Author: Cybernoz
Jul 05, 2024The Hacker NewsCloud Security / Attack Surface The attack surface isn’t what it once was and it’s becoming…
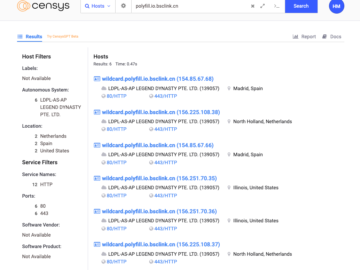
Polyfill.io Supply Chain Attack: 384,773 hosts still embedding a polyfill JS script linking to the malicious domain Pierluigi Paganini July 05,…
Hackers attack Microsoft Exchange servers because they often contain sensitive communication data that can be exploited for several illicit purposes….
Active since 2015, Mekotio is a Latin American banking trojan specifically designed to target financial data in regions like Brazil,…
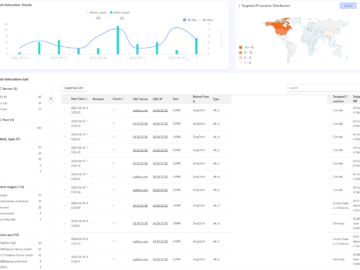
New Golang-based Zergeca Botnet appeared in the threat landscape Pierluigi Paganini July 05, 2024 Researchers uncovered a new Golang-based botnet…
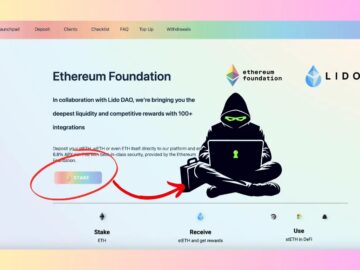
In a recent cyberattack, hackers successfully compromised Ethereum’s mailing list, attempting to drain users’ crypto funds through a sophisticated phishing…
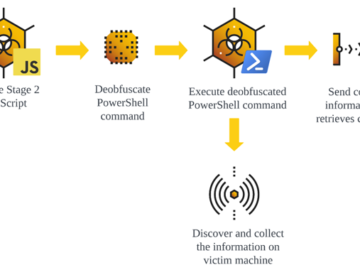
Jul 05, 2024NewsroomSEO Poisoning / Cyber Attack, The malware known as GootLoader continues to be in active use by threat…
Canonical has recently issued a series of crucial Ubuntu security updates aimed at addressing multiple vulnerabilities in Ghostscript, a widely…
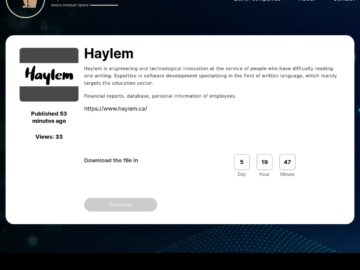
The notorious Space Bears ransomware group has allegedly targeted three prominent Canadian entities, compromising substantial volumes of sensitive data. The…
The LockBit ransomware group, infamous for its disruptive cyberattacks, is once again in the spotlight for allegedly carrying out a ransomware…
Microsoft discloses 2 flaws in Rockwell Automation PanelView Plus Pierluigi Paganini July 05, 2024 Microsoft discovered two flaws in Rockwell…
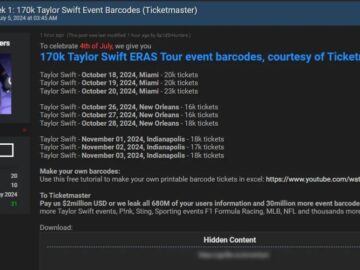
A cybercriminal group known as Sp1d3rHunters has allegedly leaked 170,000 valid barcodes for Taylor Swift ERAS Tour events. These barcodes,…