Author: Cybernoz
Dublin in Ireland is the world’s third-largest hyperscale datacentre hub, according to a study by US-based analyst Synergy Research Group….
Google’s approach to cookies shouldn’t come as a surprise. It’s been delaying the elimination of cookies for quite some time….
Researchers have uncovered a network of at least 5,000 fake X (formerly Twitter) accounts that appear to be controlled by…
Microsoft has disabled a fix for a BitLocker security feature bypass vulnerability due to firmware incompatibility issues that were causing…
APT42 is an APT group that is believed to be backed by the Iranian government, and this group primarily focuses…
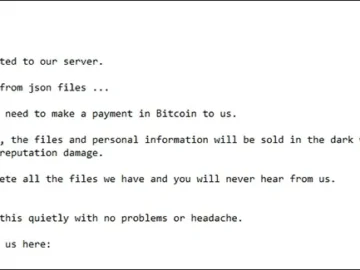
The Rhysida Ransomware gang, a notorious group known for their file-encrypting malware, has announced that they will be selling data…
Aug 15, 2024Ravie LakshmananEnterprise Security / Vulnerability SolarWinds has released patches to address a critical security vulnerability in its Web…
In 2006, Amazon Web Services (AWS), the first public cloud provider, offered publicly available services such as Elastic Computer Cloud…
NIST, an agency in the federal government of the United States (US), has finished its first draft of cryptographic algorithms…
Cybersecurity researchers have uncovered a sophisticated malspam campaign targeting unsuspecting users through email and phone calls. Attackers are leveraging popular…
In the final week of the Tour de France, cyclists endure grueling conditions of hills, heat, and pain over 21…
Cybercriminals are breaking into organizations’ cloud storage containers, exfiltrating their sensitive data and, in several cases, have been paid off…