Author: Cybernoz
Effective Vulnerability Management offers a view of a key part of cybersecurity, showing how practices, tools, and processes can help…
The threat actors known as Golden Chickens have been attributed to two new malware families dubbed TerraStealerV2 and TerraLogger, suggesting…
A new critical security vulnerability in Apache Parquet Java has been disclosed that could allow attackers to execute arbitrary code…
In an era where cybercrime is rapidly evolving, security professionals and hackers alike have found new, innovative ways to conceal…
CISOs know cyber risk is business risk. Boards don’t always see it that way. For years, CISOs have struggled to…
National Cyber Security Centre (NCSC) has issued technical guidance following a series of cyber attacks targeting UK retailers. These incidents…
In this Help Net Security interview, Stuart Clarke, CEO at Blackdot Solutions, discusses the strategic use of open-source intelligence (OSINT)…
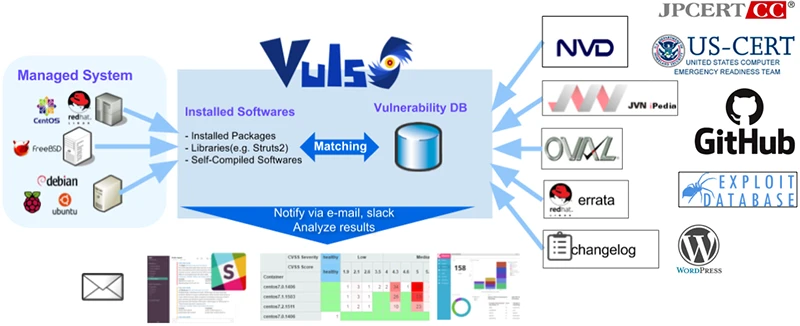
Vuls is an open-source tool that helps users find and manage security vulnerabilities. It was created to solve the daily…
90% of IT and security leaders said their organization experienced a cyberattack within the last year, according to a report…
04 May Global Ransomware Damage Costs Predicted To Exceed $275 Billion By 2031 Posted at 22:09h in Blogs, Videos by…
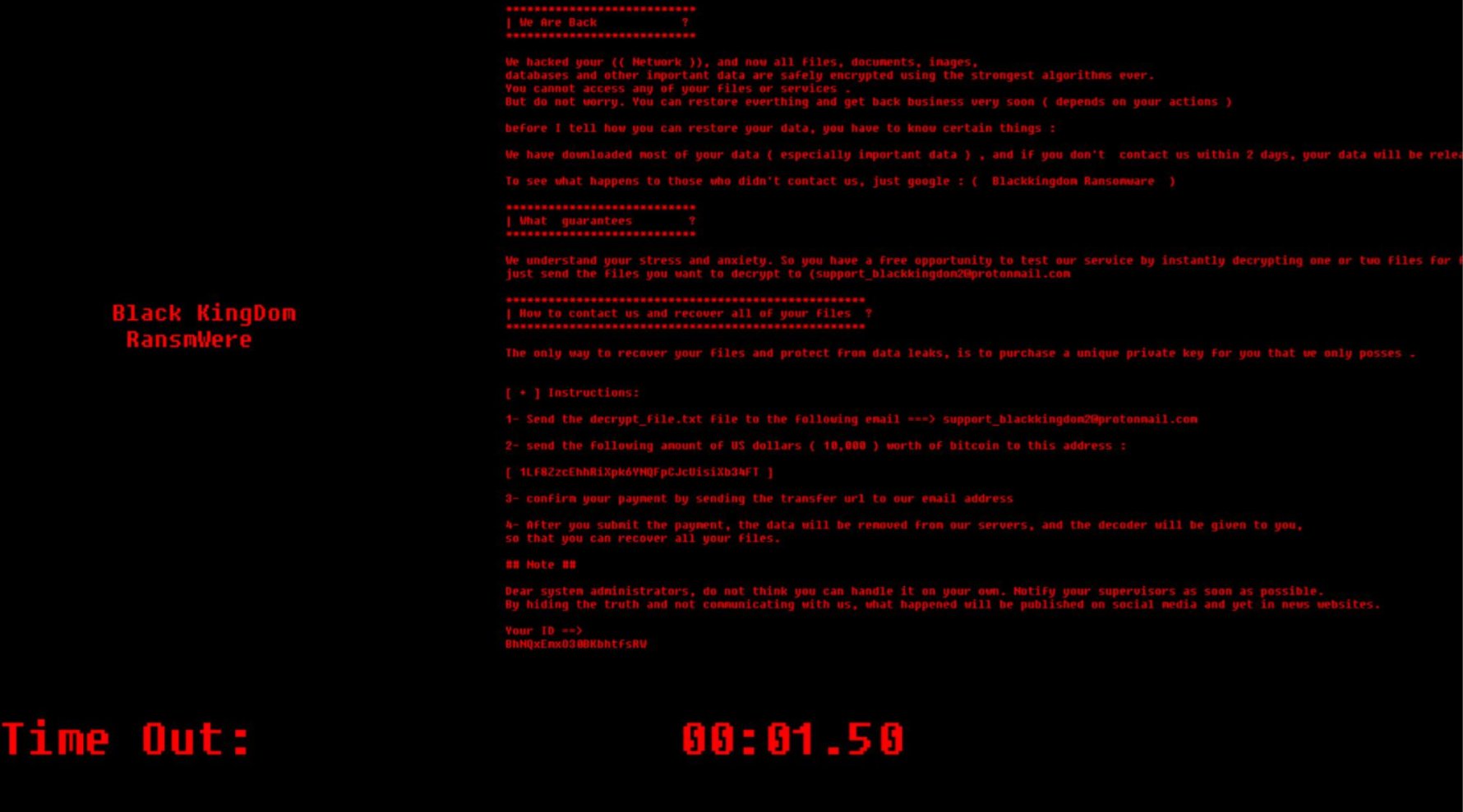
US authorities have indicted Black Kingdom ransomware admin Pierluigi Paganini May 05, 2025 A 36-year-old Yemeni man behind Black Kingdom…
Apple is partnering with Amazon-backed startup Anthropic on a new “vibe-coding” software platform that will use artificial intelligence to write,…