Author: Cybernoz
Zloader, a sophisticated Zeus-based modular trojan that first emerged in 2015, has undergone a significant transformation from its original banking-focused…
The notorious Inc ransomware group has taken responsibility for an August 2025 data breach at the Pennsylvania Attorney General’s office….
Blackdot Solutions unveiled Videris Automate, a platform that delivers new AI capabilities to automate investigations and screening processes. The launch…
Your worst day can begin so innocuously – you leave home, you stop to pick up your coffee order, you…
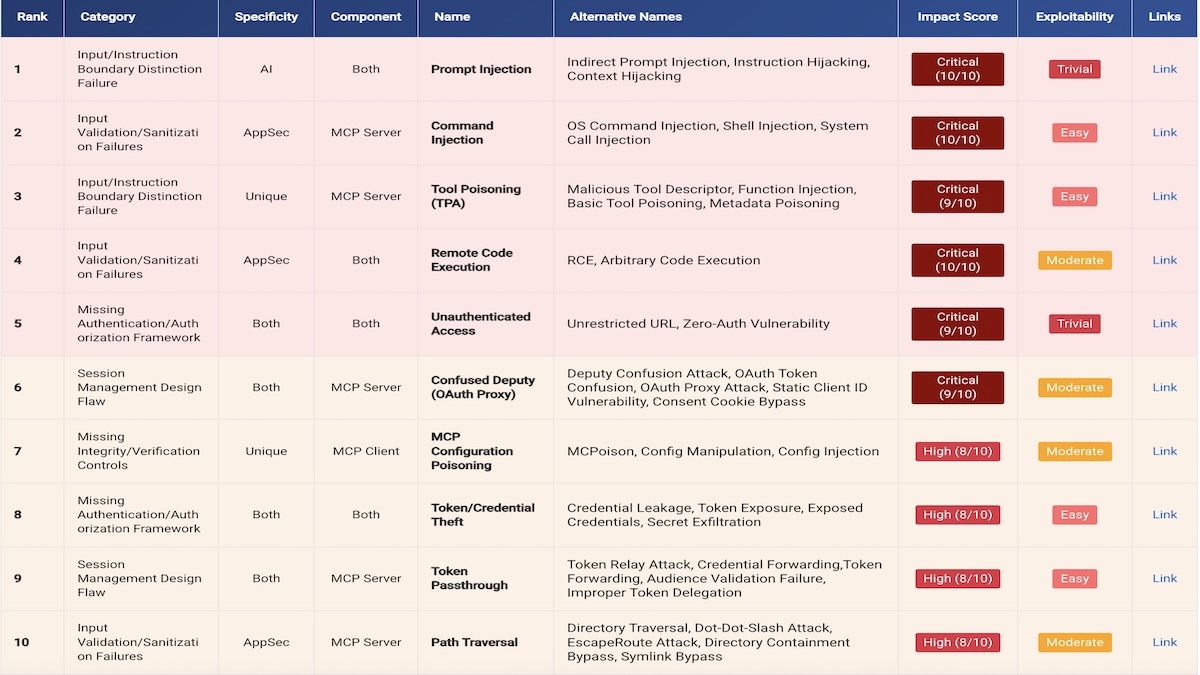
MCP has become an integral part of the expansion of agentic AI but comes with its own vulnerabilities. Model Context…
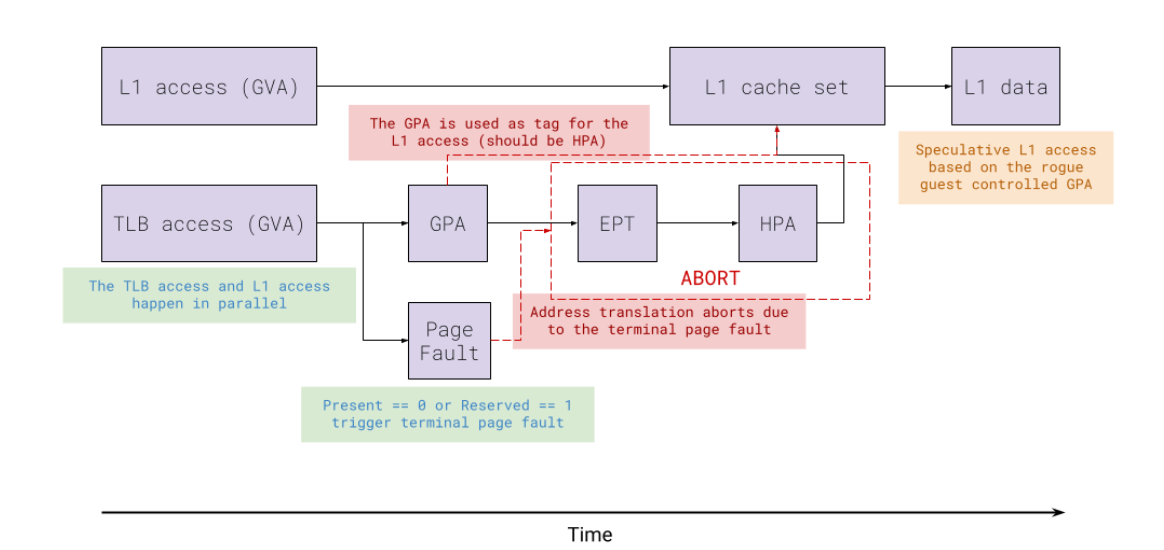
$150K awarded for L1TF Reloaded exploit that bypasses cloud mitigations Pierluigi Paganini September 23, 2025 Researchers earned $150K for “L1TF…
Newly discovered npm package ‘fezbox’ employs QR codes to retrieve cookie-stealing malware from the threat actor’s server. The package, masquerading as a…
Recent High-profile supply‐chain attacks have exposed critical weaknesses in package registry security, prompting GitHub to roll out a suite of…
These fake online speedtest applications prey on users seeking to measure their internet performance, yet they harbor hidden payloads that…
A sophisticated cyber campaign, dubbed “Operation Rewrite,” is actively hijacking Microsoft Internet Information Services (IIS) web servers to serve malicious…
In 2024, as the Russia-Ukraine war prolongs and military and economic cooperation between North Korea and Russia deepens, cyberspace has…
Every SOC leader understands that faster threat detection is better. But the difference between knowing it and building a system…