Author: Cybernoz
Researchers at the University of Surrey have developed software that can assess the amount of data that an artificial intelligence…
TikTok has been fined by a UK data protection watchdog after its investigation shows the company failed to get parental…
Hacking with OpenAI GPT-3 | Hacking Without Humans Source link
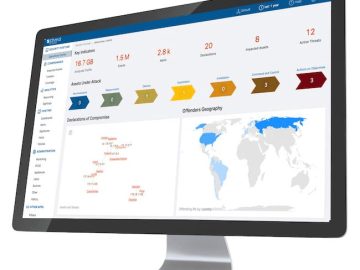
Stamus Networks released its latest software release, Update 39 (U39). The new release represents a significant enhancement to the company’s…
Google has released an Android update that fixes two critical remote code execution (RCE) vulnerabilities, and one vulnerability that has…
The State Library of Victoria. State Library of Victoria The State Library of Victoria (SLV) is looking to fill a…
Broken Access Control – Lab #10 User ID controlled by param with password disclosure | Long Version Source link
Our “Endpoint Security Evaluation Guide” eBook helps you choose the right endpoint security solution. Endpoint security has never been more…
What are Executables? | bin 0x00 Source link
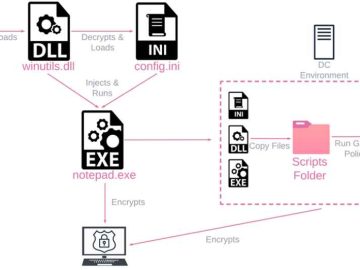
Researchers at the Israeli cybersecurity firm Check Point have given the new ransomware the name “Rorschach.” They said that their…
Description For a recent need I wish to make a return on the implementation of the binary search in Go…
The developers of the Typhon info-stealer announced on a dark web forum that they have updated the malware to a…