The hacking group ShinyHunters has claimed responsibility for breaching Resecurity, a US-based cybersecurity company headquartered in Los Angeles. In a public Telegram post shared earlier today, the group announced it had gained full access to internal systems and released a set of screenshots to support its claim.
The images depict several internal Resecurity dashboards, user management panels, token databases, and employee communication channels. The interfaces shown include sensitive user data, API keys, access tokens, and internal Mattermost chat conversations.
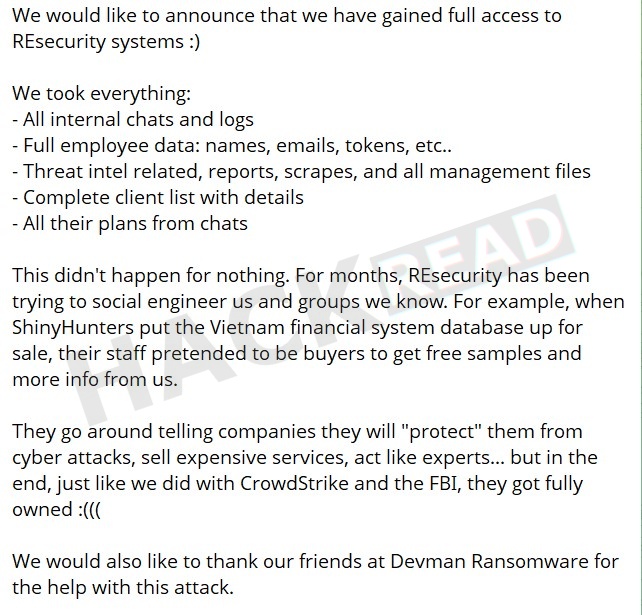
In their post, ShinyHunters claimed they exfiltrated:
- Full internal chats and logs
- Internal plans discussed in chat logs
- A complete client list with related details
- Threat intelligence data, reports, and management documents
- Employee information, including names, email addresses, and authentication tokens.
Screenshots Analysed
The screenshots analysed by Hackread.com show user accounts linked to corporate domains, user tokens under Firebase Cloud Messaging (FCM), and internal chat conversations referring to reports on scam numbers and moderation actions.
One image shows admin and user panels with real-time access tokens and email accounts, while another displays a list of employee profiles with active statuses and API credentials exposed. Hackread.com also cross-checked the names visible in the screenshots on LinkedIn, and they appear to be linked to Resecurity.
In a message accompanying the images, ShinyHunters accused Resecurity of attempting to infiltrate or deceive threat actor groups by posing as buyers on dark web markets. They referenced a previous incident involving a database related to Vietnam’s financial systems, stating that Resecurity staff sought free samples while claiming to be potential clients. ShinyHunters framed the alleged breach as retaliation for these tactics.
They also mentioned collaboration with the Devman ransomware group in executing the attack. The post references prior claims involving other high-profile breaches, such as CrowdStrike, framing this incident as part of a continued effort targeting firms they label as hypocritical or deceptive.
Unconfirmed For Now
As of now, Resecurity has not issued any public response or confirmation regarding the breach. The authenticity and scope of the compromise remain unverified by third-party sources. If confirmed, the incident would mark Resecurity as the first major target publicly claimed by ShinyHunters in 2026.
Resecurity has previously worked with both government and private sector entities in cybercrime investigation, threat attribution, and digital forensics. This said breach could have implications for partners, clients, and broader trust in their services, particularly if sensitive intelligence or client data was exposed.
More information is expected as the situation develops.
