Security researchers have uncovered a sophisticated Spanish-language phishing kit targeting Microsoft Outlook users, revealing what appears to be a coordinated credential-theft operation with potential AI-assisted code development.
The toolkit, tracked under the operational codename “Mycelial Mage,” demonstrates evolving anti-analysis capabilities and a deliberate shift toward ephemeral exfiltration channels using Telegram and Discord.
The investigation, which began in August 2025, traces the operation’s origins back to at least March 2025.
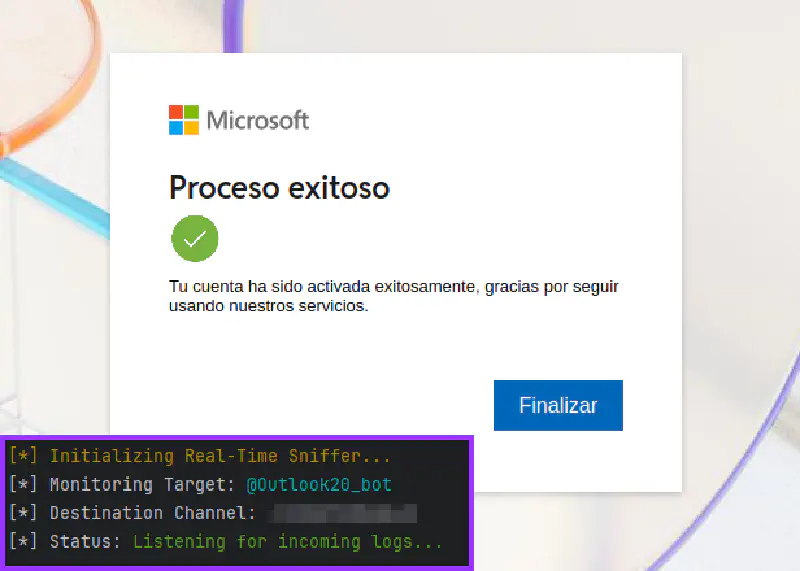
However, the true scope of the campaign may extend further. Researchers identified the kit through a distinctive signature embedded in the malicious code four mushroom emojis inserted within a stylized string referencing Outlook (0UTL) a deliberate marker that proved invaluable for tracking multiple deployments across the internet.
The Mycelial Mage kit exhibits clear evidence of iterative development, with researchers documenting at least three distinct evolutionary phases.
The earliest variants employed a modular architecture, separating configuration data from execution logic. Later iterations introduced aggressive anti-analysis measures designed to frustrate both static and dynamic inspection.
These defensive techniques include dynamic debugger traps triggered when developer tools are opened, console method hijacking to suppress runtime visibility, and self-referential regex patterns engineered to cause catastrophic backtracking during source analysis.
The most recent variants detected in the wild show hallmarks of AI-assisted development, particularly in newly observed Discord-based exfiltration modules.
Code samples demonstrate consistent indentation, clearly named functions, and explanatory comments in Spanish characteristics distinctly different from the obfuscated early variants.
This shift suggests either operator sophistication or access to generative AI tools for code development and obfuscation.
Credential Capture and Exfiltration
The operational workflow remains consistent across all observed variants. Upon execution, the kit performs reconnaissance using legitimate IP geolocation services (api.ipify.org and ipapi.co) to resolve victim location data.
Stolen credentials including email addresses and passwords are enriched with IP address and geolocation information before exfiltration.
Data theft follows a standardized format, consistently marked with the operator’s fungal emoji signature: 0UTL CORREO: [victim_email] PASSWR: [victim_password] IP: [IP_Address] [City, Country].
Perhaps most notably, researchers observed a strategic migration from Telegram-based exfiltration to Discord webhooks in recent campaigns. This shift reflects a sophisticated understanding of defensive capabilities.
Telegram bot tokens, while easier to deploy, create potential forensic windows defenders who obtain valid credentials can query API metadata or intercept message logs.
For Microsoft Outlook users, particularly those in Spanish-speaking regions, heightened awareness of unsolicited authentication requests and email verification prompts remains critical for defense.
Infrastructure as a Service Model
Hosting patterns suggests this operation functions as a distributed phishing-as-a-service ecosystem rather than a singular campaign.
Deployment infrastructure remains compartmentalized across multiple autonomous systems and IP ranges, indicating intentional separation for resilience.
However, selective convergence at the exfiltration layer where Telegram tokens and Discord webhooks bridge isolated infrastructure clusters points to backend reuse and operational efficiency.
The discovery underscores a broader trend in credential-theft operations: increasing sophistication in both development practices and operational tradecraft.
Discord webhooks, by contrast, function as write-only sinks. Once exfiltrated data is delivered, the historical record becomes inaccessible to anyone holding only the webhook URL, creating an inherently opaque exfiltration channel.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
