ESET researchers have uncovered sophisticated attack techniques employed by a China-aligned threat actor dubbed “TheWizards,” which has been actively targeting entities across Asia and the Middle East since 2022.
The group employs a custom lateral movement tool called Spellbinder that performs adversary-in-the-middle (AitM) attacks using IPv6 SLAAC spoofing, allowing attackers to redirect legitimate software updates to malicious servers.
China-aligned APT Group’s Sophisticated Attack Infrastructure
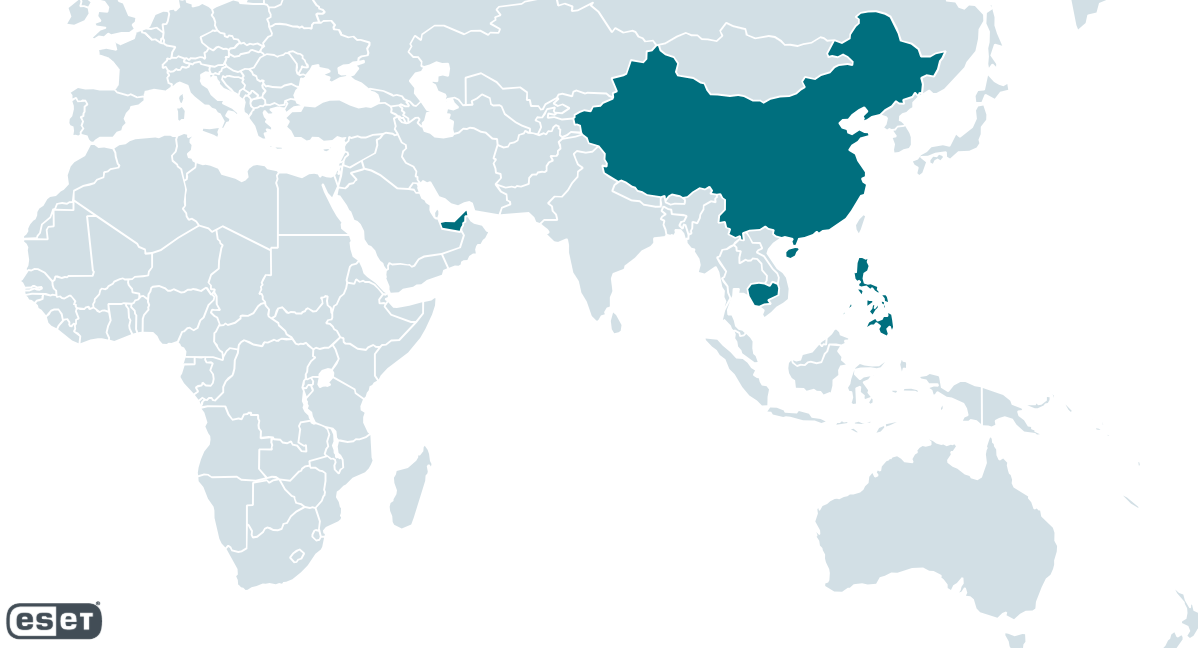
TheWizards has developed a comprehensive attack strategy focused primarily on victims in the Philippines, Cambodia, United Arab Emirates, mainland China, and Hong Kong.
According to ESET telemetry, the group targets individuals, gambling companies, and various organizations across these regions.
Their attack infrastructure involves deploying Spellbinder on compromised networks to intercept traffic and redirect update protocols from legitimate Chinese software to attacker-controlled servers.
The attackers then deliver WizardNet, their signature backdoor, which functions as a modular implant connecting to remote controllers to execute malicious .NET modules on compromised systems.
In a recent case documented by ESET, the update process of Tencent QQ software was hijacked to deliver the malware.
“Our research led us to discover a tool used by the attackers that is designed to perform adversary-in-the-middle attacks,” explained ESET researcher Facundo Muñoz.
Technical Analysis of the Spellbinder AitM Mechanism
Spellbinder employs an IPv6 SLAAC spoofing technique that exploits commonly overlooked network misconfigurations in IPv4 and IPv6 coexistence.
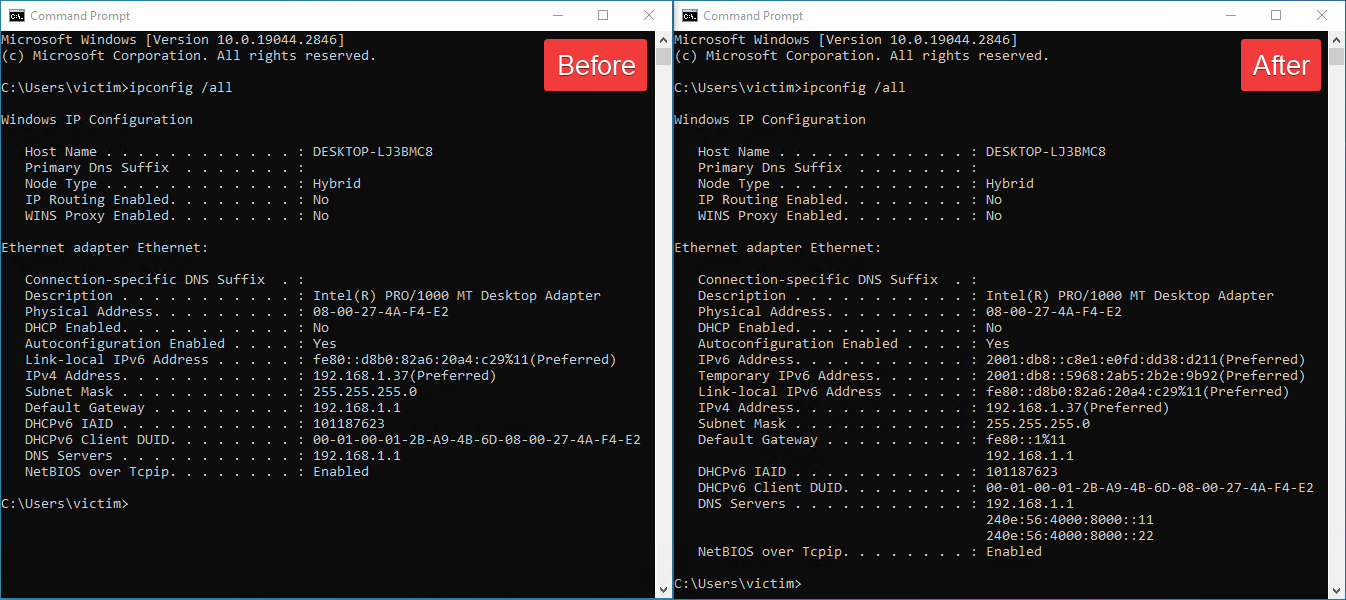
The tool sends multicast Router Advertisement packets to “all nodes” on the network, causing Windows machines with IPv6 enabled to autoconfigure using information provided in the RA message.
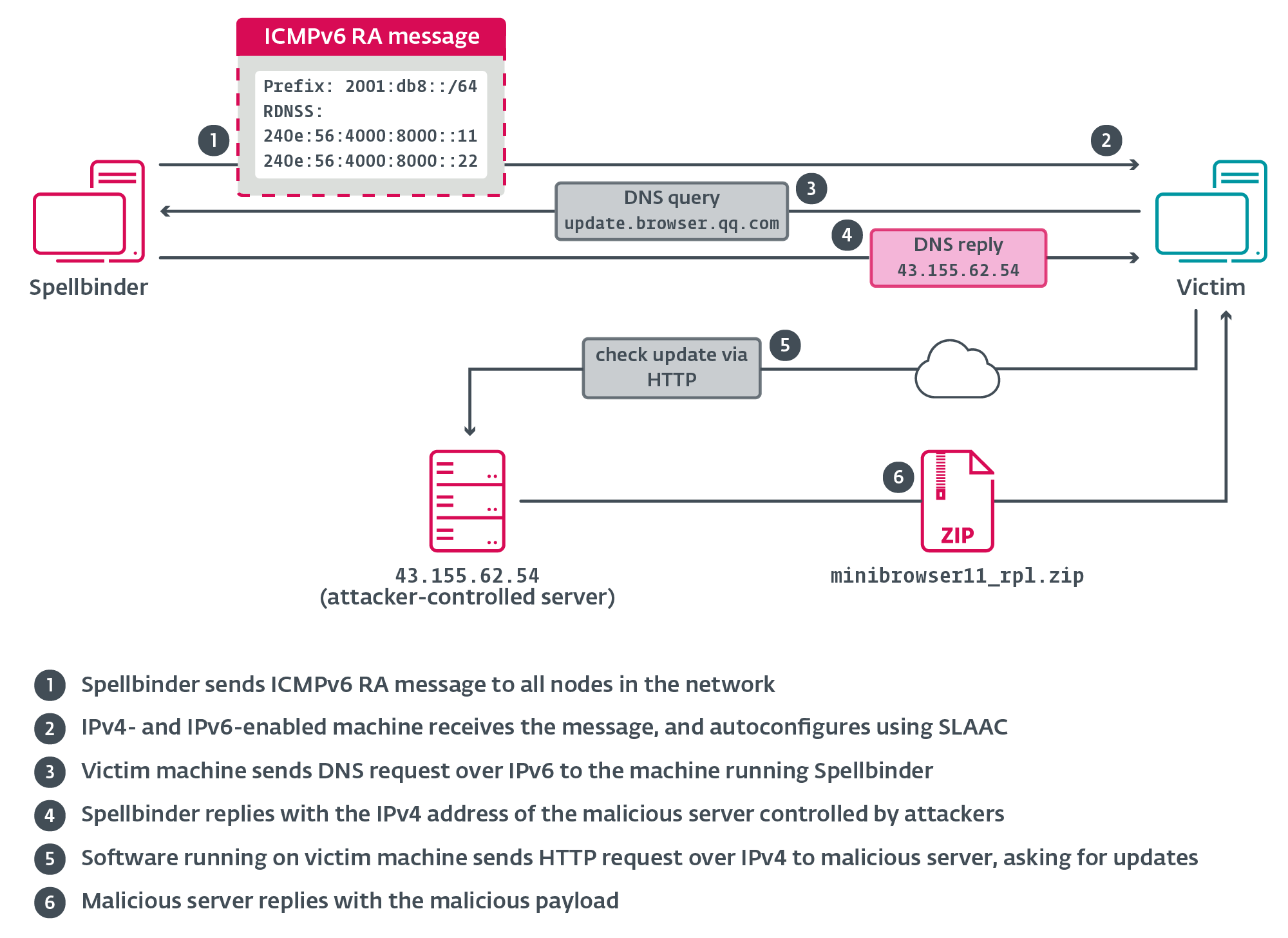
The attack vector leverages the Network Discovery Protocol in IPv6, with Spellbinder advertising itself as an IPv6-capable router. It provides specific DNS server addresses (240e:56:4000:8000::11 and 240e:56:4000:8000::22) that are part of AS4134 from China Telecom Backbone.
When DNS queries are issued for targeted domains-including popular Chinese platforms like Tencent, Baidu, and others-Spellbinder crafts and sends DNS answer messages redirecting traffic to attacker-controlled IP addresses.
This technique allows TheWizards to perform stealthy man-in-the-middle attacks without requiring ISP compromise, making it particularly effective for lateral movement within targeted organizations.
Links to Chinese Security Firm and Global Impact
ESET’s investigation revealed connections between TheWizards and Sichuan Dianke Network Security Technology (also known as UPSEC), a Chinese cybersecurity company.
While TheWizards primarily uses the WizardNet backdoor for Windows systems, their hijacking server is also configured to deliver a backdoor called DarkNights to Android devices.
According to NCSC UK, UPSEC is linked to malware targeting Tibetan and Uyghur communities. Intelligence Online identified UPSEC as the supplier of the DarkNights backdoor (also known as DarkNimbus), which shares infrastructure with TheWizards’ operations.
The sophisticated nature of TheWizards’ tools and tactics represents a significant threat to organizations worldwide.
Their ability to hijack legitimate software update mechanisms from popular Chinese applications demonstrates an advanced persistent threat capability that can bypass conventional security measures.
The group’s continued evolution of tools like Spellbinder since its initial discovery in 2022 indicates ongoing development and operational activity that security teams should monitor closely.
Indicators of Compromise (IoCs):
Files
| SHA-1 | Filename | ESET detection name | Description |
| 9784A1483B4586EB12D86E549D39CA4BB63871B8 | minibrowser_shell.dll | Win32/Agent.AGNF | Downloader component. |
| 4DB38A097AE4D5E70B2F51A8EE13B0C1EE01A2A1 | Client.exe | MSIL/Agent.DMS | WizardNet backdoor. |
| 76953E949AC54BE8FF3A68794EF1419E9EF9AFCB | ipv6.exe | Win64/Agent.CAZ | Spellbinder tool (2022). |
| DA867188937698C7769861C72F5490CB9C3D4F63 | N/A | Win64/Agent.CAZ | Spellbinder tool (2023), loaded in memory. |
| 0CBA19B19DF9E2C5EBE55D9DE377D26A1A51B70A | wsc.dll | Win64/Agent.EUO | Loads shellcode from log.dat. |
| 1A8147050AF6F05DEA5FBCA1AE1FF2FFD2B68F9C | log.dat | Win32/Rozena.BXT | Shellcode that loads Spellbinder. |
| 2D376ADF44DBD9CF5DB08884E76192D0BC9984C4 | plugin-audiofirstpiece.ml | Android/Spy.Agent.EFF | ZIP archive containing DarkNights for Android. |
| 5B70A853D8E989AD102D639FBF7636B697313ABC | classes.dex | Android/Spy.Agent.EFF | DarkNights for Android. |
Network
| IP | Domain | Provider | First seen | Details |
| 43.155.116[.]7 | hao[.]com | ACEVILLEPTELTD-SG | 2022‑11‑06 | Server issuing malicious updates to legitimate applications in 2022. Used by Spellbinder. |
| 43.155.62[.]54 | vv.ssl-dns[.]com | ACEVILLEPTELTD-SG | 2022‑11‑29 | Server issuing malicious updates to legitimate applications in 2023 and 2024. Used by Spellbinder. |
| 43.135.35[.]84 | mkdmcdn[.]com | ACE-SG | 2023‑11‑15 | WizardNet C&C server. |
| 103.243.181[.]120 | assetsqq[.]com | HK Kwaifong Group Limited | 2021‑07‑15 | DarkNights C&C server. |
| 111.13.100[.]92 | N/A | CHINAMOBILE-CN | 2021‑07‑15 | DarkNights C&C server. |
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
