Author: Cybernoz
Modern advancements have tilted the world into a tightly-knit web. Accessing localized content and resources can be hard due to…
Mar 29, 2024The Hacker NewsPen Testing / Regulatory Compliance Network penetration testing plays a vital role in detecting vulnerabilities that…
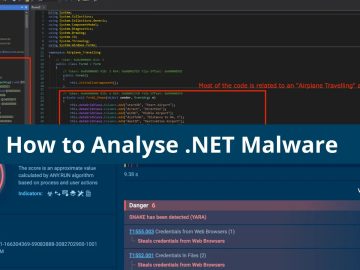
Utilizing sandbox analysis for behavioral, network, and process examination provides a foundation for reverse engineering .NET malware. The write-up outlines…
American fast-fashion firm Hot Topic hit by credential stuffing attacks Pierluigi Paganini March 29, 2024 Hot Topic suffered credential stuffing attacks that…
A comprehensive survey conducted by Keeper Security, in partnership with TrendCandy Research, has shed light on the growing concerns within…
In recent years, the world has witnessed a concerning uptick in cyber kidnappings, with individuals, organizations, and even governments falling…
Companies demonstrating advanced cybersecurity performance generate a shareholder return that is 372% higher than their peers with basic cybersecurity performance,…
By Shrikant Navelkar, Director, Clover Infotech Due to the significant advancements in the IT industry, the adoption of cloud computing…
Splunk Inc. has disclosed two significant vulnerabilities within its software suite, posing a considerable risk to organizations utilizing Splunk Enterprise…
Though generative AI offers financial firms remarkable business and cybersecurity utility, cyberthreats relating to GenAI in financial services are a…
Mar 29, 2024NewsroomSupply Chain Attack / Threat Intelligence The maintainers of the Python Package Index (PyPI) repository briefly suspended new…
Enterprises spend enormous effort fixing software vulnerabilities that make their way into their publicly-facing applications. The Consortium for Information and…