Security researchers from the Whitehat School recently completed an intensive bug-hunting project focused on identifying privilege escalation (LPE) flaws in Windows systems.
The findings reveal critical vulnerabilities in two major attack surfaces: kernel drivers and named pipes areas that cybersecurity teams should prioritize immediately.
The Kernel Driver Challenge
Kernel drivers represent a significant security risk because they operate at the system’s core, processing requests from user applications.
The research shows that many drivers lack proper validation when receiving commands from users.
When a driver accepts user input without checking its legitimacy, attackers can exploit this trust gap to read and write arbitrary data in protected kernel memory.

The team demonstrated a practical methodology: first identifying vulnerable drivers on a system, then analyzing their code to find unsafe memory operations like “memmove” functions that blindly copy data.

By crafting malicious commands, researchers achieved arbitrary read and write capabilities, ultimately escalating their privileges to system administrator level.
Named pipes are communication channels that allow user applications to interact with system services running with elevated privileges.
The Hackyboiz research revealed that many system services configure these pipes with overly permissive access controls, allowing any user to connect and send requests.
What’s particularly concerning is that developers sometimes implement command handlers without sufficient validation, trusting that only authorized parties would connect.
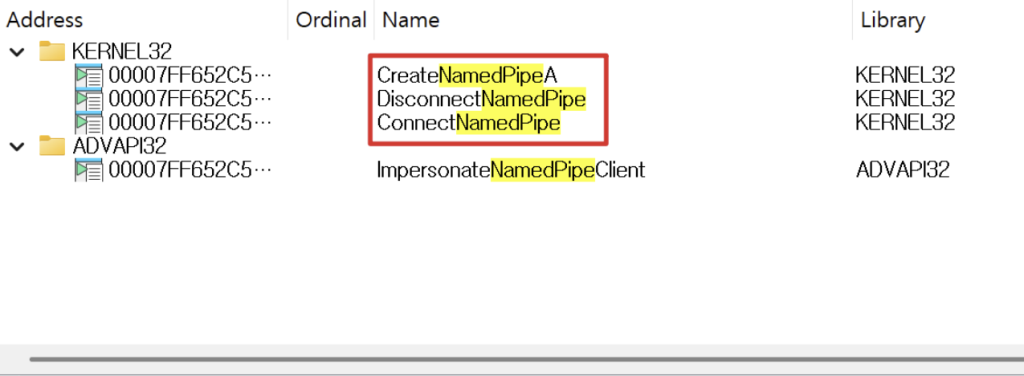
The team identified a real-world vulnerable antivirus service with a named pipe accessible to all users.
By sending specially crafted requests, they manipulated the SYSTEM service into modifying critical Windows registry settings, ultimately executing arbitrary code with administrator privileges.
Both vulnerabilities share a common root cause: insufficient trust boundary validation. Kernel drivers and system services assume user input is safe without proper checks.
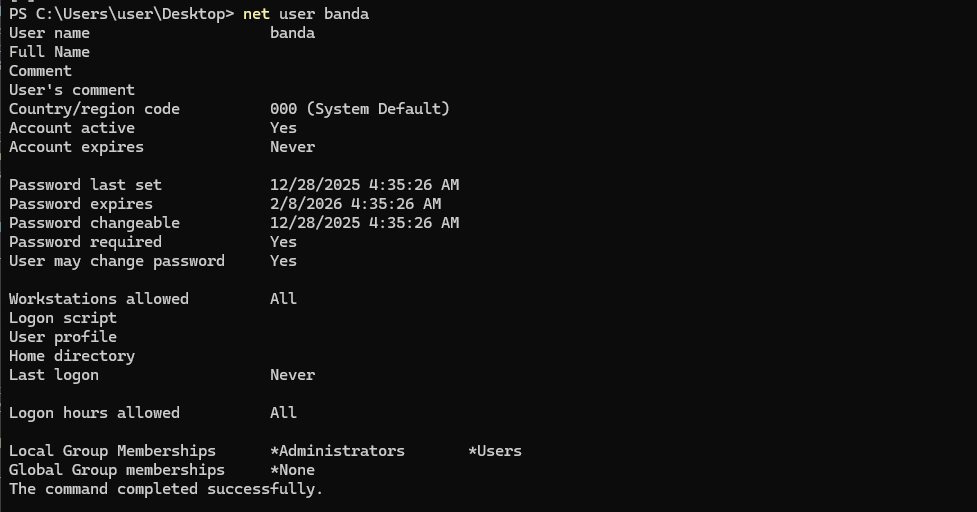
This gap creates a direct path from user mode to system privileges.
The research methodology outlined provides a systematic approach for security teams: enumerate exposed interfaces, verify accessibility permissions, analyze code for unsafe patterns, and test with dynamic monitoring tools like WinDBG and Process Monitor.
Organizations should conduct urgent audits of third-party drivers and system services, particularly those from antivirus vendors, security tools, and system utilities.
The findings underscore why Windows remains a prime target for local privilege escalation attacks and why defense-in-depth strategies remain essential.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
