A new leak site has gone live, operated by the notorious group calling itself “Scattered Lapsus$ Hunters,” (a coalition that combines the tactics and branding of Scattered Spider, Lapsu$, and ShinyHunters) and it carries a bold claim that Salesforce, one of the largest SaaS and CRM providers in the world, has been breached and close to one billion records (989 million records) are up for sale.
The group says the attack took place in mid-2024 and that the stolen data amounts to multiple terabytes. In messages posted to their site, they allege the data includes highly sensitive personal information such as Social Security numbers, driver’s licenses, and dates of birth. They are now demanding that Salesforce negotiate before an October 10, 2025, deadline, warning that failure to do so will result in the release of the full cache.
Additionally, the hackers are also inviting law firms to cooperate with them, even naming Berger Montague as a partner they would share evidence with. The hackers are presenting this less like a threat and more like an offer. They also claim they will provide detailed documentation to courts and regulators in the United States and Europe, alleging Salesforce acted with “criminal negligence” by failing to block repeated intrusions.
The list of companies named as victims on the leak site is massive. The group has listed 39 organizations whose data they say was taken from Salesforce-hosted systems. The list includes:

- KFC – 1.3GB
- ASICS – 9GB
- UPS – 91.34GB
- IKEA – 13GB
- GAP, INC. – 1GB
- Petco – 9.9GB
- Cisco – 5.6GB
- McDonald’s – 28GB
- Cartier – 1.4GB
- Adidas – 37GB
- Fujifilm – 155MB
- Instacart – 32GB
- Marriott – 7GB
- Walgreens – 11GB
- Pandoranet – 8.3GB
- Chanel – 2GB
- CarMax – 1.7GB
- Disney/Hulu – 36GB
- TransUnion – 22GB
- Aeroméxico – 172.95GB
- Toyota Motor Corporations – 64GB
- Stellantis – 59GB
- Republic Services – 42GB
- TripleA (aaacom) – 23GB
- Saks Fifth – 1.1GB
- Albertsons (Jewel Osco, etc) – 2GB
- Engie Resources (Plymouth) – 3GB
- 1-800Accountant – 18GB
- HMH (hmhcocom) – 88GB
- Instructurecom – Canvas – 35GB
- Google Adsense – 19GB
- HBO Max – 3.2GB
- FedEx – 1.1TB
- Qantas Airways – 153GB
- Vietnam Airlines – 63.62GB
- Air France & KLM – 51GB
- Home Depot – 19.43GB
- Kering (Gucci, Balenciaga, Brioni, AlexMcQ) – 10GB
Hackers Accuse Salesforce of Failure
The hackers accuse Salesforce of failing to enforce multi-factor authentication and say they successfully targeted more than 100 additional unnamed instances through OAuth application weaknesses. They also point to earlier warnings, claiming they emailed Salesforce in July 2025 from an address linked to the operation and received no meaningful response.
The hackers present their message as part ransom demand, part technical briefing. They point out that their attacks ran for a year, left clear traces, and argue Salesforce had enough time to spot and stop them
They also cite GDPR, CCPA, and HIPAA obligations, arguing that data protection duties were ignored. To back this up, they promise to release forensic-style documents with attack fingerprints, affected populations broken down by country, and details about the kinds of information exposed.
The attackers provide a tuta.io based contact address and require any communication to include a strict verification format in the subject line. They say verified representatives will then be forwarded to a live channel where negotiations can take place.
Salesforce Apparently Knows
The hackers have also circulated a screenshot on their Telegram channel that appears to show a Salesforce security advisory acknowledging ongoing extortion attempts. In the message, Salesforce refers to social engineering threats, states that there is no evidence its platform was compromised, and reassures customers that its teams are monitoring the situation.
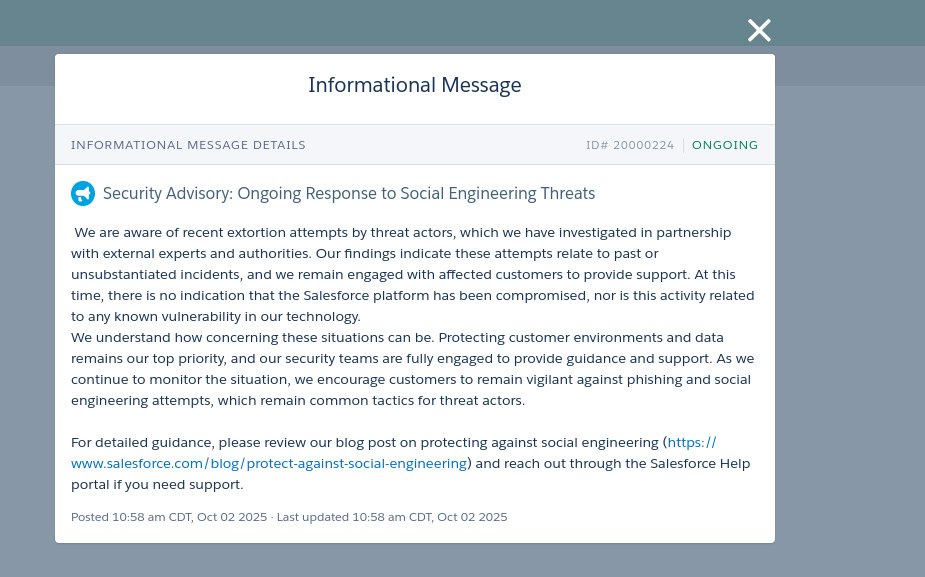
Since the image cannot be independently verified, it is unclear whether this advisory is authentic or fabricated as part of the attackers’ campaign. Nevertheless, the group’s site maintains the deadline of October 10, 2025, with the status listed as “Active.” And, with the site live, the group now has a public tool to increase pressure on the company as the deadline approaches.
