Stanley is a newly discovered malware toolkit that, as per its developer, bypasses the Chrome Web Store review process. Disguised as the Notely app, it uses clever website spoofing to steal credentials while keeping legitimate URLs in the address bar.
A new crimeware toolkit named Stanley is currently being sold on Russian-language crime forums, allowing scammers to create fake websites that look identical to the real thing. Data security and analytics specialist Varonis discovered and reported this kit, which first appeared on January 12, 2026. It is being offered by a seller using the alias Стэнли (Stanley) for prices ranging from $2,000 to $6,000.
What is most concerning for the average user is that this toolkit isn’t just a piece of software but a full-featured service. The most expensive version comes with a guarantee that the malicious app will pass the official security checks of the Chrome Web Store.
“That guarantee is what makes the usual advice insufficient. “Only install from official stores, check reviews, look for verified badges” doesn’t help when malicious extensions pass Google’s review process and sit in the Chrome Web Store alongside legitimate tools. Once published, these extensions can remain active for months before detection, quietly harvesting credentials from thousands of users,” Varonis’ report reads.
The Notely Trap
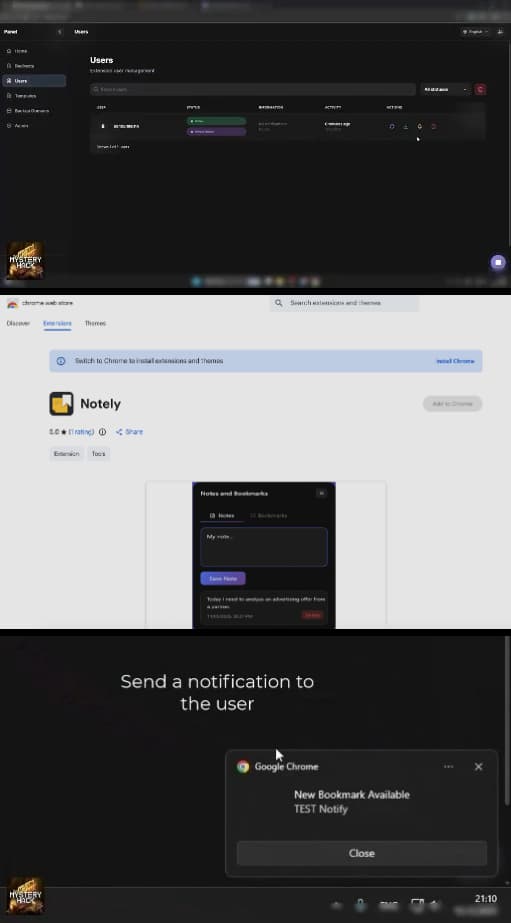
We normally trust our browser’s address bar to tell us if a site is safe. However, Varonis researchers discovered that Stanley uses a clever trick of disguising itself as a simple note-taking tool called Notely. Once a person installs it, the app can display a fake login page directly over a real website.
According to researchers, even when a user is looking at a fake page, “the browser’s URL bar continues to display the legitimate domain.” This means you could be on a scammer’s site while the address at the top still says “coinbase.com.” Further investigation revealed that the app also uses real Chrome notifications to trick people into clicking dangerous links.
Advanced Tracking
This research, which was shared with Hackread.com, shows that the toolkit is far from basic. It uses a victim’s IP address as a unique ID, allowing scammers to track users and even see their browsing history, and the app “checks in” with the hackers every 10 seconds to receive new commands.
If the hackers’ main connection is shut down, the app can automatically cycle through fallback addresses to stay online. Varonis reported this threat to Google on January 21, 2026. Although the hackers’ server was taken offline the next day, the Notely extension stayed live for longer.
Protecting Yourself
This discovery is part of a larger trend, including the DarkSpectre and CrashFix campaigns. Varonis senior security researcher and report author Daniel Kelley noted that “extensions that do something useful while hiding malicious functionality are hard to spot.”
He suggests “regularly audit your browser” and remove any tools they don’t use every day. Also, you need to be wary of any extension asking for permission to access “all websites,” as this is exactly how Stanley gains control over your accounts.
(Photo by Growtika on Unsplash)
