealers, and scam pages – See phishing behaviour in action, including form captures, fake login flows, and injected scripts.
- Extract IOCs and artefacts automatically – Get domain names, URLs, IPs, dropped files, and more without manual digging.
- Reduce investigation time and false positives – Use behaviour-based verdicts to make faster, more confident decisions.
- Inspect phishing pages across platforms – Identify threats targeting Windows, Android, Linux, and web environments from a single interface.
- Simulate real user behaviour – Interact with phishing pages to trigger hidden actions like redirects, pop-ups, or fake login prompts.
- Generate shareable reports instantly – Export evidence and IOC-rich reports for incident response, team handoffs, or client notifications.
