Cybercriminals now repurpose devices like Raspberry Pi into ‘plug-and-play’ weapons for digital fraud. With GEOBOX on the Dark Web, their capabilities are even more sophisticated, enabling manipulation of GPS, network simulation, Wi-Fi mimicry, and anti-fraud filter evasion.
Cybercriminals are targeting IoT devices for illicit activities through OPSEC techniques and customizable settings, allowing these devices to operate without logs and ensure anonymity for perpetrators, reveals research from the US-based cybersecurity solutions and services provider, Resecurity.
According to Resecurity’s Cyber Threat Intelligence team, a significant discovery has been made on the Dark Web: a malicious tool known as GEOBOX. This tool can turn ordinary IoT hardware into powerful weapons for cybercriminals. GEOBOX represents a “paradigm shift in cybercriminal tactics,” highlighting the evolving nature of threats in the digital landscape.
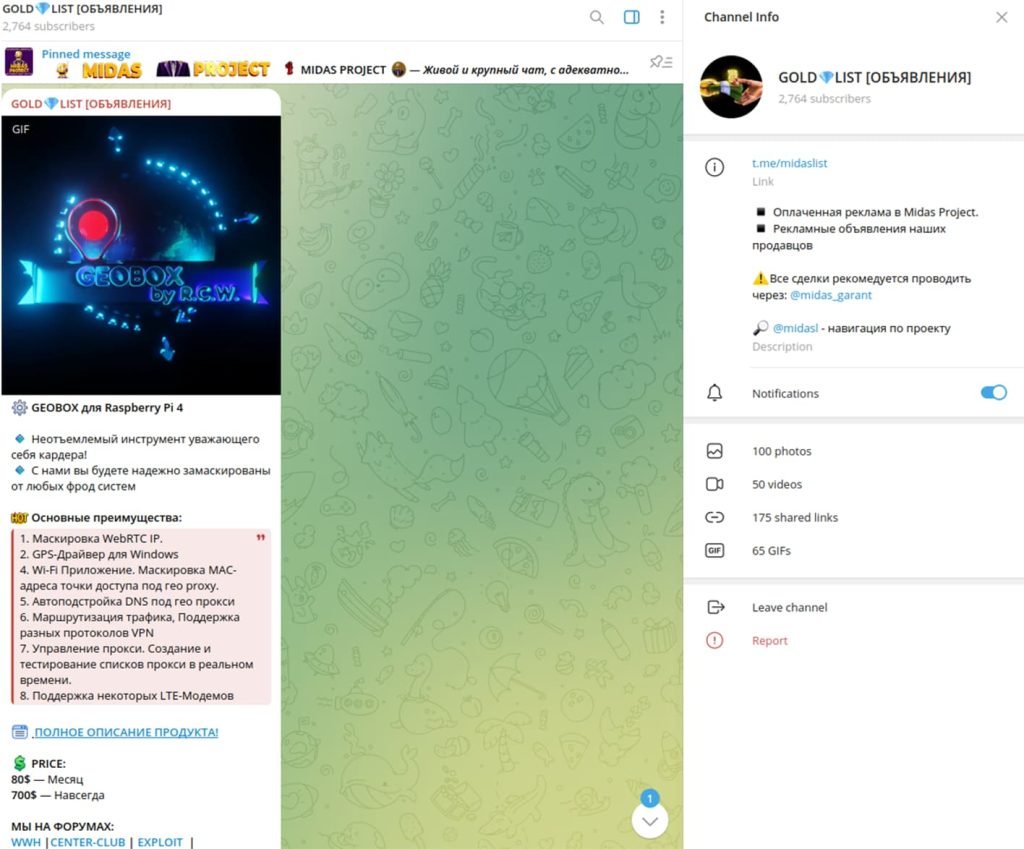
GEOBOX is a powerful, deceptive tool specifically designed for the Raspberry Pi 4 Model B devices to facilitate cybercriminals in anonymization and fraud. It was first discovered while investigating an online banking theft involving a high-net-worth (HNW) client of a Fortune 100 financial company, prompting researchers to dig deeper into its workings.
The emergence of GEOBOX is not unexpected, appearing shortly after the discovery of another dark web tool known as TMChecker. TMChecker has been arming ransomware gangs, specifically targeting the e-commerce and aviation industries with precision cyberattacks.
The research blog, shared by Resecurity with Hackread.com, ahead of publication on Monday revealed that threat actors have already used multiple internet-connected GEOBOX devices as proxies, each placed at a strategic remote location, enhancing their anonymity.
This complicated the investigation and tracking process, as GEOBOX devices do not store logs by default. Resecurity observed a bad actor using GEOBOX with two LTE-based wireless modems for enhanced anonymization, particularly in remote connections.
The package can be rented for a lifetime fee of $700 or a monthly rate of $80, payable in cryptocurrency and advertised on major underground forums and Telegram. The user manual provides clear instructions on the download and installation of the Raspberry Pi OS using Raspberry Pi Imager, how to obtain the GEOBOX Software Image and work with the GEOBOX software.
It is a feature-rich tool, including WebRTC IP for discreet online communication, GPS spoofing for geolocation manipulation, and the ability to mask Wi-Fi MAC addresses. The device requires at least 4 GB of RAM, but an 8 GB version is also available offering superior performance.
Further, it connects to the internet via Ethernet or USB modem and offers various tabs like INTERNETBOX, MIDDLEBOX, Proxy, VPN, and Wi-Fi, each providing specific functionalities. Users can configure various internet connection types, including VPN protocols like L2TP, PPTP, L2TP-IPsec, Wireguard, SSTP, Zerotier, and OpenVPN, and even create a VPN tunnel within another VPN tunnel.
GEOBOX can help threat actors in cyberattack coordination, dark web market operations, sophisticated financial frauds, circumvention of government censorship, anonymous malware distribution, credential stuffing campaigns, disinformation campaigns, surveillance evasion in authoritarian regimes, content piracy and geo-restriction bypassing, and network security testing.
That’s not all. Cybercriminals can also use GEOBOX to fake their geographical location using a GPS-like driver, bypassing location verification checks on websites like Whoer.net and browserleaks.com, and creating customized accounts on popular platforms like Google and Amazon.
The emergence of GEOBOX necessitates robust digital risk monitoring and endpoint protection strategies, making collaboration between law enforcement agencies, deployment of proactive measures, and continuous innovation in cybersecurity strategies fundamental to counter such threats effectively.
RELATED TOPICS
- Kaspersky’s iShutdown Tool Detects Pegasus Spyware
- New Dark Web Market Styx: Focuses on Money Laundering
- USB Wormable Raspberry Robin Malware Hits Windows PCs
- Building Your Defense Toolbox: Tools to Combat Cyber Threats
- Following WormGPT, FraudGPT Emerges for AI-Driven Cyber Crime