Scammers are using official Microsoft Teams notifications to send fake billing notices. Check Point Research reveals how this phone-based scam works and which industries are most at risk.
Cybersecurity experts at Check Point Research have spotted a new phishing campaign where scammers are using a clever method to sneak into office accounts. The most concerning finding is that, according to the report from Check Point Harmony Email Security, more than 12,866 phishing emails have been sent out already, reaching around 6,135 users.
How the Scam Works
What makes this particular campaign different is that instead of sending a suspicious link, attackers are using the trust we have in everyday office tools. Microsoft Teams, as we know it, allows you to invite guests to a group. Scammers are taking advantage of exactly this by creating a new team with a name that looks like an urgent bill, such as a Subscription Auto-Pay Notice.
When the scammer invites you as a guest, Microsoft sends you a real email notification from an official address. This makes it very hard for security filters to catch the scam. Inside the email, the team name itself acts as the trap. It claims you owe money, like in one case, an amount of $629.98 USD.
According to Check Point’s blog post, attackers use special characters and symbols, like using a zero instead of the letter O, to help the message bypass security while remaining readable to you.
One sample observed by the team was titled: “Subscription Auto-Pay Notice (Ivoice ID: 2025_614632PPOT_SAG Amount 629. 98 USD). If you did not authorise or complete this m0nthly Payment, plese c0ntact our support team urgently”.
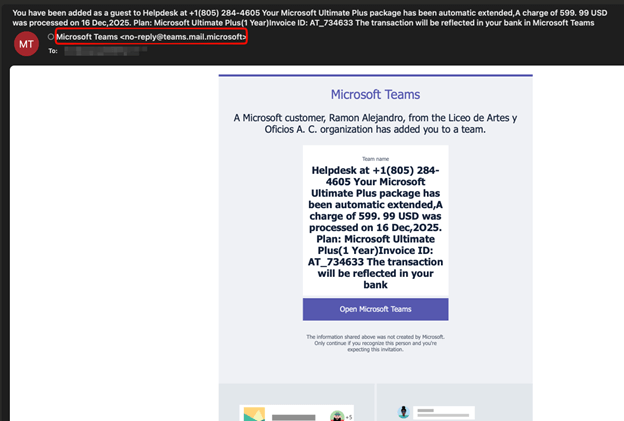
A Push for Phone Scams
The most interesting part is that the attackers aren’t asking you to click a button or a link; they want you to call a fake support phone number included in that team name. The goal is to get you on the phone to resolve a pretend billing issue and trick you into giving up your bank details or passwords. It is worth noting that this campaign is incredibly active, sending out about 990 messages every single day. While many industries have been hit, the sectors seeing the most trouble include:
- Education: 14.9%
- Technology and SaaS: 18.6%
- Manufacturing, Engineering, and Construction: 27.4%
Global Reach
The campaign has mainly targeted people in the United States, which accounts for 67.9% of the activity, followed by Europe (15.8%) and Asia (6.4%). Within Latin America, researchers noted that Brazil and Mexico saw the most activity.
The main takeaway from this research is that attackers are finding ways to use popular applications and trusted invitation workflows to hide in plain sight. People should be very careful of any unexpected invitations, especially those that use urgent language or include phone numbers.
