A new report from security firm Infoblox reveals that at least 18 American universities have been hit by a prolonged, coordinated phishing attack over a period of many months.
According to Infoblox’s blog post, shared with Hackread.com, this campaign ran from April to November 2025 and aimed to steal student and staff account details, even when Multi-Factor Authentication (MFA) was turned on.
The Attack Strategy: Bypassing Security
For your information, MFA is an extra safety step that involves entering a code from your phone or approving a notification after you enter your password. This attack bypassed MFA by using a dangerous, open-source phishing kit called Evilginx.
Evilginx acts like a digital middleman, using an Adversary-in-the-Middle (AiTM) approach. When a student clicked on one of the phishing links sent in a personalised email, Evilginx quietly stepped between the victim and the university’s actual login page. It mimicked the real login process, stealing both the username/password and the session cookie that grants access after MFA is completed.
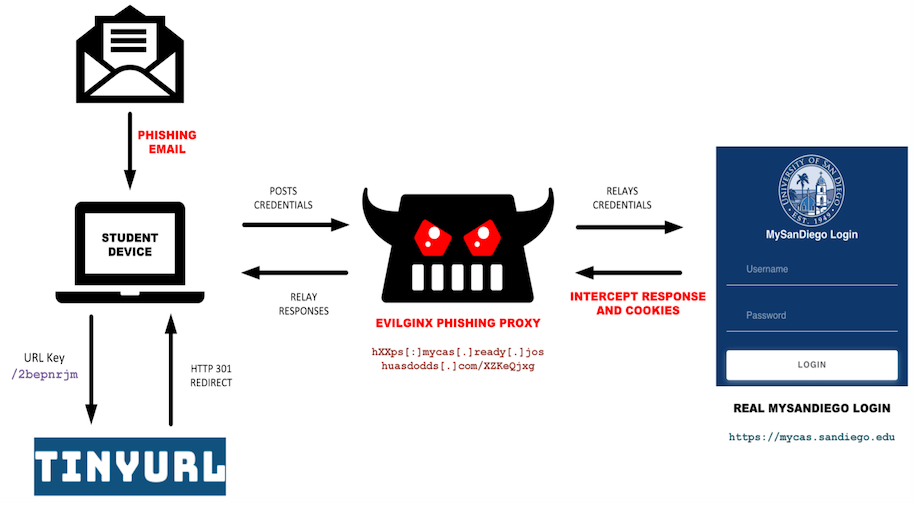
Stealing this cookie allows the attacker to take over the account completely. Researchers noted that the links used in the emails were short, temporary TinyURLs that looked like they came from the school’s single sign-on (SSO) portal.
Tracing the Digital Trail
Infoblox’s report also revealed that the campaign operators took steps to hide their tracks, such as changing the attack links often and using services like Cloudflare to mask where their servers were located. However, an initial tip from a security professional at one of the targeted institutions helped Infoblox begin an investigation.
Further probing involved analysing DNS patterns, which refer to the digital record of how domains are requested and resolved. Eventually, Infoblox’s Threat Intel team was able to connect the dots. They tracked nearly 70 different domains used in the plot over the months. The first recorded attack was on April 12, 2025, against the University of San Diego.
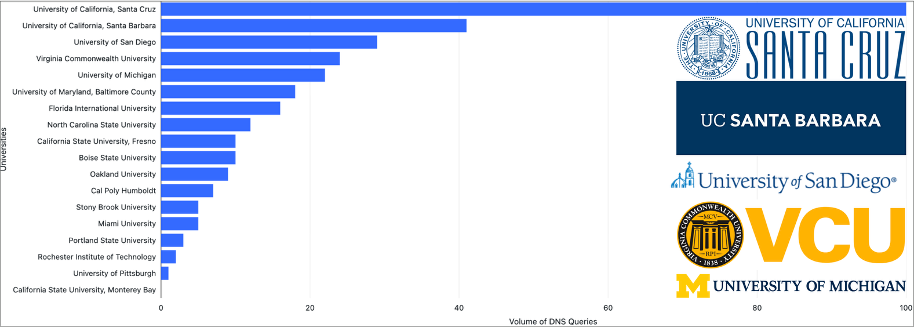
The top five targeted schools, based on attack volume, were the University of California, Santa Cruz, the University of California, Santa Barbara, the University of San Diego, Virginia Commonwealth University, and the University of Michigan.
Renée Burton, Vice President of Infoblox Threat Intel, stressed the serious harm these attacks cause, noting that universities remain a popular target. She shared a particularly concerning example, stating, “Universities remain a common target for malicious actors, who show little concern for the damage they cause or the value of the systems they lock down,” and detailed a case where an attack on the University of Washington “ultimately destroyed part of the museum’s digital catalogue of plant and animal specimens an invaluable record.”
These successful attacks show how quickly cybercriminals are using tools like Evilginx to bypass MFA, making strong security awareness and prompt reporting by campus staff and students more critical than ever to protect their data.
