Author: Cybernoz
Cybercriminals have begun openly marketing a powerful new variant of the HiddenMiner malware on underground dark web forums, raising alarms…
Chinese products have become a staple in markets around the world. From household items like pens to complex machinery such…
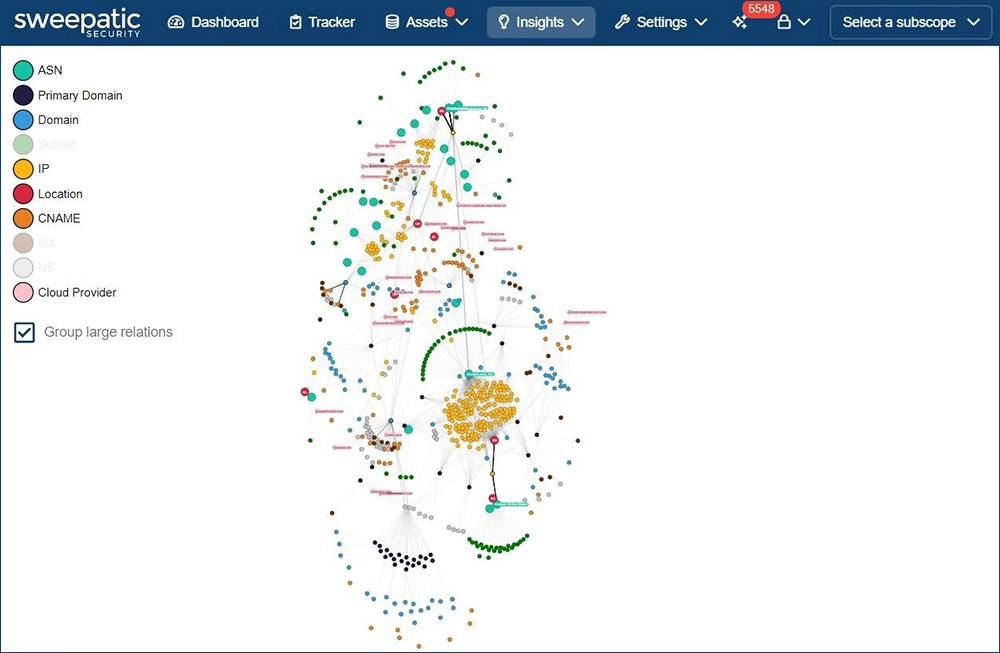
In a world where organizations’ digital footprint is constantly changing and attackers regularly capitalize on security failings in exposed IT…
Jeffrey Bowie, CEO of cybersecurity firm Veritaco, was arrested on April 14, 2025, facing two counts of violating Oklahoma’s Computer…
Jeffrey Bowie, the CEO of a local cybersecurity firm, has been arrested for allegedly planting malware on computers at SSM…
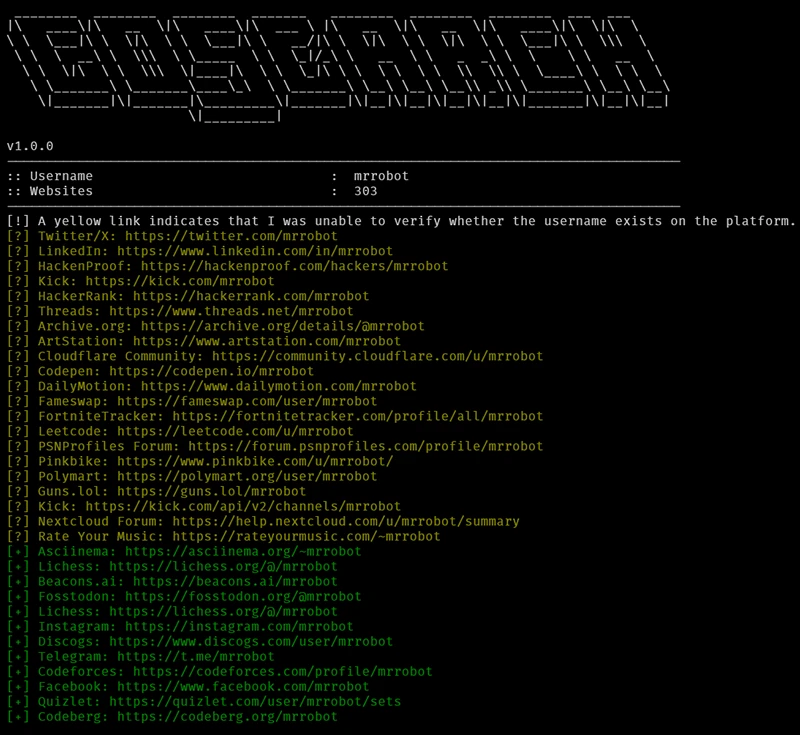
GoSearch is an open-source OSINT tool built to uncover digital footprints linked to specific usernames. Designed for speed and accuracy,…
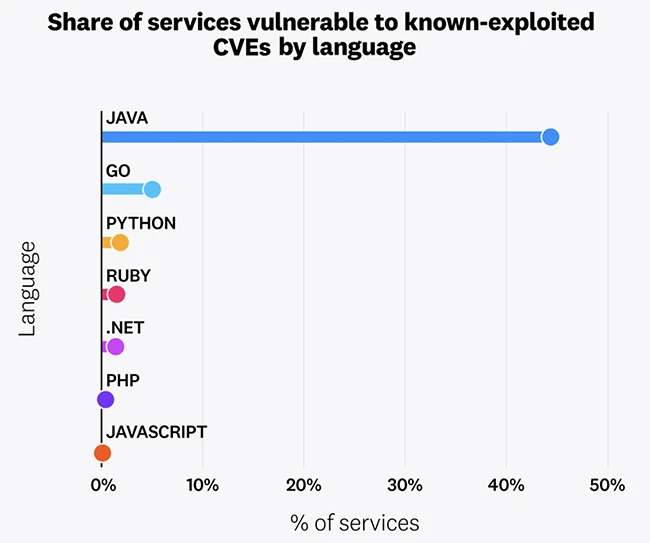
Web applications face a wide range of risks, including known-exploitable vulnerabilities, supply chain attacks, and insecure identity configurations in CI/CD,…
Shadow Servers have identified 454 SAP NetWeaver systems vulnerable to a critical zero-day vulnerability that has been actively exploited in…
A large-scale phishing campaign targets WooCommerce users with a fake security alert urging them to download a “critical patch” that adds a…
Melbourne Airport is building up its cyber detection and response capabilities in order to secure 30 million annual passenger journeys,…
The ransomware scene is re-organizing, with one gang known as DragonForce working to gather other operations under a cartel-like structure….
Brave has open-sourceed a new tool called “Cookiecrumbler,” which uses large language models (LLMs) to detect cookie consent notices and…