Author: Cybernoz
The national Dutch police (Politie) says that a state actor was likely behind the data breach it detected last week….
Dubai Silicon Oasis, United Arab Emirates, October 3rd, 2024, CyberNewsWire ANY.RUN has announced an upgrade to its Threat Intelligence Portal,…
The Threat Intelligence Market is experiencing exponential growth as organizations worldwide strive to protect their digital assets and defend against…
During a distributed denial-of-service campaign targeting organizations in the financial services, internet, and telecommunications sectors, volumetric attacks peaked at 3.8…
An exclusive live webinar will take place on October 4th at noon Eastern Time (ET), demonstrating how Criminal IP’s Attack…
Microsoft and the Justice Department have seized over 100 domains used by the Russian ColdRiver hacking group to target United…
At DEF CON 32, the SquareX research team delivered a hard-hitting presentation titled Sneaky Extensions: The MV3 Escape Artists where…
New Linux malware ‘Perfctl’ is targeting millions worldwide, mimicking system files to evade detection. This sophisticated malware compromises Linux servers,…
Oct 03, 2024Ravie LakshmananMobile Security / Technology Google has revealed the various security guardrails that have been incorporated into its…
Adobe Commerce and Magento online stores are being targeted in “CosmicSting” attacks at an alarming rate, with threat actors hacking approximately…
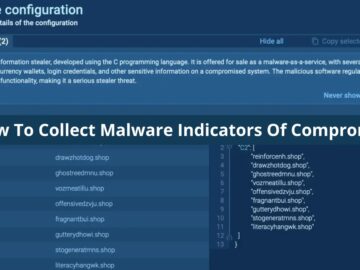
Indicators of Compromise (IOCs) are critical forensic artifacts that cybersecurity researchers use to “detect,” “investigate,” and “mitigate” security threats. As…
Decoding Compliance | What CISOs Need to Know Non-compliance can result in substantial financial penalties, with average fines reaching up…