Fake Booking.com emails trick hotel staff into running AsyncRAT malware via fake CAPTCHA, targeting systems with remote access trojan.
A new phishing campaign is targeting hotel staff with fake Booking.com emails, tricking victims into executing malicious commands on their own systems. The scam appears well-planned, combining social engineering with the end aim to infect and compromise hotel networks with AsyncRAT.
It Starts with a Convincing Email
The attack begins with a message that appears to come from Booking.com. The email claims a guest has left behind important personal belongings and urges the hotel manager to click a button labelled “View guest information.”
The email is polite, urgent and designed to look legitimate, typical of social engineering attempts designed to trick people into clicking without thinking.
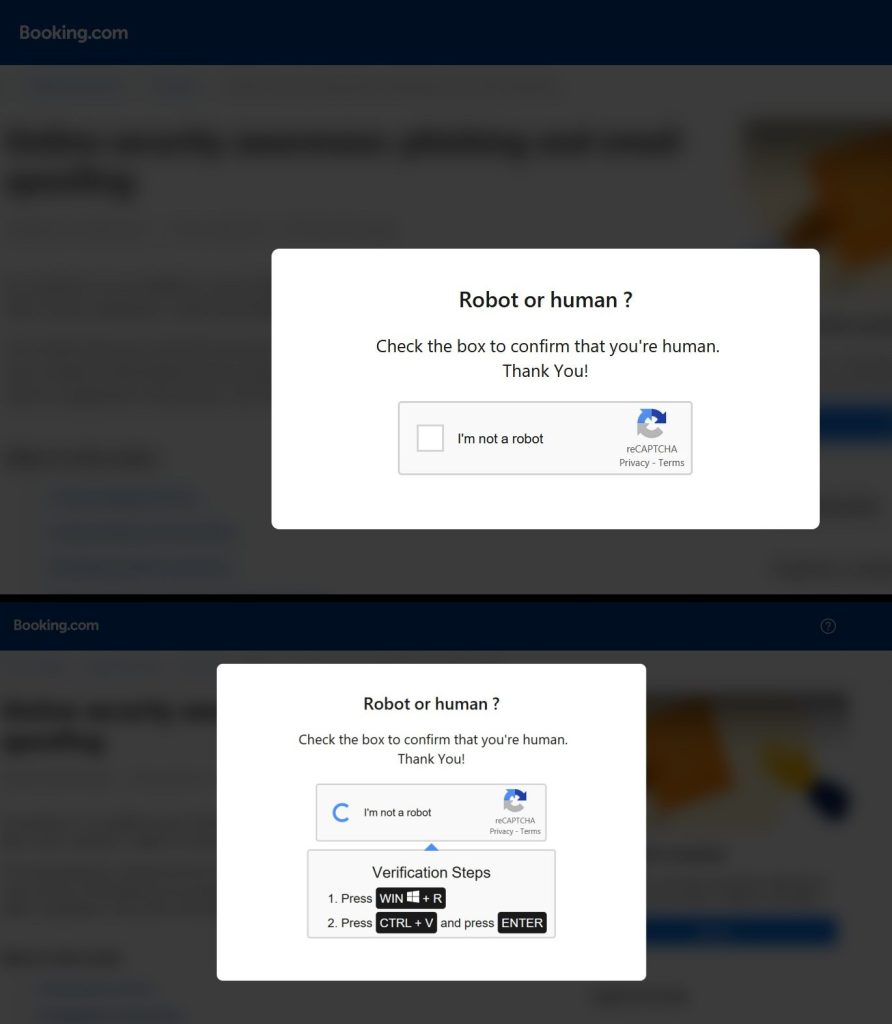
A Fake CAPTCHA Hides the Real Threat
Clicking the link takes the user to a lookalike Booking.com site hosted at: booking.partlet-id739847.com. The page initially presents a CAPTCHA asking the visitor to confirm they’re not a robot.
After checking the box, users are presented with something far more suspicious — a set of instructions that tell them to press WIN + R (to open the Windows Run dialogue), followed by CTRL + V and Enter. This trick uses the clipboard to deliver and execute a hidden command.
Behind the Scenes: AsyncRAT
Security analysis of the malware delivered in this scam shows it’s AsyncRAT, a remote access trojan. This malware has been active since the second half of 2019 and has gained popularity among cybercriminals because of its open-source and highly customizable features.
AsyncRAT is capable of:
- Keystroke logging
- Remote desktop viewing
- File access and data theft
- Installing additional payloads
- Persistent control over infected systems
AsyncRAT has been actively used in cyberattacks over the past few years. In May 2021, Microsoft observed AsyncRAT targeting aerospace and travel organizations. By November 2021, security researchers found it being delivered alongside other malware families to infect systems and steal cryptocurrencies.
In June 2023, cybersecurity firm eSentire reported a new variant called DcRAT, which was embedded in OnlyFans-related content a rebranded version of AsyncRAT. Then in January 2024, the malware was spotted targeting critical infrastructure in the United States, this time using malicious GIF and SVG files to deliver the payload.
The malware runs via MSBuild.exe, a legitimate Windows utility, helping it evade some antivirus tools. It installs itself in the %AppData% directory and communicates with a command-and-control server at 185.39.17.70 over port 8848.
Why this Phishing Scam is Tricky
Unlike basic phishing campaigns that aim to steal passwords, this one goes much further. It guides the user into executing malware manually, a clever way to bypass security restrictions and avoid triggering downloads.
If successful, attackers could gain full remote access to hotel systems, putting customer data, reservation info, and payment records at risk.
Tips for Hotels and Staff
- Never click links in unsolicited emails, even if they look official.
- Don’t run commands based on instructions from emails or websites, especially anything involving the Windows Run dialogue.
- Check the domain, real Booking.com links don’t contain extra subdomains like
partlet-id739847.
- Report suspicious messages directly to Booking.com via their official partner support channels.
This campaign is just another example of how phishing has become a threat by combining realistic branding with malware execution tactics. Hotel managers and staff should stay alert and treat any unexpected email involving guest data with caution.
