Author: Cybernoz
A revamped Department for Science, Innovation and Technology (DSIT) will transform public services and supercharge economic growth through science and…
Security researchers have discovered a new vulnerability in OpenSSH, identified as CVE-2024-6409, which could potentially allow remote code execution attacks on affected systems. This…
AI SPERA, a leading Cyber Threat Intelligence (CTI) company, has announced a partnership with UAE-based distributor Devcons to expand into…
A dark web hacker recently revealed a massive compilation of passwords dubbed in a file name “RockYou2024,” totaling 9,948,575,739 unique…
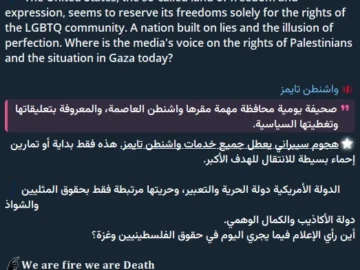
The Washington Times has allegedly become the latest victim of a cyberattack, with the hacker group SN Blackmeta claiming responsibility….
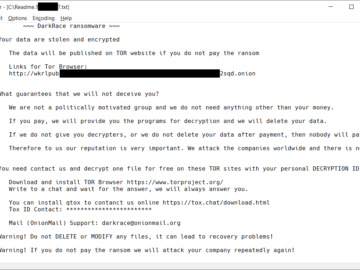
Avast released a decryptor for DoNex Ransomware and its predecessors Pierluigi Paganini July 09, 2024 Avast developed and released a…
A critical vulnerability has been discovered in the Ghostscript rendering platform, identified as CVE-2024-29510. This flaw, a format string vulnerability,…
Microsoft employees in China will be required to use iPhones, as the company plans to block Android devices from accessing…
Hackers often weaponize LNK files because they can carry malware into systems undetected by anyone. LNK files are shortcuts that,…
Jul 09, 2024NewsroomCyber Espionage / Threat Intelligence Cybersecurity agencies from Australia, Canada, Germany, Japan, New Zealand, South Korea, the U.K.,…
Excelsior Orthopaedics, a leading musculoskeletal healthcare center in New York, has been allegedly targeted by the notorious MONTI ransomware group….
A critical security vulnerability has been discovered in HCL Domino, a popular enterprise server software, that could potentially expose sensitive…