ClayRat, a new Android spyware, has drastically improved its abilities, making it a far greater threat than anticipated. Mobile security firm Zimperium has released an important update on this spyware, revealing that this new version is not only harder to spot but has been upgraded to perform a full device takeover.
Initial Discovery and New Features
As previously covered by Hackread.com, Zimperium’s zLabs discovered ClayRat in October 2025 as a fast-spreading Android spyware mainly targeting users in Russia. It disguised itself as popular apps like WhatsApp, Google Photos, TikTok, and YouTube. Even then, it could steal private data, including call logs, SMS messages, and even capture victim photos with the phone’s camera.
This new version still mimics apps and local services, such as Russian taxi and parking applications. However, the added features make it “a more dangerous spyware compared to its previous version,” noted zLabs researchers Vishnu Pratapagiri and Fernando Ortega in their latest blog post shared exclusively with Hackread.com.
Reportedly, the updated ClayRat abuses a powerful Android feature called Accessibility Services. It first asks the user to grant it Default SMS privileges, then guides them to turn on the Accessibility Service.
This new capability means the spyware can take over your phone as it can record your lock screen details, capturing your PINs, passwords, or even patterns, to unlock your device automatically. It can record your entire screen activity, letting attackers see exactly what you’re looking at and typing.
To secure its hold, the malware can block you out by putting fake screens, like a phoney “System Update” notice, on top of your display; it then uses automated screen taps to disable Google Play Protect, preventing you from uninstalling the malicious app or shutting down the phone. Finally, it can create fake custom messages that pop up like real alerts, intercepting any personal information, e.g. password, that you type in reply.
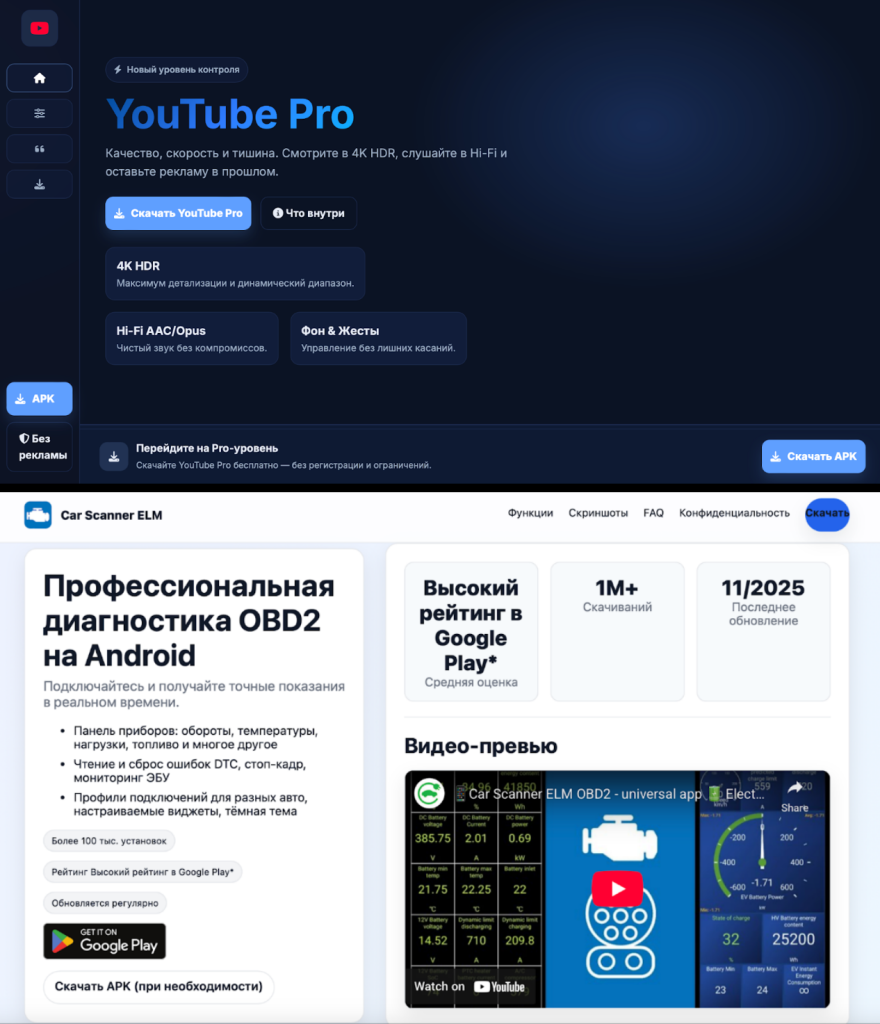
Why Businesses Should Worry
ClayRat poses a serious risk to companies because employees often use their own mobile phones for work. If a work device is compromised, attackers can easily access company emails, messaging apps, and other business data.
The spyware is still spreading aggressively; researchers observed it operating over 25 fraudulent phishing domains that mimic various apps, including utility tools like the Car Scanner ELM. It also uses the widely trusted cloud service Dropbox to distribute its malicious files. Zimperium has already found over 700 unique versions of the software, showing how quickly this operation is expanding.
As we know it, protecting a device from a threat that can seize complete control requires very strong security. The simplest and most effective way to stay protected is to only install apps from the official Google Play Store and carefully check the permissions, especially the Accessibility Service, before granting them.
