A recent security audit has uncovered critical vulnerabilities within Moodle, the widely used open-source learning management system (LMS).
These vulnerabilities allow attackers to evade core security mechanisms and potentially exploit systems via Server-Side Request Forgery (SSRF).
The flaws center around a subtle but impactful Time-of-Check to Time-of-Use (TOC-TOU) bug that affects all Moodle features that accept user-supplied URLs.
This bug puts millions of educational and organizational Moodle instances at risk, particularly those hosted on cloud platforms like AWS.
The Vulnerability: Exploiting TOC-TOU in Moodle’s Core
The vulnerabilities were discovered in Moodle version 4.4.3, the latest stable release at the time of the audit.
As per a report by QuarksLab, Researchers found that Moodle’s process for validating URLs provided by users suffers from a logical flaw. This bug allows attackers to bypass SSRF restrictions and target internal network resources.
The problem arises due to a separation between the DNS resolution (checking the hostname against a blocklist) and the actual network request.
An attacker can manipulate DNS responses between these two steps, causing Moodle to believe a URL is safe during the check, but then making the actual request point to a forbidden address, such as localhost or sensitive AWS metadata endpoints.
Example Attack Scenario
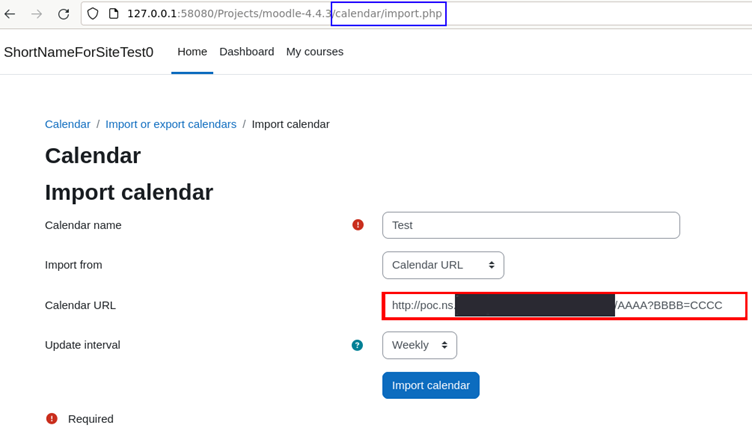
The attack chain leverages Moodle’s Calendar synchronization and File Picker features, which allow users to import external resources via URLs. Here’s how the exploit works:
- User supplies a controlled URL (e.g., http://attacker.com/resource) in the Calendar or File Picker feature.
- Moodle’s backend code first checks the hostname using DNS resolution (gethostbynamel()), ensuring it’s not blacklisted.
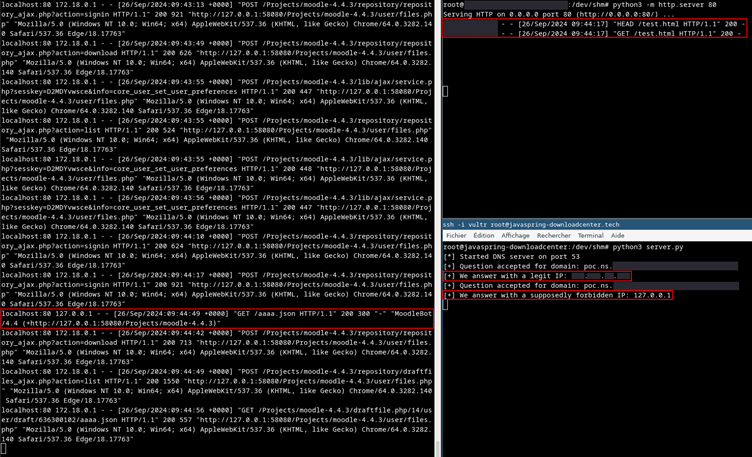
- If the check passes, Moodle proceeds to fetch the resource using curl_exec(). At this point, the attacker changes the DNS record to resolve to an internal or sensitive address, such as 127.0.0.1 or AWS’s IMDSv1 metadata endpoint.
- The system makes an internal request, bypassing all intended restrictions.
Relevant Moodle Code Excerpt
// Simplified code highlighting the TOC-TOU bug
$formdata = $form->get_data(); // User-controlled data
// ...URL validation chain...
$curl = new curl();
$response = $curl->get($user_supplied_url);In-depth check bypass:
function url_is_blocked($url) {
$host = gethostbynamel(parse_url($url)['host']);
// Check if $host is in blocklist
// Time passes...
// Later, curl_exec() is called, which re-resolves the host
}Proof of Concept: Malicious DNS Server
A Python-based DNS server can be deployed to manipulate responses based on the request order, enabling the attacker to return a benign IP during the initial check and a target IP (e.g., 127.0.0.1) during the fetch.
# PoC DNS server snippet
TOC_TOU_CHECK = 0
def resolve_domain(name):
global TOC_TOU_CHECK
TOC_TOU_CHECK += 1
if TOC_TOU_CHECK % 2 == 0:
return "127.0.0.1"
else:
return "203.0.113.1" # benign IP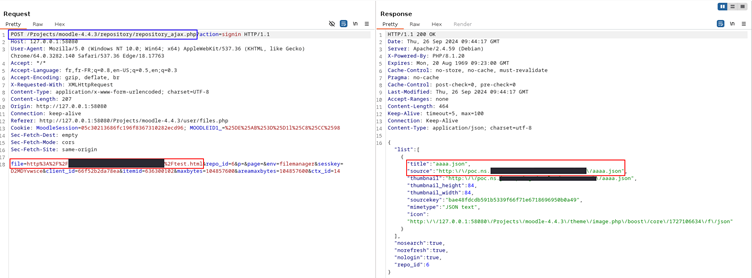
Impact and Recommendations
- Potential RCE: If Moodle is hosted on AWS and has not disabled IMDSv1, attackers could escalate SSRF to remote code execution.
- Affected Features: Calendar imports, File Picker’s URL Downloader, and any functionality accepting external URLs.
- Immediate Actions:
- Patch your Moodle instance when a fix becomes available.
- Restrict outbound network access from Moodle servers.
- Disable IMDSv1 and move to IMDSv2 on AWS-hosted Moodle instances.
Moodle’s TOC-TOU vulnerability vividly underscores the complexities and dangers of SSRF, especially in environments handling sensitive educational data.
Institutions and organizations should prioritize this and harden their deployments until official patches are released. Regular security audits and vigilant monitoring remain indispensable in today’s threat landscape.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
