Author: Cybernoz
Citrix addressed NetScaler console privilege escalation flaw Pierluigi Paganini February 20, 2025 Citrix addressed a high-severity privilege escalation vulnerability impacting…
At the start of last August, Point de Contact told WIRED that only two images on four different Microsoft servers…
Since early 2024, ESET researchers have been tracking DeceptiveDevelopment, a series of malicious campaigns linked to North Korea-aligned operators. Disguising…
For decades, Microsoft Exchange has been the backbone of business communications, powering emailing, scheduling and collaboration for organizations worldwide. Whether…
Raymond Limited, a leading textile and apparel conglomerate, has confirmed a Raymond cyberattack that impacted parts of its IT infrastructure….
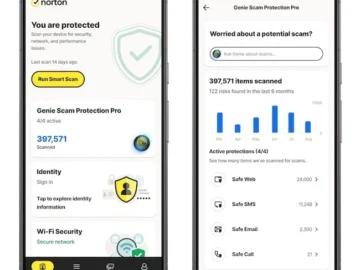
Norton is setting the standard for scam protection with a new range of AI-powered features fully integrated in Norton Cyber…
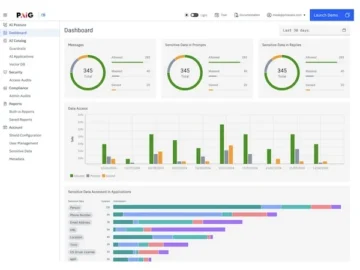
Privacera announced significant updates to its AI Governance (PAIG) platform, reinforcing its commitment to AI risk management and compliance. These…
A previously undocumented ransomware payload named NailaoLocker has been spotted in attacks targeting European healthcare organizations between June and October 2024….
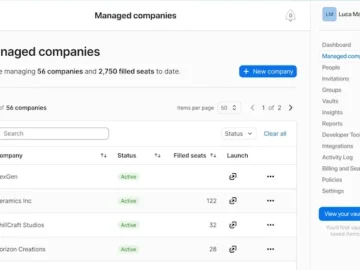
1Password introduced 1Password Enterprise Password Manager – MSP Edition, a dedicated solution that transforms how MSPs safeguard client data and…
Russian state-sponsored hackers are ramping up efforts to compromise Signal messenger accounts, particularly those used by Ukrainian military personnel, government…
Symantec, a division of Broadcom, has released a critical security update to address a high-severity vulnerability identified in its Symantec…
Palo Alto Networks warns that CVE-2025-0111 flaw is actively exploited in attacks Pierluigi Paganini February 20, 2025 Palo Alto Networks…